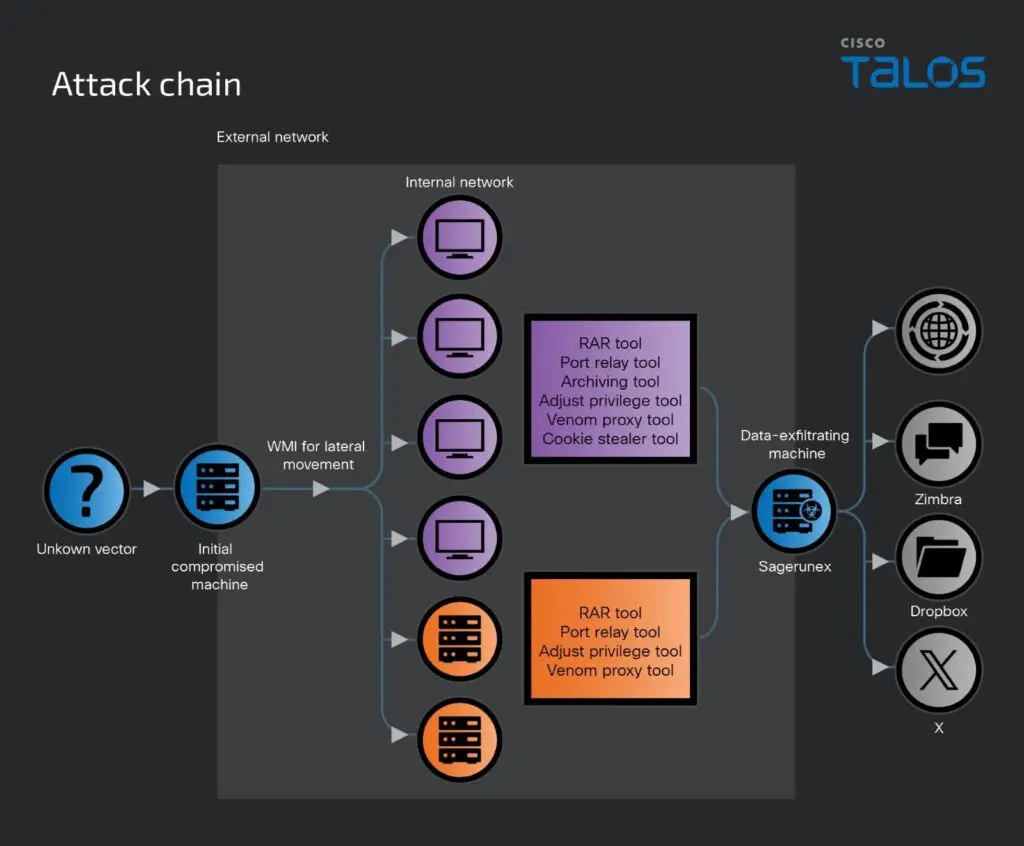
Attack Chain | Image: Cisco Talos
A sophisticated cyber espionage operation linked to the Lotus Blossom group has been discovered targeting government, manufacturing, telecommunications, and media sectors across Southeast Asia. According to Cisco Talos researchers, this state-backed group has been active since at least 2012 and has continued its operations using the Sagerunex backdoor, an advanced Remote Access Trojan (RAT) exclusively associated with Lotus Blossom.
Cisco Talos researchers identified multiple espionage campaigns utilizing different variants of the Sagerunex backdoor. These operations appear highly persistent and demonstrate a strong focus on intelligence gathering.
“Talos attributes these attacks to the threat actor known as Lotus Blossom. Lotus Blossom has actively conducted cyber espionage operations since at least 2012 and continues to operate today,” the report explains.
The primary objectives of these campaigns include long-term network infiltration, sensitive data exfiltration, and persistent surveillance of high-profile targets in the Philippines, Vietnam, Hong Kong, and Taiwan.
Sagerunex, a DLL-based RAT, has been deployed in various campaigns since 2016. This malware allows attackers to:
- Gain persistence via system registry modifications.
- Execute remote commands and steal files.
- Exfiltrate credentials from compromised systems.
- Leverage third-party cloud services for C2 communications.
“Our investigation uncovered two new variants of the Sagerunex backdoor, which were detected during attacks on telecommunications and media companies,” the report writes.
Unlike earlier versions that relied on Virtual Private Servers (VPS) for Command and Control (C2) communication, newer Sagerunex variants now use third-party cloud services, including:
- Dropbox
- Twitter API
- Zimbra Open-Source Webmail
This shift in tactics enables Lotus Blossom to evade traditional network-based security detections, making their operations harder to track.
Cisco Talos researchers identified several hacking tools used alongside Sagerunex to achieve their espionage objectives:
- Cookie Stealer Tool – A PyInstaller bundle that extracts stored Chrome browser credentials.
- Venom Proxy Tool – A modified penetration testing proxy, hardcoded with destination IP addresses.
- Privilege Escalation Tool – Used to gain higher privileges on compromised systems.
- Custom Archiving Tool – Compresses and encrypts stolen data.
- Port Relay Tool – Allows connection relays for deeper infiltration into networks.
These tools allow the Lotus Blossom group to exfiltrate sensitive government and enterprise data without raising alarms.
Lotus Blossom is known for its ability to maintain access within compromised networks for extended periods. The group frequently uses Impacket for executing remote commands, a technique consistent with previously observed Lotus Blossom tactics.
Researchers describe their persistence strategy: “Lotus Blossom frequently utilizes the Impacket tool to execute remote processes and commands within the victim’s environment, consistent with known Lotus Blossom TTPs.”
Once inside a system, the attackers execute reconnaissance commands such as:
- netstat, tasklist, quser, ipconfig (to analyze system activity)
- dir, net, whoami (to identify system directories and user accounts)
To maintain persistence, Sagerunex is embedded into the Windows system registry, allowing the malware to execute at system startup.
“We also observed Lotus Blossom gain persistence using specific commands to install their Sagerunex backdoor within the system registry and configuring it to run as a service on infected endpoints,” the report highlights.
Related Posts:
- AVrecon RAT hidden in SOHO routers infected 70,000 devices in 20 countries in two years
- Chinese Hackers Deploy VersaMem Web Shell via Versa Director Zero-Day
- “TheMoon” Malware Returns: Thousands of Routers Compromised
- Sophisticated J-Magic Backdoor Evades Detection on Juniper Routers
