LDAP Nom Nom
Anonymously bruteforce Active Directory usernames from Domain Controllers by abusing LDAP Ping requests (cLDAP)
Looks for enabled normal user accounts. No Windows audit logs were generated. High-speed ~ up to 10K/sec – go beyond 25K/sec with multiple servers!
- Tries to autodetect DC from environment variables on domain joined machines or falls back to machine hostname FQDN DNS suffix
- Reads usernames to test from stdin (default) or file
- Outputs to stdout (default) or file
- Parallelized, multiple connections to multiple servers (defaults to 8 servers, 8 connections per server)
- Shows a progressbar if you’re using both input and output files
- Evasive maneuvers: Use –throttle 20 for a 20ms delay between each request (slows everything down to a crawl)
- Evasive maneuvers: Use –maxrequests 1000 to close the connection and reconnect after 1000 requests in each connection (try to avoid detection based on traffic volume)
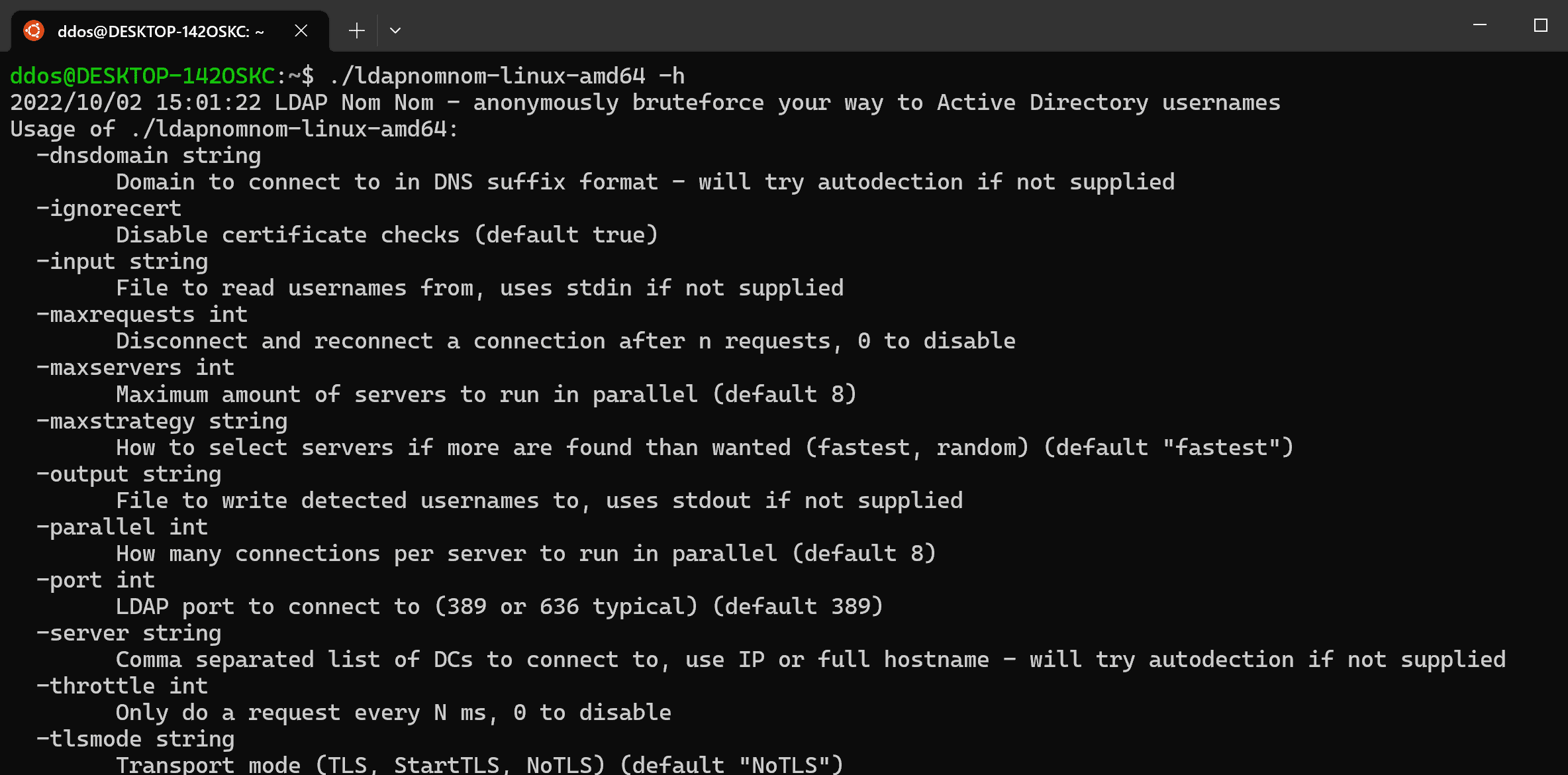
Use

Examples
Connect to up to 32 servers from contoso.local with 16 connections to each – FAAAAAAAST
ldapnomnom –input 10m_usernames.txt –output multiservers.txt –dnsdomain contoso.local –maxservers 32 –parallel 16
Connect to one named server with 4 connections
ldapnomnom –input 10m_usernames.txt –output results.txt –server 192.168.0.11 –parallel 4
Look for username lists to feed into this elsewhere – for instance, the 10M list from here
Detection
- No Windows event logs are generated (tested on Windows 2016 / 2019)
- Requires custom network-level monitoring (unencrypted LDAP analysis or traffic volume for LDAPS)
Mitigation
- None, this is part of the dcLocator stuff
- Rename your administrator account
- Audit accounts for having the same password as the username
- Prevent kerberoasting by removing SPNs on as many accounts as possible
- Use long and complex passwords on accounts with SPNs
Changelog v1.3
- 680e316: Minor module upgrade (Lars Karlslund)
- 5792223: Updated readme to mention that Microsoft Defender for Identity now detects this based on bad guess count (Lars Karlslund)
- cf250d1: Time for that ASCII art logo (Lars Karlslund)
- c578678: Update GitHub actions and build script (Lars Karlslund)
- 2c9c4a0: Obfuscated builds (Lars Karlslund)
- ff52afc: Build fix (Lars Karlslund)
- c6f0fc1: Build fix take two (Lars Karlslund)
- 76e7177: Another build fix (Lars Karlslund)
- f06417a: Build update (Lars Karlslund)
- a7ce063: Typo (Lars Karlslund)
- 6dbe9fe: Also literals (Lars Karlslund)
Install
Copyright (c) 2022 Lars Karlslund