
iPhone device farm with multiple devices displaying stolen credit card information and actively sending scam iMessages | Image: Prodaft
In the ever-evolving landscape of cyber threats, Phishing-as-a-Service (PhAAS) platforms have emerged as a significant concern, enabling cybercriminals to conduct large-scale phishing campaigns with ease. The recent report by Prodaft sheds light on one such platform, uncovering its sophisticated infrastructure, widespread impact, and the threat actors behind it.
Lucid is a PhAAS platform operated by Chinese-speaking threat actors that has been targeting 169 entities across 88 countries globally. With a scalable, subscription-based model, Lucid allows cybercriminals to conduct large-scale phishing campaigns to harvest credit card details for financial fraud. The platform stands alongside other prominent PhAAS platforms like Darcula and Lighthouse.
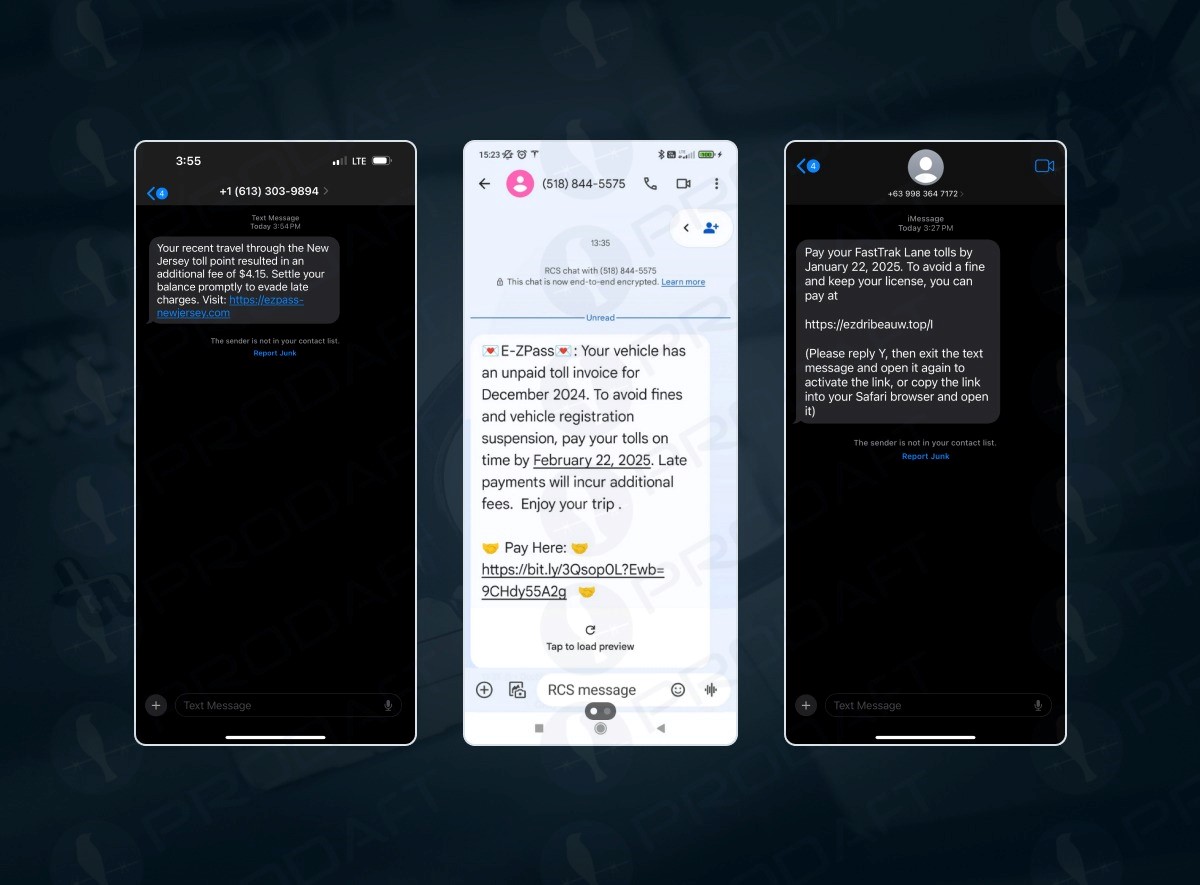
The platform employs an automated attack delivery mechanism, deploying customizable phishing websites distributed primarily through SMS-based lures. To enhance effectiveness, Lucid leverages Apple iMessage and Android’s RCS technology, bypassing traditional SMS spam filters and significantly increasing delivery and success rates. This strategic use of advanced messaging technologies allows threat actors to evade traditional security measures and reach a broader audience.
Lucid incorporates advanced anti-detection and evasion techniques to prolong the lifespan of its phishing sites. These techniques include IP blocking and user-agent filtering, making it more challenging for security professionals to identify and neutralize malicious activities. Additionally, the platform features a built-in card generator, enabling threat actors to validate and exploit stolen payment data efficiently.
The report emphasizes the growing reliance on PhAAS platforms to facilitate payment fraud and financial cybercrime. These platforms provide cybercriminals with ready-made phishing solutions, facilitating the widespread dissemination of attacks. As the report states, “Given its advanced infrastructure and persistent activity, Lucid poses a significant and ongoing cyber threat,” necessitating heightened vigilance and proactive mitigation efforts.
The group behind Lucid PhAAS, known as Black Technology or XinXin, has been active since 2023. Their operations, initially local, have grown substantially, with a significant surge expected by early 2025. The XinXin group has emerged as a primary source of smishing campaigns targeting Europe, the United Kingdom, and the United States, focusing on stealing credit card information and personally identifiable information (PII).
The XinXin group utilizes various smishing services to send messages that appear legitimate to randomly targeted users. These messages often reference unpaid toll fees, shipping costs, or tax declarations. The success of these campaigns is attributed to the high volume of messages sent. Unlike dedicated phishing services that target specific users, Lucid campaigns focus on collecting as many phone numbers as possible, reflecting the growing influence of Chinese-speaking actors in the underground economy.
Threat actors exploit several architectural vulnerabilities, including encryption blind spots, trust perception exploitation, and specific technical approaches to bypass security measures. The end-to-end encryption in RCS and iMessage creates a blind spot, making network-level filtering ineffective. Threat actors also leverage visual trust indicators, such as blue bubbles in iMessage, to create a perception of legitimacy.