LUNAR SPIDER malvertising campaign Image: EclecticIQ
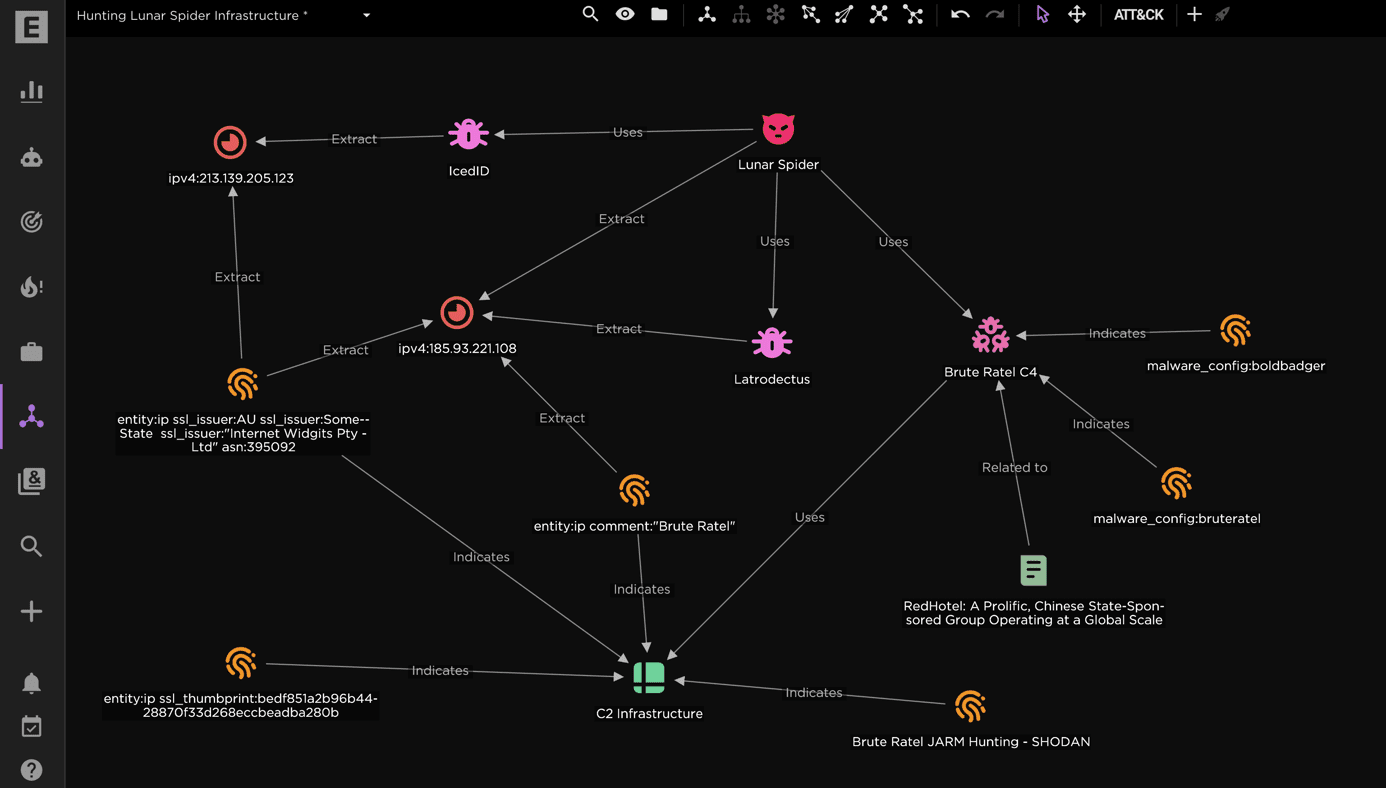
The EclecticIQ Threat Research Team recently unveiled a new malvertising campaign linked to the notorious LUNAR SPIDER group, a Russian-speaking, financially motivated cybercriminal organization known for deploying high-profile malware families like IcedID and Latrodectus. In October 2024, LUNAR SPIDER resumed operations following a period of disruption by law enforcement, utilizing sophisticated techniques to evade detection and maintain its foothold in the cybercriminal ecosystem.
Known for deploying IcedID malware in ransomware campaigns, LUNAR SPIDER’s latest strategy has seen the adoption of Brute Ratel C4 (BRc4) in its attack arsenal. According to EclecticIQ analysts, “The actor leveraged Brute Ratel C4, demonstrating notable adaptability and determination to continue their activities despite heightened law enforcement pressure.” This marks a significant tactical shift, with the group now relying on the Latrodectus downloader to deliver Brute Ratel.
