Security researchers from AhnLab Security (ASEC) recently identified a new variant of the LummaC2 malware, which utilizes the popular gaming platform Steam as a C2 server. This method significantly heightens the threat to users and organizations worldwide.
LummaC2 is an infostealer that actively propagates under the guise of illicit programs such as cracks, keygens, and game cheats. These malicious files are distributed through various channels, including YouTube, LinkedIn, and even search engine advertisements using a technique known as SEO Poisoning.
Recently, LummaC2 has also been disguised as legitimate applications, such as Notion, Slack, and Capcut, thereby broadening its target audience. According to ASEC, LummaC2 was initially distributed as a single executable file (EXE) or through the technique of DLL Sideloading, where a malicious DLL is compressed along with a legitimate EXE file. This method allowed the virus to remain undetected by many security systems.
In its new variant, LummaC2 uses the Steam platform to retrieve information about C2 domains, whereas previously, all information about the C2 infrastructure was embedded in the malware sample itself. With this innovation, attackers can now dynamically change C2 domains using a legitimate platform, increasing the virus’s resilience and reducing the likelihood of detection.
It should be noted that this method is not entirely new. It mirrors a strategy previously employed by the Vidar virus, which also exploited various legitimate platforms such as TikTok, Mastodon, and Telegram to obtain C2 infrastructure information.
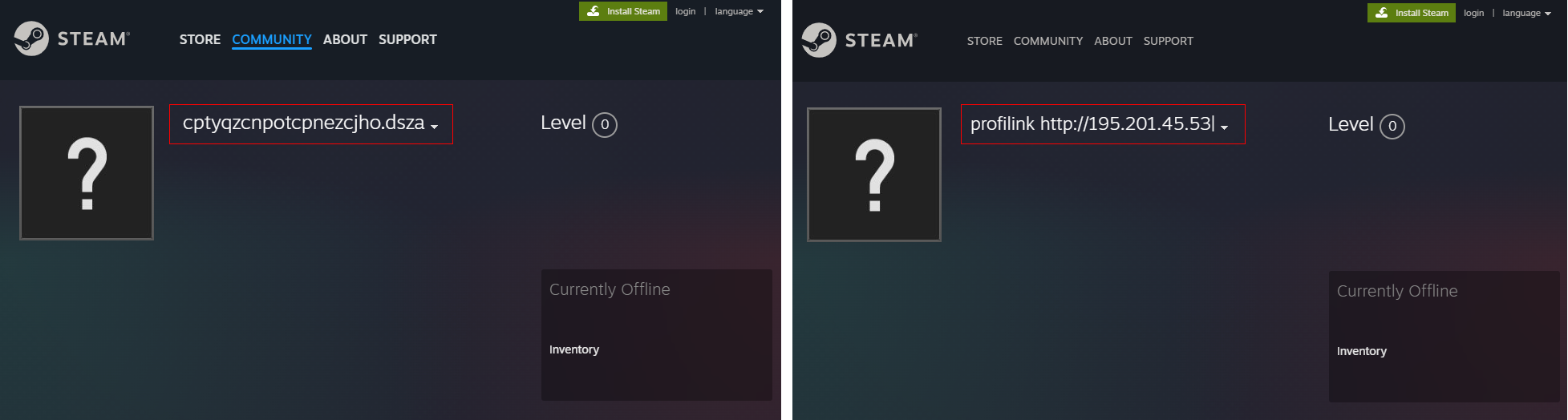
Upon execution, LummaC2 decrypts its internal encrypted strings to obtain information about C2 domains. If all embedded domains are inaccessible, the virus initiates a connection to Steam. The necessary URL within the gaming platform is stored directly in the executable code.
The recorded URL points to a specific Steam account profile page, presumably created by the attacker. The malware retrieves a string by parsing the “actual_persona_name” tag on this page, which is then decrypted using a Caesar cipher to obtain the current C2 domain.
Utilizing a legitimate service like Steam, with its vast user base, helps reduce suspicion and allows the attacker to easily change the C2 domain as needed. This flexibility increases the likelihood of a successful attack and makes the virus more difficult for security systems to detect.
After decrypting the domain, LummaC2 connects to the C2 server and downloads an encrypted JSON configuration file. This file is also decrypted, and the virus performs malicious actions based on the specified settings. The stolen information includes data from password storage programs, browsers, VPNs, FTP, and many other applications. It is sent to the hackers’ C2 server upon completion of the malware’s tasks.
To mitigate the risks associated with LummaC2 and similar malware, organizations, and individuals are advised to:
- Avoid downloading illicit software from unreliable sources.
- Use only reputable antivirus software.
- Regularly update software to protect against known vulnerabilities.
- Educate users about the risks of downloading and executing unknown files.
- Monitor network traffic to detect unusual patterns that may indicate a virus infection.
All these measures will help better protect against the sophisticated tactics of LummaC2 and other emerging cyber threats.
Related Posts:
- LummaC2 and Raccoon Stealer: The Rise of Certificate Abuse in Malware
- Beware! Fake Notion Installer Spreads Data-Stealing Malware
- ClearFake Campaign Employs Novel Social Engineering Tactic to Deliver LummaC2 Infostealer