log4j-detector
Detects Log4J versions on your file system within any application that are vulnerable to CVE-2021-44228 and CVE-2021-45046. It is able to even find instances that are hidden several layers deep. Works on Linux, Windows, and Mac, and everywhere else Java runs, too!
Currently reports log4j-core versions 2.3.1, 2.12.3, and 2.17.0 as _SAFE_, 2.12.2, 2.15.0 and 2.16.0 as _OKAY_ and all other versions as _VULNERABLE_ (although it does report pre-2.0-beta9 as _POTENTIALLY_SAFE_). It reports older log4j-1.x versions as _OLD_.
Can correctly detect log4j inside executable spring-boot jars/wars, dependencies blended into uber jars, shaded jars, and even exploded jar files just sitting uncompressed on the file-system (aka *.class).
We currently maintain a collection of log4j-samples we use for testing.

How Does It Work?
The Java compiler stores String literals directly in the compiled *.class files. If log4j-detector detects a file named “JndiManager.class” on your file system, it then examines that file for this String: “Invalid JNDI URI – {}”. Turns out that specific String literal is only present in the patched version of Log4J (version 2.15.0). Any versions of Log4J without that String are vulnerable.
What About Log4J 1.2.x?
Only versions of Log4J 2.x (from 2.0-beta9 to 2.14.1) are vulnerable to CVE-2021-44228.
How Can I Be Sure This Isn’t A Trojan Pretending To Be A Log4J Detector?
Great question! Since we include the complete source code here in Github (all 750 lines of Java), as well as the steps to build it, and since this tool has zero dependencies, it shouldn’t take too long to carefully study the code to your satisfaction. If you don’t trust Maven you can go directly into the “src/main/java/com/mergebase/log4j” directory and type “javac *.java”. That works, too!
Understanding The Results
_VULNERABLE_ -> You need to upgrade or remove this file.
_OKAY_ -> We only report this for Log4J versions 2.15.0 and 2.16.0. We recommend upgrading to 2.17.0.
_SAFE_ -> We currently only report this for Log4J versions 2.17.0 and 2.12.2.
_OLD_ -> You are safe from CVE-2021-44228, but should plan to upgrade because Log4J 1.2.x has been EOL for 7 years and has several known vulnerabilities.
_POTENTIALLY_SAFE_ -> The “JndiLookup.class” file is not present, either because your version of Log4J is very old (pre-2.0-beta9), or because someone already removed this file. Make sure it was someone in your team or company that removed the “JndiLookup.class” if that’s the case because attackers have been known to remove this file themselves to prevent additional competing attackers from gaining access to compromised systems.
This Scanner Only report Hits Against The log4j-core Library. What About log4j-api?
Many scanners (including GitHub’s own Dependabot) currently report both “log4j-core” and “log4j-api” libraries as vulnerable. These scanners are incorrect. There is currently no existing version of the “log4j-api” library that can be exploited by any of these vulnerabilities.
Why Report About 2.10.0, 2.15.0, 2.16.0, and 2.17.0 ?
We consider version 2.10.0 important because that’s the first version where Log4J’s vulnerable “message lookup feature” can be disabled via Log4J configuration.
We consider versions 2.15.0 and 2.16.0 important because these are the first versions where Log4J’s default out-of-the-box configuration is not vulnerable to CVE-2021-44228.
And version 2.17.0 is important because it’s not vulnerable to CVE-2021-45046. Despite CVE-2021-45046 being much less serious, we anticipate everyone will want to patch to 2.17.0.
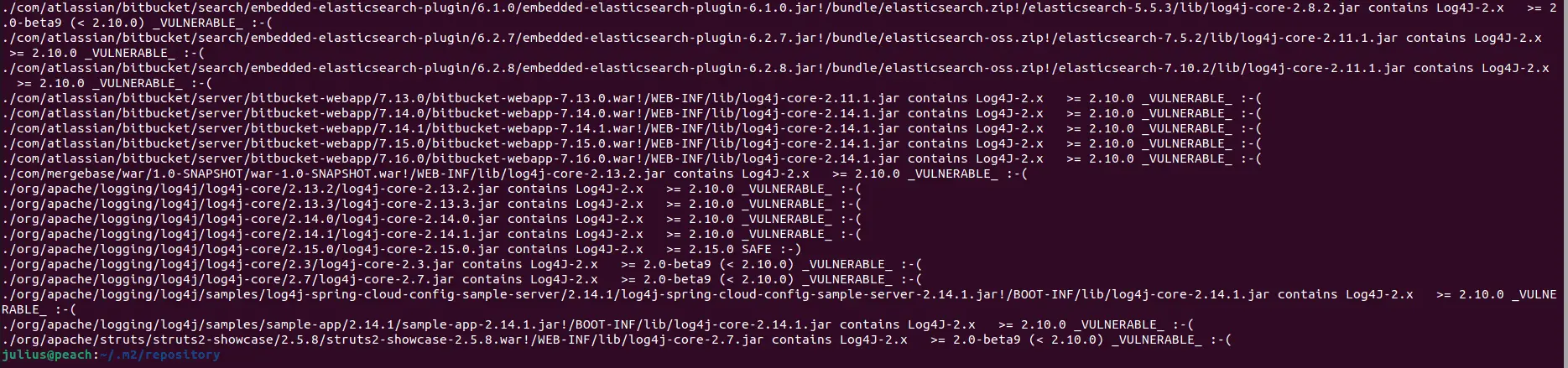
What are those “file1.war!/path/to/file2.zip!/path/to/file3.jar!/path/to/log4j.jar” results about?
The “!” means the log4j-detector entered a zip archive (e.g., *.zip, *.ear, *.war, *.aar, *.jar). Since zip files can contain zip files, a single result might contain more than one “!” indicator in its result.
Note: the log4j-detector only recursively enters zip archives. It does not enter tar or gz or bz2, etc. The main reason is that Java systems are often configured to execute jars inside jars, but they are never configured to execute other file formats (that I know of!). And so a log4j copy inside a *.tar.gz is probably not reachable for a running Java system, and hence, not a vulnerability worth reporting.
2nd note: for zips-inside-zips our scanner does load the inner-zip completely into memory (using ByteArrayInputStream) before attempting to scan it. You might need to give Java some extra memory if you have extremely large inner-zips on your system (e.g., 1 GB or larger).
Changelog v2021.12.29
- Ability to detect log4j-core-2.3.2.jar, log4j-core-2.12.4.jar, and log4j-core-2.17.1.jar (all are _SAFE_).
Download & Use
Copyright (c) 2021 – MergeBase Software Inc