
Researchers at Rapid7 have uncovered a fresh campaign using LodaRAT, a well-known remote access tool (RAT) that has been active since 2016. Initially developed for information gathering, LodaRAT has been used in cyber-espionage and data theft, but the latest campaign reveals an alarming expansion in both distribution and capabilities, making it a global threat.
The latest variant of LodaRAT has expanded its reach, targeting cookies and credentials from Microsoft Edge and Brave browsers. Rapid7 highlighted, “While new malware families pop up all the time with fancy updates, LodaRAT has stayed mostly the same since 2021, yet it’s still spreading and infecting systems worldwide”. The simplicity of its core design allows attackers to maintain its effectiveness without major modifications.
LodaRAT’s persistent capabilities have made it a significant threat. It is delivered via phishing emails, vulnerability exploitation, and more recently, through DonutLoader and CobaltStrike, both of which are known for evading detection.
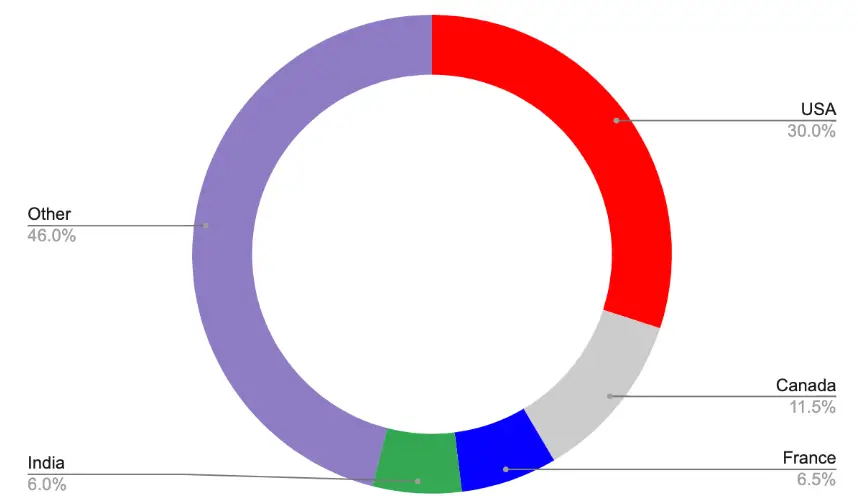
The malware is now masquerading as popular applications like Discord, Skype, and Windows Update to trick users into downloading it. Unlike previous campaigns, which were regionally focused, this iteration is indiscriminate, infecting victims globally. Rapid7 observed that around 30% of VirusTotal samples were uploaded from the USA.
Once installed, LodaRAT establishes persistence by modifying the system registry or creating a scheduled task. This version of LodaRAT introduces the ability to steal credentials from modern web browsers and perform actions such as:
- Screen capturing and saving images in a hidden directory to evade detection
- Microphone and webcam recording, with captured media exfiltrated to the command-and-control (C2) server
- New user account creation and disabling of Windows Firewall
- Lateral movement capabilities that leverage the SMB protocol to infect other systems within the network
Rapid7 found that the malware “attempts to connect to an internal IP on port 445” to spread to other devices, showcasing an increase in its potential to compromise organizational networks. Rapid7 warned, “The recent campaign… proves that small tweaks can keep malware effective without major updates”.
To combat this threat, Rapid7 advises implementing robust detection coverage across all endpoints and recommends using their Insight Agent to monitor and alert on suspicious processes. Security teams should also stay vigilant for LodaRAT’s indicators of compromise (IOCs) and employ strong authentication and cybersecurity measures to reduce the risk of credential theft.
Related Posts:
- Kimsuky APT: New TTPs Revealed in Rapid7 Cybersecurity Report
- Cybercriminals Evolve Social Engineering Tactics, Exploit CVE-2022-26923 in Sophisticated Campaign
- CVE-2024-38094 Exploited: Attackers Gain Domain Access via Microsoft SharePoint Server
- Sophisticated Social Engineering Campaign Linked to Black Basta Ransomware