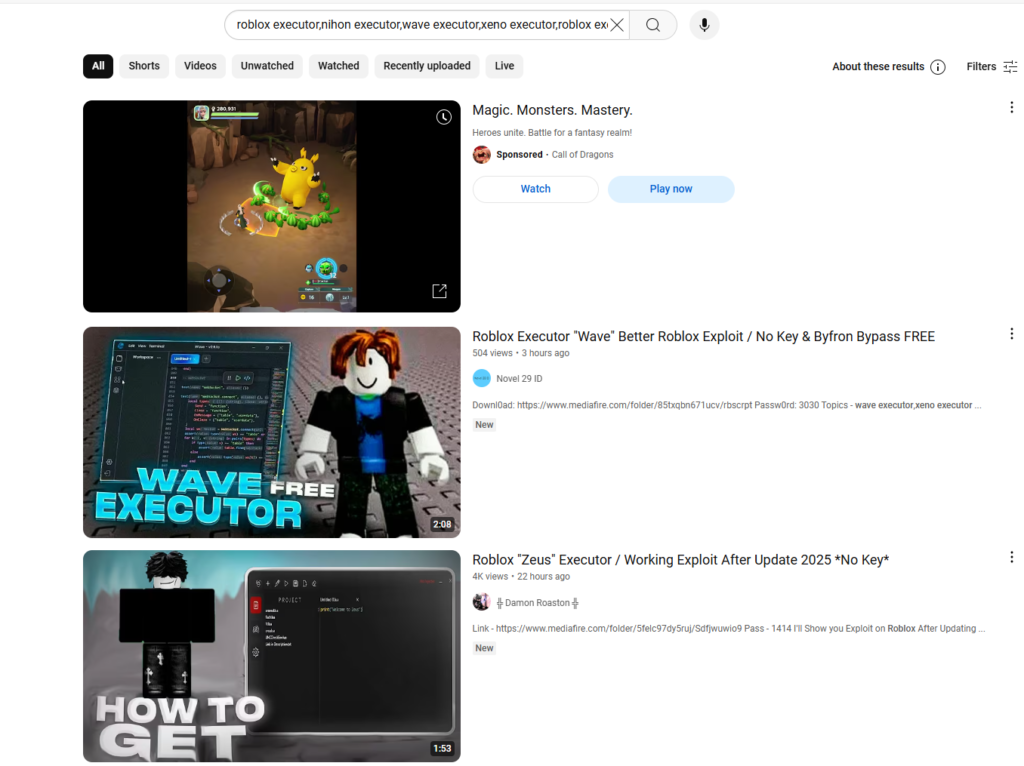
Examples of suspicious exploits being advertised through YouTube | Image: Silent Push
Silent Push Threat Analysts have uncovered new developments in the spread of Lumma Stealer, a notorious infostealer malware that has been gaining traction through deceptive online tactics. The latest report details how malicious actors are leveraging YouTube, Cloudflare, and MediaFire to distribute this malware, posing significant risks to unsuspecting users worldwide.
Originally surfacing on Russian-language criminal forums in 2022, Lumma Stealer operates under a Malware-as-a-Service (MaaS) model, allowing cybercriminals to buy access based on tiered pricing. The malware is designed to extract browser credentials, stored financial information, cryptocurrency wallet data, and other sensitive details.
According to Silent Push, “From 2023 onward, the number of compromises linked to Lumma Stealer has risen dramatically, particularly those including the resale of stolen credentials to other criminals.”
Lumma Stealer’s operators employ a variety of distribution techniques, many of which exploit popular platforms. Among the primary infection vectors identified are:
- Malicious YouTube links: Attackers hide malware-infected files in video descriptions, comments, and downloadable resources.
- Fake CAPTCHA verifications: A technique known as ClickFix tricks users into executing malware by mimicking a legitimate verification process.
- Cloudflare and MediaFire-hosted malware: Hackers abuse these trusted services to evade detection while spreading malicious files.
Silent Push warns that “The increase in malware being spread via malicious YouTube links and infected files disguised in videos, comments, or descriptions is alarming.”
Investigators found that Lumma Stealer logs, which contain stolen credentials, are being shared for free on Leaky[.]pro, a relatively new hacking forum. This platform offers billions of “URL:LOG:PASS” records, making it a goldmine for cybercriminals looking to exploit compromised accounts.
Silent Push notes, “Lumma Stealer logs are being shared for free on Leaky[.]pro, offering billions of records with specific details tied to stolen credentials.”
Silent Push analysts have identified patterns in Lumma Stealer’s infrastructure, revealing that threat actors often register C2 domain clusters in bulk. Many of these domains are left to age before being activated, a technique that helps evade detection.
“Threat actors using Lumma Stealer appear to register clusters of roughly 10-20 domains at a time, some of which are used immediately and others that are left to age for up to two weeks,” the report states.
Related Posts:
- Lumma Stealer Malware Campaign Targets Educational Institutions with Deceptive PDF Lures
- Lumma Stealer MaaS: Clipboard Hijacking and LOLBins Used in Latest Campaign
- MaaS in Action: How Lumma Stealer Employs Advanced Delivery Techniques
- LUMMA Malware: Cybercriminals Elevate Tactics with Fake Invoice Campaign
- Cybercriminals Turn Discord into Malware Playground with Lumma Stealer