This malvertising campaign leverages SEO poisoning, a technique in which search engine results are manipulated to trick users into clicking on malicious links. In this instance, the Latrodectus downloader targeted financial services, redirecting victims searching for tax-related content to download an obfuscated JavaScript file. Once activated, this file retrieved a malicious MSI installer, masquerading as a legitimate NVIDIA file, which ultimately installed Brute Ratel C4 on the victim’s system.
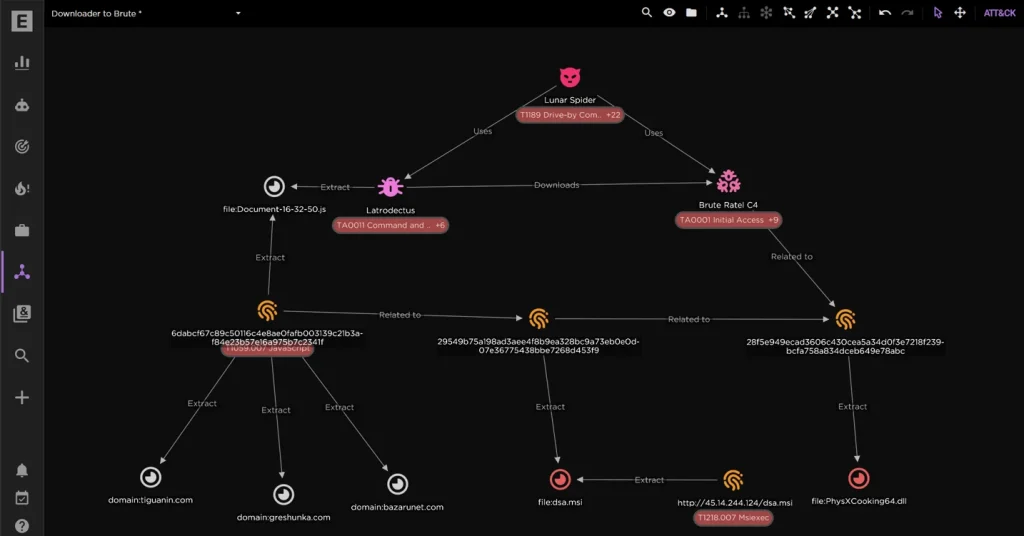
The report notes, “This consistent use of shared providers and similar infrastructure highlights how LUNAR SPIDER is efficiently coordinating its malicious activities across different malware families.” By utilizing over 200 malicious infrastructures and overlapping command-and-control servers, LUNAR SPIDER can disguise and sustain its campaigns with efficiency.
LUNAR SPIDER’s influence within the cybercriminal ecosystem is extensive. Evidence suggests significant collaboration with other groups, including WIZARD SPIDER, the group behind TrickBot and Conti ransomware, and ALPHV/BlackCat ransomware affiliates. According to the report, “LUNAR SPIDER has established significant connections within the cybercrime ecosystem” through its IcedID malware, which provides initial access for ransomware operators. Shared infrastructure, such as the IP address 173[.]255[.]204[.]62 used by both LUNAR SPIDER’s Latrodectus and ALPHV’s C2 domains, illustrates the operational synergy among these threat actors.
EclecticIQ leveraged the MITRE ATT&CK Analysis Tool to map LUNAR SPIDER’s tactics, techniques, and procedures (TTPs), which is instrumental in understanding the threat actor’s behavior. The report highlights the value of this mapping: “By understanding these techniques, security teams can build more effective detection and response strategies, enhancing their ability to prevent similar attacks.”
As LUNAR SPIDER continues to adapt and expand its reach, cybersecurity teams in the financial sector and beyond are urged to remain vigilant, particularly concerning malvertising and SEO poisoning attacks.
Related Posts:
- Patchwork Group Expands Cyber Espionage with Advanced Tools
- Latrodectus Malware Evolves: New Payload Features Enhance Evasion and Control
- FCC Takes Aim at SIM Swapping Fraud, Protecting Consumers from Billions in Losses
- LATRODECTUS Malware Loader: Threat Poised to Replace ICEDID
- Watch Out for Latrodectus: New Malware from Suspected IcedID Developers Targeting Businesses