Lucky CAT: A distributed fuzzing management framework
Lucky CAT – Crash All the Things!
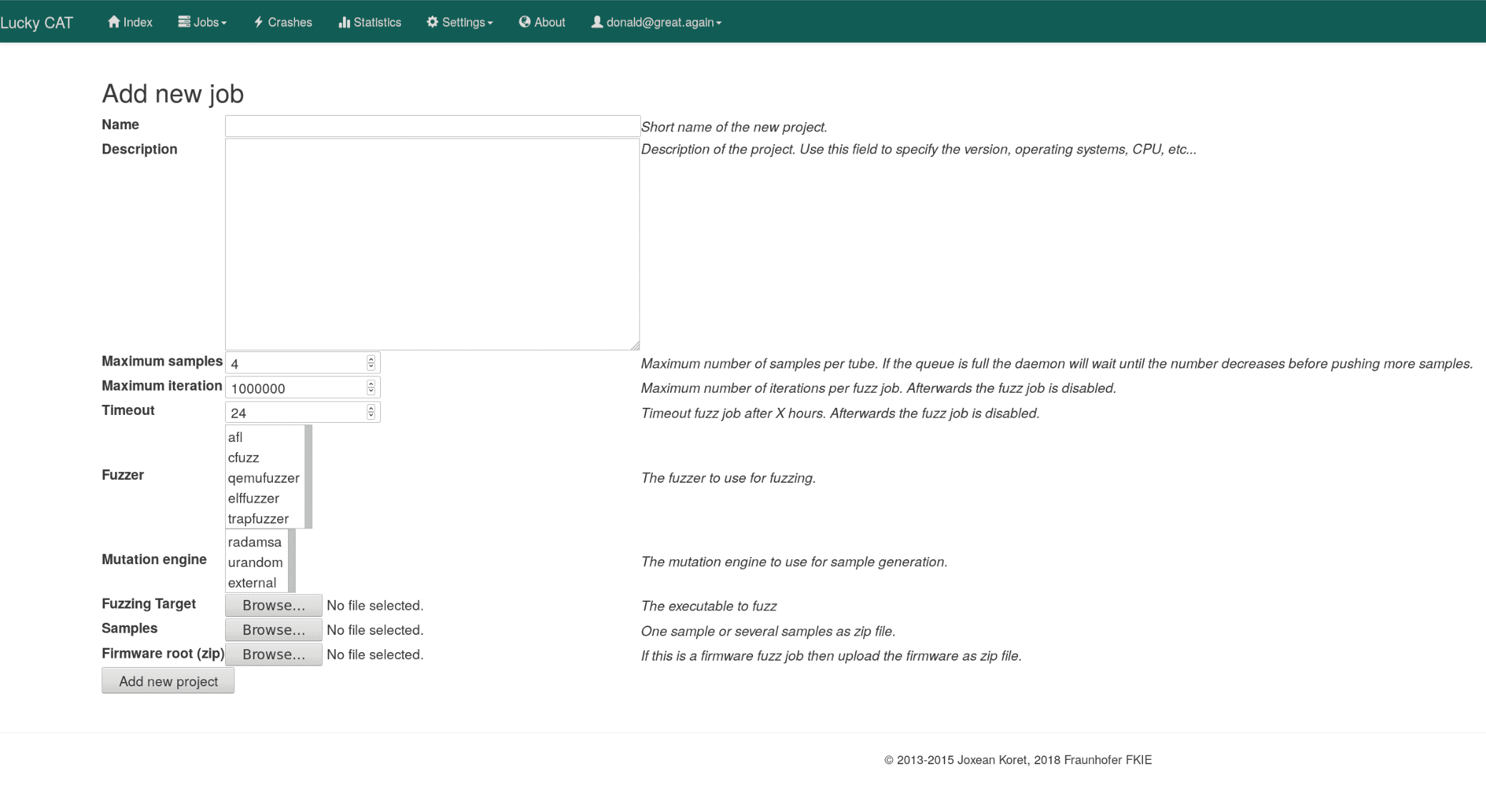
What is Lucky CAT?
