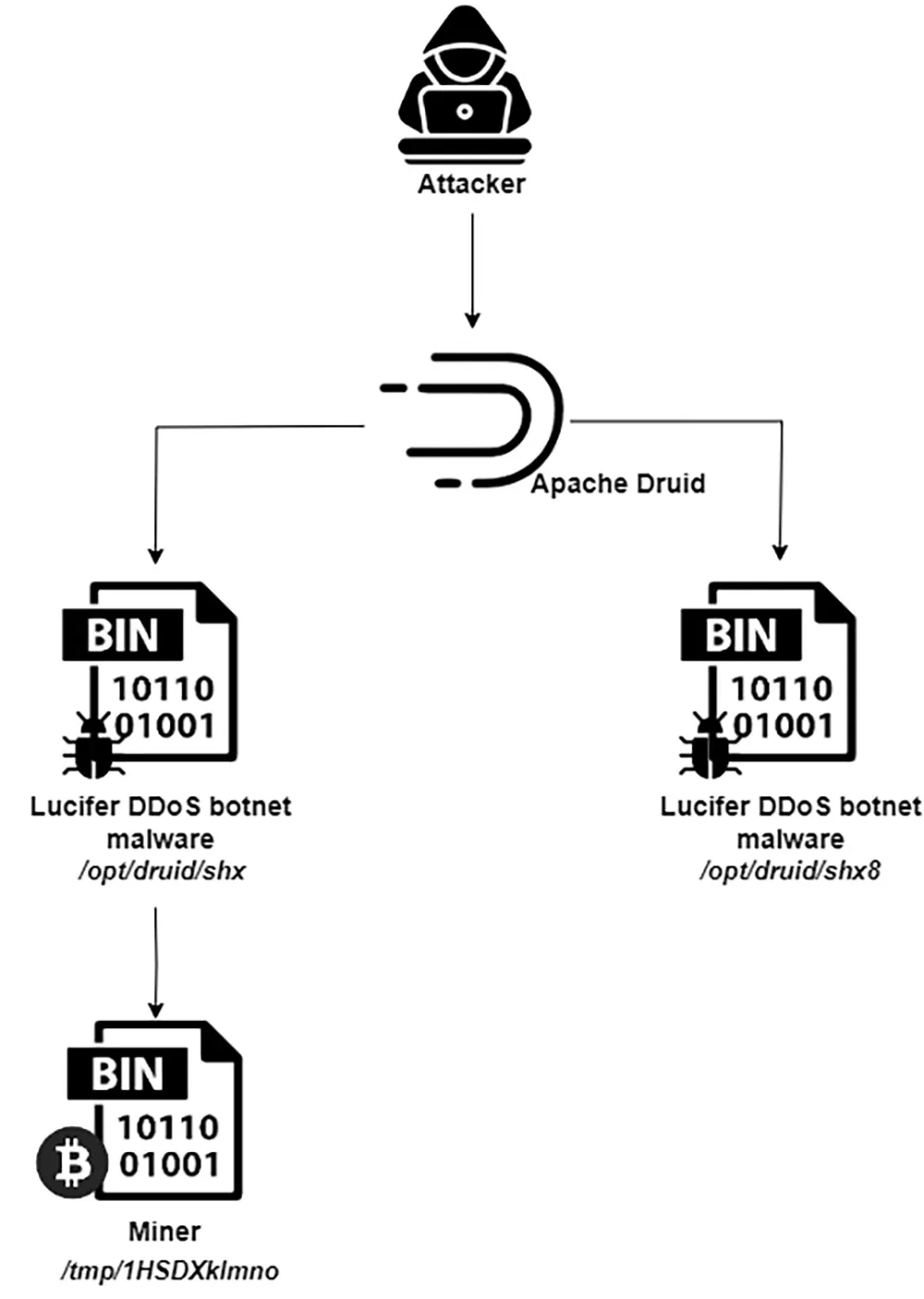
Attack flow, third phase
Security researchers at Aqua Nautilus have uncovered a sophisticated campaign exploiting misconfigurations and vulnerabilities in Apache Hadoop and Apache Druid. This campaign leverages a potent variant of the Lucifer DDoS botnet with observed evolutions, ultimately establishing infected Linux systems as components of a Monero cryptomining operation.
The open-source Apache Software Foundation supports hundreds of active projects, making it a rich target landscape. Apache Hadoop and Apache Druid provide the capabilities necessary for the storage, retrieval, and real-time analysis of massive datasets – capabilities increasingly sought after across various industries. These projects’ large user base and extensive code contributions increase the likelihood of exploitable vulnerabilities or misconfiguration. The targeted vulnerabilities and misconfigurations include:
- Apache Druid CVE-2021-25646: Vulnerability enabling remote code execution via malicious JavaScript injection.
- Apache Hadoop YARN: Misconfigured APIs susceptible to remote code execution exploits.
The Lucifer campaign’s phases have been delineated:
- Reconnaissance: Continuous scanning for systems with exposed Apache Hadoop or Apache Druid instances.
- Exploitation: Targeting specific vulnerabilities, such as Apache Druid CVE-2021-25646, or exploiting misconfigurations in Apache Hadoop YARN APIs to gain an initial foothold.
- Dropper Deployment: Downloading and executing Lucifer malware, often in multiple evolutionary stages. Attackers modify dropper behavior to potentially bypass detection mechanisms.
