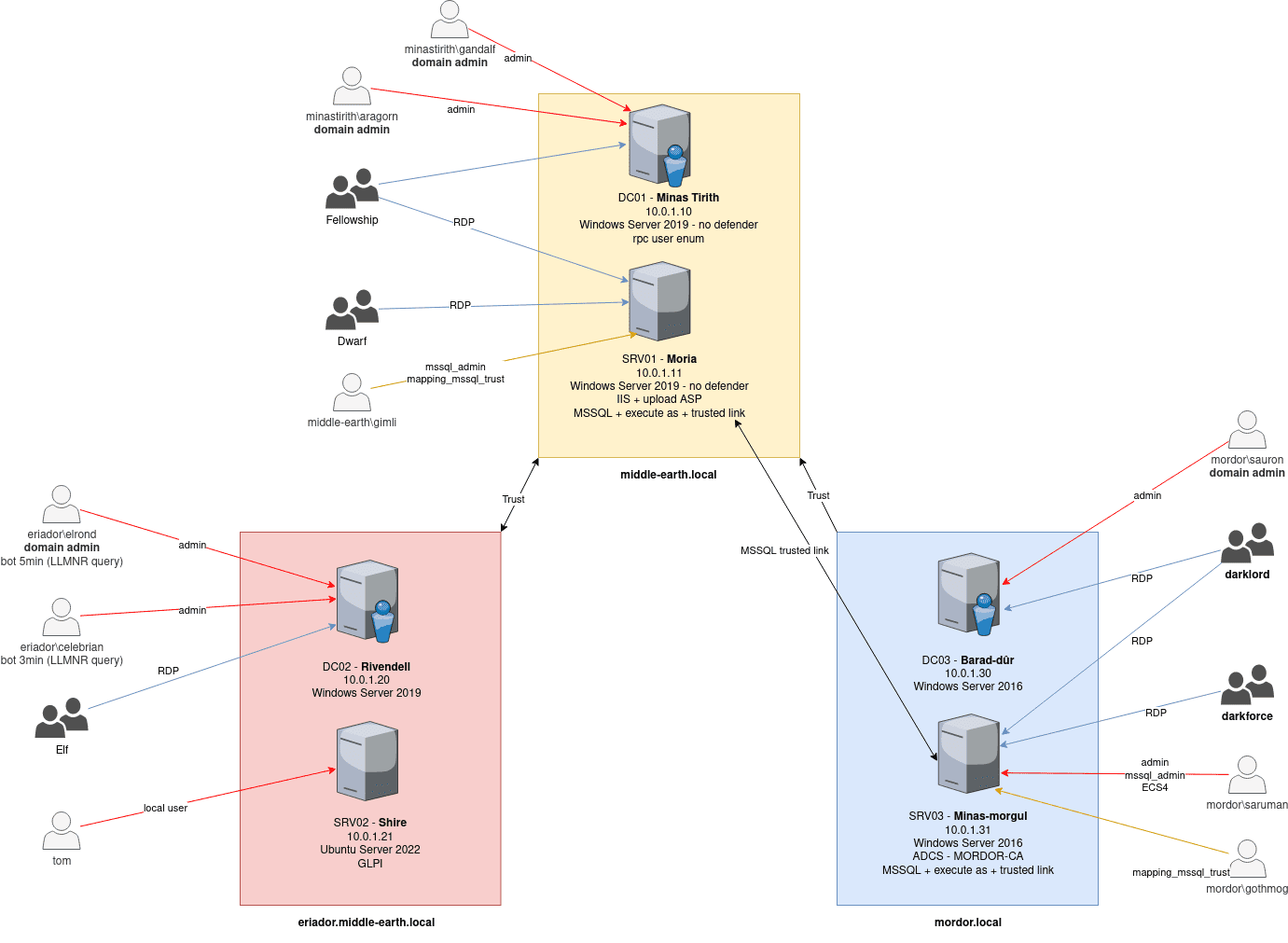
LOAD – Lord Of Active Directory
Based on AWS-Redteam-Lab and OCD GOAD
The price for running the lab for 125 hours during one month is approximately 14$. With Free Tier you get 750h of EC2 per month, there are 6 machines so 125h. But you only get 30 GB of storage. So you need storage for the other 5 VMs: 30Gb * 5 = 150Gb = 14$ / month.
Vulnerabilities

LINUX
SHIRE (srv02)
– GLPI SQLi
– GLPI-htmlawed-CVE-2022-35914
USERS
– privesc user with vulnerable crontab
– privesc root with password in bash_history and sudo nopasswd for /bin/systemctl
ERIADOR.MIDDLE-EARTH.LOCAL
RIVENDELL (dc02)
– anonymous RPC (enum users, pass pol, groups / rpcclient)
– brute force users names
ELF
– celebrian Responder crack hash (bot 3min)
– elrond: Responder with NTLM relay domain admin (bot 5min)
HOBBIT
– bilbo: password in description
– pippin: ASREPROAST
– merry: Constrained delegation with protocol transition / Kerberoasting
– froddo:
– sam:
MIDDLE-EARTH.LOCAL
MINAS-TIRITH(dc01)
– Open share RW, LNK exploit
– khamul.easterling : Open backup share, with GPO with cpassword, password increment
MORIA (srv01)
– MSSQL trusted link : donPapi to get sql_svc password
– mitm6 SRV01 -> DC01
MEN
– denethor: DOMAIN ADMIN
– theoden: ACL self-self-membership-on-group DOMAIN ADMIN
– faramir: ACL genericwrite-on-user Denethor
– boromir: ACL genericall-on-user Denethor
ACL forcechangepassword on Faramir
WriteDACL MEN
FELLOWSHIP
– legolas: execute as user on MSSQL
KERBEROASTING
– gimli: ACL genericall-on-computer MORIA
ACL writeproperty-self-membership DOMAIN ADMIN
– aragorn: execute as login on mssql / administrator
– gandalf: mssql admin
group cross domain
mssql trusted link
ACL writeproperty-self-membership Domain Admins #TODO change for someone who is not administrator, he has DCSYNC (administrator?)
ENTS
– treebeard: ACL writeproperty-on-group DOMAIN ADMIN
– skinbark: ACL genericall-on-group DOMAIN ADMIN
– ginglas: ACL write owner on group DOMAIN ADMIN
MORDOR.LOCAL
Computers
BARAD-DUR (dc03)
– Coerced DC + ntlmrelayx to ldaps
– ADCS ESC1, ESC2, ESC3, ESC4, ESC8
– NTLM downgrade attack
MINAS-MORGL (srv03)
– IIS upload webshell
– Privilege escalation Windows 2016 : SeImpersontePrivilege
DARKFORCE
– sauron: domain admin MORDOR
– saruman: mssql admin / GenericAll on gothmog (shadow credentials) / GenericAll on ECS4
– balrog:
PRISONER
– gollum: mssql trusted link
password spray -> user=pwd
ORC
– gothmog: DOMAIN ADMIN
– lurtz:
– ugluk:
– guritz:
NAZGUL
– angmar:
Install
Copyright (C) 2023 hilarex