Lucky CAT (Crash All the Things!) is a distributed fuzzing testing suite with an easy to use web interface. It allows managing several fuzzing jobs on several remote machines concurrently. Lucky CAT aims to be easily usable, scalable, extensible, and fun.

Lucky CAT’s origin is Joxean Koret’s Nightmare Fuzzing Project. However, there may be only traces of Nightmare and Lucky CAT is more 2018-ish by relaying, amongst others, on Bootstrap, Docker, MongoDB, Python 3, and RabbitMQ.
Why use Lucky CAT?
Lucky CAT offers the following features:
- Fuzz job management: primary focus on black box fuzzing and embedded devices
- Easy deployment: thanks to Docker and Docker Compose
- Scalability: Lucky CAT uses a microservice architecture backed by RabbitMQ
- Easy integration: Lucky CAT provides a RESTful API to integrate it with your other tools
- Responsive WebUI: for job management, crash analysis, and statistics
- Fast command line client: for those who never leave the terminal…
- Fuzzers included: tiny POSIX-compatible fuzzer cfuzz, afl, afl-otherarch wrappers and many more
- Easy fuzzer integration: integrate other fuzzer into Lucky CAT by using either a Python template or a C template
- Crash verification: local and remote crash verification with the gdb plugin exploitable
And because we use it to find bugs:
- CVE-2018-3005: Oracle VirtualBox (found with trap_fuzzer)
- CVE-2018-6924 / FreeBSD-SA-18:12.elf: FreeBSD x64 kernel (found with elf_fuzzer)
- CVE-2018-14775 / OpenBSD 6.3 errata 015 / OpenBSD 6.2 errata 020: OpenBSD i386 kernel (found with trap_fuzzer)
- OpenBSD 6.3 errata 012 / OpenBSD 6.2 errata 018: OpenBSD x64 kernel (found with elf_fuzzer)
Lucky CAT comes with batteries included: mutation engines, fuzzers and crash verifiers. Nevertheless, you may integrate your own fuzzing tools as well.
Fuzzers
You need fuzzers in order to provoke crashes. They stress test the fuzzing target and check if it has crashed. Lucky CAT comes with built-in fuzzers like the elf_fuzzer for fuzzing Linux/BSD ELF binaries or a minimalistic file fuzzer called cfuzz, which can be deployed on POSIX compatible devices like your average router. There are also plugins for other fuzzer projects: one plugin wraps afl for fuzzing x86/x64 targets on Linux and BSD and another plugin called qemu_fuzzer wraps afl-other-arch to fuzz binaries on all of the QEMU supported target architectures.
Mutation Engines
Lucky CAT allows fuzzer to have their own mutation engine (e.g. afl). However, many times you write a quick and simple fuzzer that does not come with its own mutation engine. Therefore, Lucky CAT mutates test cases for you. Mutated test cases are published via a queue from which multiple fuzzer instances can consume. This allows you to scale easily, just add more instances. As the time of writing, Lucky CAT supports two fuzzing engines: Radamsa and /dev/urandom.
Crash Verifiers
What are all the crashes good for if you have to manually verify them and determine their exploitability? Therefore, Lucky CAT publishes them to registered verifier. They consume the crashing test cases and determine their exploitability for you. Currently, there are two verifiers included in Lucky CAT: a local and a remotely exploitable verifier. Both utilize the GDB plugin exploitable in order to determine the exploitability of a test case. The first does this locally. The second asks our remote C client (rexploitablec) to do so.
Copyright (C) 2018 – Fraunhofer FKIE (thomas.barabosch@fkie.fraunhofer.de)
Copyright (C) 2013 – 2015 Joxean Koret (admin@joxeankoret.com)





