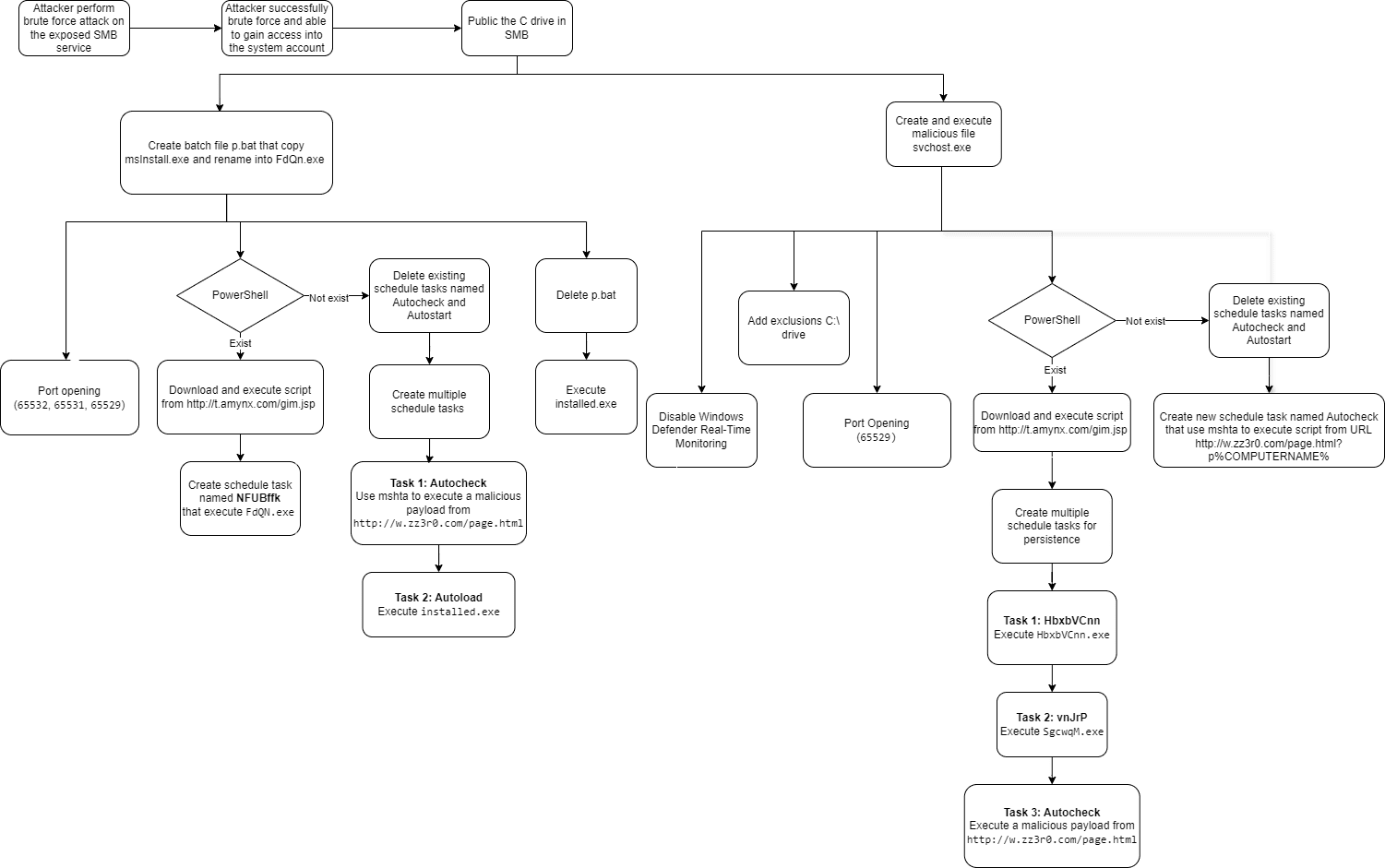
Graph flow of the attack
A recent report from security researchers at Aufa and NetbyteSEC Interns sheds light on the resurgence of the LemonDuck malware, which is now exploiting the EternalBlue vulnerability (CVE-2017-0144) in Microsoft’s Server Message Block (SMB) protocol to facilitate cryptomining attacks. EternalBlue, a notorious exploit, was first leveraged by the infamous WannaCry ransomware, and it remains a critical entry point for malware like LemonDuck, which targets network resources to mine cryptocurrency while evading detection.
LemonDuck, identified as a sophisticated cryptomining malware, uses several attack vectors, including phishing emails, brute-force password attacks, and SMB exploits. Once it gains access to a vulnerable system, it establishes control and utilizes the machine’s processing power for cryptomining. “LemonDuck employs PowerShell to avoid detection, deploy various malicious payloads, and target systems for cryptojacking,” researchers noted.
The attack starts with a brute-force attack on SMB services, exploiting the EternalBlue vulnerability to gain unauthorized access. In a case study from the report, the researchers revealed that the attacker, originating from an IP in Taichung City, Taiwan, successfully compromised an SMB service, granting them administrative access. According to the report, “the attacker creates a hidden administrative share for the C: drive, enabling remote access without the victim’s knowledge.”
Once the attacker has access, they use a batch file, p.bat, to initiate a series of malicious actions. These include copying a malicious file (msInstall.exe), renaming it, and setting up firewall rules to reroute traffic to remote servers. The report states, “The batch file also executes a base64-encoded PowerShell script to download additional malware from remote URLs and schedules tasks to ensure persistent execution.”
LemonDuck’s primary goal is to leverage system resources for cryptomining. To achieve this, the malware uses various techniques to maintain persistence and avoid detection. One such method involves disabling Windows Defender real-time protection and adding the entire C: drive to the exclusion list, ensuring that security software overlooks malicious activities. The report highlights, “This malware was able to disable Windows Defender’s real-time protection and create exclusions for the entire C: drive and the PowerShell process to avoid detection.”
The malware also manipulates network settings, opening TCP ports (65532, 65531, 65529) under DNS-related rules and using port proxies to disguise outbound traffic as legitimate DNS requests. This allows the malware to communicate with its command-and-control (C2) servers and exfiltrate data without raising red flags in typical network monitoring systems.
The report provides several indicators of compromise (IOCs) associated with LemonDuck, including IP addresses, URLs, and malicious executables. One of the key URLs flagged in the attack is http://t.amynx.com/gim.jsp, which is used to download additional malware payloads. VirusTotal has marked this URL as malicious, linking it to cryptomining activities.
To mitigate these attacks, organizations are urged to patch their systems against known vulnerabilities, especially EternalBlue (CVE-2017-0144). Regularly updating software and using advanced security solutions that can detect lateral movements in networks are essential in preventing malware like LemonDuck from gaining a foothold.
The LemonDuck malware continues to evolve, employing a mix of brute-force SMB exploits, cryptomining payloads, and advanced evasion techniques to compromise vulnerable systems. As the report notes, “It is crucial for organizations to ensure that all operating systems and software are regularly updated to protect against known vulnerabilities, including EternalBlue (CVE-2017-0144) to minimize the risk from being compromised.”
Related Posts:
- Imperva found RedisWannaMine cryptojacking attack that uses EternalBlue vulnerability to infect servers
- Cryptojacking Campaign Exploits Atlassian Confluence CVE-2023-22527 Vulnerability
- Log4j Campaign Exploited to Deploy XMRig Cryptominer
- Hackers are actively exploiting PHP RCE vulnerability (CVE-2024-4577)