Source: CloudSEK
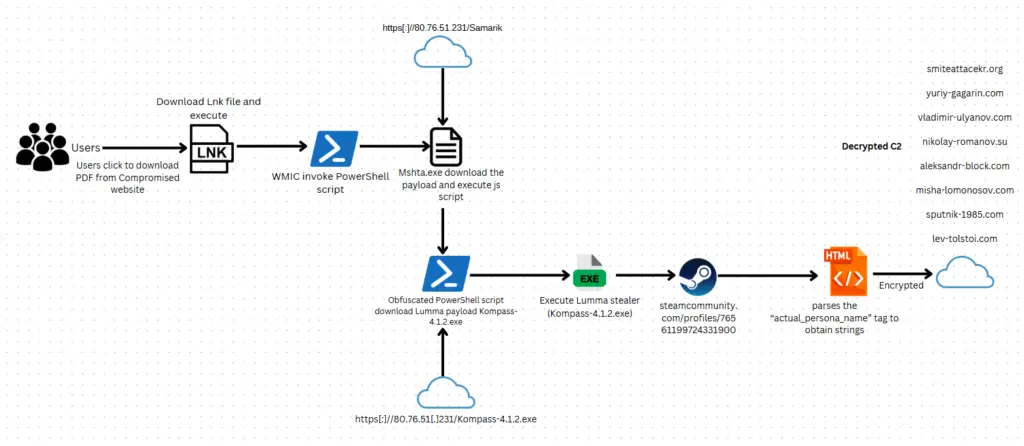
A new report from CloudSEK reveals an ongoing malware campaign distributing the Lumma Stealer information stealer, primarily targeting educational institutions but also affecting various other sectors. The campaign employs malicious LNK (shortcut) files disguised as legitimate PDF documents to trick users into initiating a multi-stage infection process.
The attackers are exploiting compromised educational institutions’ infrastructure to host malicious files on WebDAV servers. Users are lured into downloading these files under the pretense of accessing school fee structures or other seemingly innocuous documents. The malicious LNK files, when clicked, execute a PowerShell command that downloads and runs obfuscated JavaScript code. This code ultimately leads to the deployment of the Lumma Stealer payload.
“The campaign’s primary infection vector involves using malicious LNK (shortcut) files that are crafted to appear as legitimate PDF documents,” the report states. These LNK files exploit “unique features” to “deceive users and bypass security measures, making them effective tools for infiltrating systems and networks.”
Once executed, Lumma Stealer can steal a variety of sensitive data, including passwords, browser information, and cryptocurrency wallet details. The malware then attempts to connect with command and control (C2) servers to exfiltrate the stolen data.
Lumma Stealer employs several evasion techniques to avoid detection:
- Obfuscated JavaScript Execution – The initial LNK file runs a PowerShell script, which is hidden within JavaScript overlay code.
- AES-Encrypted Payload – The malware downloads an AES-encrypted payload and decrypts it in CBC mode using a hardcoded key.
- Mathematical Obfuscation – The PowerShell script uses basic arithmetic techniques to hide its true functionality.
Once deployed, Lumma Stealer exfiltrates stolen data to command-and-control (C2) servers, enabling attackers to harvest passwords, cryptocurrency wallets, and browser session details.
Interestingly, the report notes that the malware also includes a Steam URL as a fallback communication channel. “The sample uses the Steam connection if it cannot access every C2 domain it owns,” the researchers explain.
As CloudSEK warns, this campaign is ongoing, with new attack variants likely to emerge. Businesses, governments, and educational institutions must remain vigilant and proactive to defend against this rapidly evolving cyber threat.
Related Posts:
- Lumma Stealer MaaS: Clipboard Hijacking and LOLBins Used in Latest Campaign
- MaaS in Action: How Lumma Stealer Employs Advanced Delivery Techniques
- LUMMA Malware: Cybercriminals Elevate Tactics with Fake Invoice Campaign
- Cybercriminals Turn Discord into Malware Playground with Lumma Stealer
- LNK Files and SSH Commands: The New Arsenal of Advanced Cyber Attacks