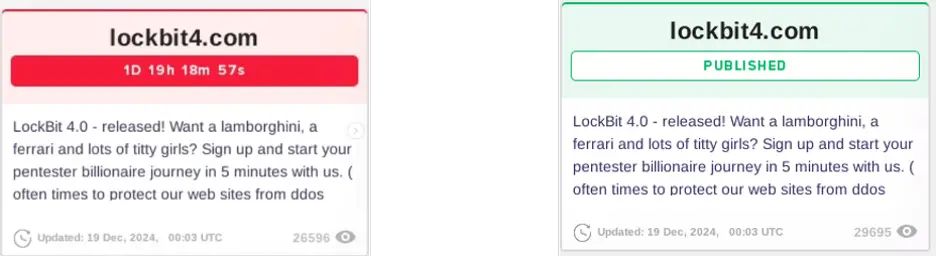
The pre-release and release notifications for LockBit 4.0 | Image: Deep Instinct
LockBit has been a major player in the ransomware world since 2019, known for its sophisticated tactics and significant impact on organizations across various industries. The group operates under a Ransomware-as-a-Service (RaaS) model, supplying its LockBit malware to affiliates who execute attacks and share a portion of the ransom with the LockBit group.
The latest version, LockBit 4.0, was officially released on February 3, 2025, following an announcement on December 19, 2024, that marked the end of the LockBit 3.0 era. This new release has brought several changes, but the core threat remains potent.
Deep Instinct’s report highlights a mix of new features and some surprising regressions in LockBit 4.0. While it introduces enhanced evasion capabilities, it also takes some steps back from its predecessor.
- Simpler Packer: Unlike LockBit 3.0, which used a unique password-protected packer for each version, LockBit 4.0 employs a simpler, non-password-protected UPX packer. This makes unpacking easier for analysis.
- Quiet Mode: A new “quiet mode” allows attackers to operate more stealthily by keeping file extensions and modification dates unchanged and omitting ransom notes. This feature makes attacks harder to detect and investigate.
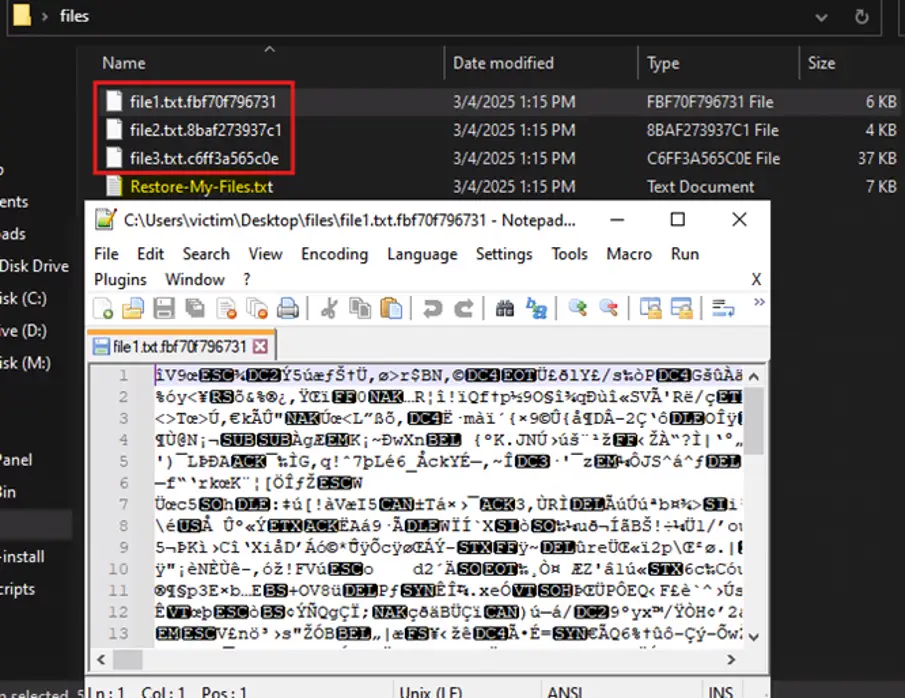
- Ransom Note and File Changes: The ransom note has subtle changes, and unlike LockBit 3.0, the new version doesn’t change the icons of encrypted files. Instead, it appends a random 12-character hash to the file extension.
- Encryption Method and Speed: Both versions use partial encryption, but LockBit 4.0 allocates memory for 9% of the file’s size in each cycle. However, LockBit 3.0 encrypts files faster; where LockBit 4.0 takes about 25 seconds to encrypt 1,000 files, LockBit 3.0 does it in approximately 5 seconds.
- Dynamic API Resolution and DLL Loading: LockBit 4.0 uses the same dynamic method as 3.0 to discover functions but employs proxy DLL loading to evade Event Tracing for Windows Telemetry Infrastructure (ETWTI), a technique that helps it avoid detection by security products.
- DLL Unhooking: LockBit 4.0 implements DLL Unhooking to bypass security product hooks by remapping a DLL into memory, making it harder for security solutions to detect the malware.
- Vectored Exception Handler (VEH) Removal: The malware removes its own VEHs to avoid detection and hinder analysis or debugging.
- Disabling DLL Loading Notifications: LockBit 4.0 prevents endpoint detection products from receiving alerts about newly loaded DLLs by blocking callbacks registered with LdrRegisterDllNotification.
- Self-Deletion: Both versions delete themselves from the disk, but LockBit 4.0 does not touch the Recycle Bin, unlike LockBit 3.0.
LockBit 4.0 introduces new evasion techniques but also retains many characteristics of its predecessor. While some changes may seem like steps backward, the overall threat remains significant. Organizations must stay vigilant and proactive in their cybersecurity measures to defend against this continuously evolving ransomware.
Related Posts:
- Cyberattackers Unleash LockBit Ransomware Using Cobalt Strike and Proxy Tools
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities
- LockBit Ransomware: The Hidden Threat in Resume Word Files
- LockBit Imposter: New Ransomware Leverages AWS for Attacks
- From Confluence Vulnerability (CVE-2023-22527) to LockBit Encryption: A Rapid Attack Chain