- Cryptominer Installation: Fetching the XMRig cryptomining payload and executing it to siphon computational resources for financial gain.
- Persistence: Establishing persistence techniques, such as cronjob scheduling, to maintain long-term control of infected systems.
The first phase of the attack sees the exploitation of Apache Hadoop YARN, leading to the download and execution of the Lucifer malware, thereby hijacking the compromised system for cryptomining. This phase is characterized by the downloading of a single ELF binary, serving as a dropper for the main payload—an XMRig cryptominer.
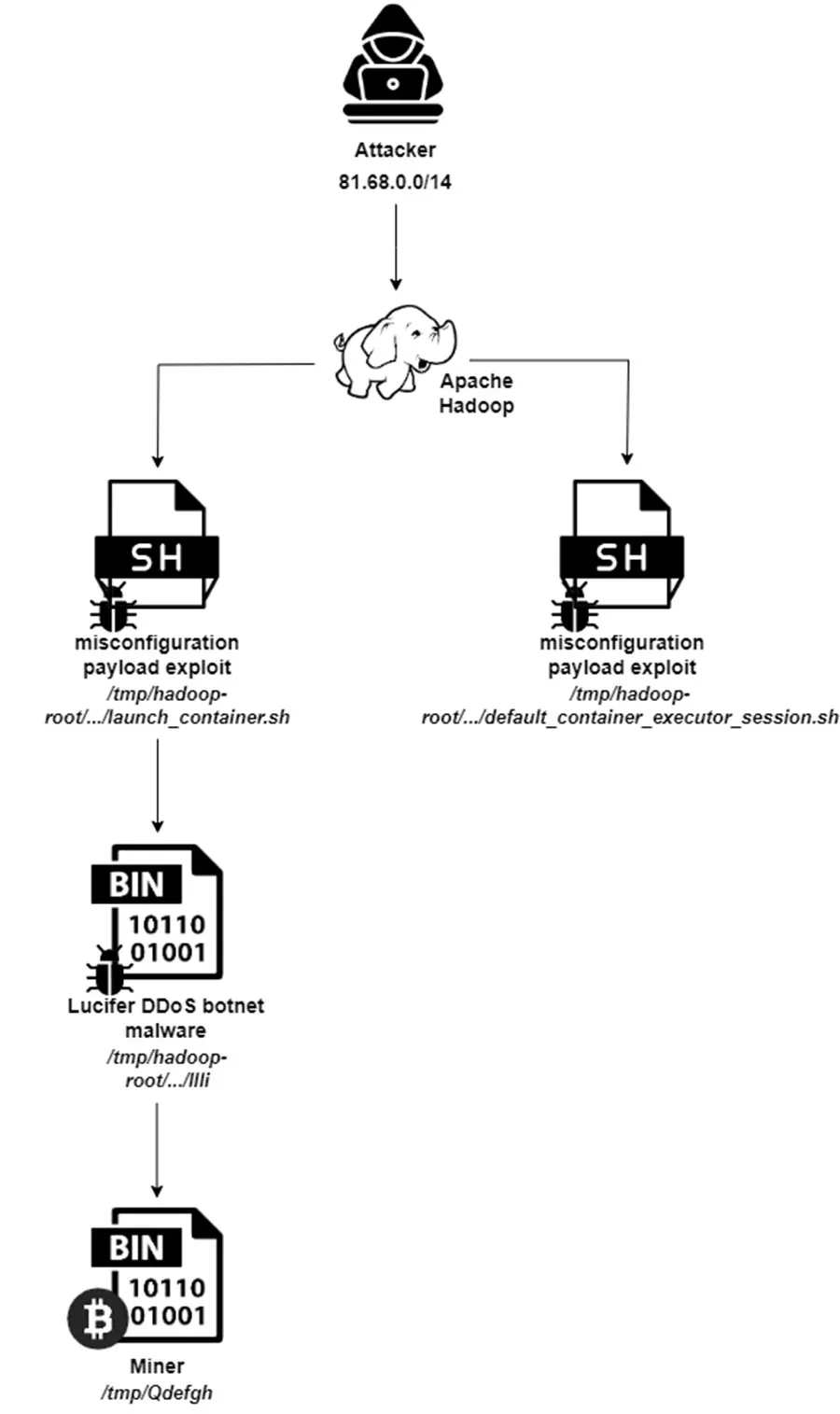
As the campaign evolves, the complexity of the attack increases. The second phase witnesses the deployment of two ELF binaries—one acting as the familiar dropper and the other’s purpose shrouded in mystery. This stage hints at the attackers’ experimentation, possibly probing for defense evasion techniques.
The campaign’s final phase sees the attackers shifting their focus to Apache Druid, exploiting the CVE-2021-25646 vulnerability to gain initial access. This stage is marked by the downloading and execution of two malicious binaries, indicating a refined strategy aimed at evading detection and ensuring persistence.

The Lucifer malware emerges as a formidable weapon in the attackers’ arsenal, boasting capabilities that extend beyond mere cryptomining. It is capable of command and control operations, self-propagation through the exploitation of multiple vulnerabilities, credential brute-forcing, and even launching DDoS attacks.
The Lucifer campaign is a stark reminder of the risks facing open-source technologies within the big data landscape. Organizations must invest in robust cybersecurity infrastructure, maintain meticulous patch management, and foster a security-first culture to safeguard critical assets and business operations.