MAAD Attack Framework: simple, fast & effective security testing of M365 & Azure AD

MAAD Attack Framework
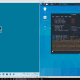
MAAD-AF is an open-source cloud attack tool developed for testing the security of Microsoft 365 & Azure AD environments through adversary emulation. MAAD-AF provides security practitioners with easy-to-use attack modules to exploit configurations across different M365/AzureAD cloud-based tools & services.
MAAD-AF is designed to make cloud security testing simple, fast, and effective. Through its virtually no-setup requirement and easy-to-use interactive attack modules, security teams can test their security controls, detection, and response capabilities easily and swiftly.

Features
- Pre & Post-compromise techniques
- Simple interactive use
- Virtually no-setup requirements
- Attack modules for Azure AD
- Attack modules for Exchange
- Attack modules for Teams
- Attack modules for SharePoint
- Attack modules for eDiscovery
MAAD-AF Attack Modules
- Azure AD External Recon (Includes sub-modules)
- Azure AD Internal Recon (Includes sub-modules)
- Backdoor Account Setup
- Trusted Network Modification
- Disable Mailbox Auditing
- Disable Anti-Phishing
- Mailbox Deletion Rule Setup
- Exfiltration through Mailbox Forwarding
- Gain User Mailbox Access
- External Teams Access Setup (Includes sub-modules)
- eDiscovery exploitation (Includes sub-modules)
- Bruteforce
- MFA Manipulation
- User Account Deletion
- SharePoint exploitation (Includes sub-modules)
Requirements
- Internet-accessible Windows host
- PowerShell (version 5 or later) terminal as Administrator
- The following PowerShell modules are required and will be installed automatically:
- Az,
- AzureAd,
- MSOnline,
- ExchangeOnlineManagement,
- MicrosoftTeams,
- AzureADPreview,
- ADInternals,
- Microsoft.Online.SharePoint.PowerShell,
- PnP.PowerShell
Note: A ‘Global Admin’ privilege is required to leverage the full capabilities of modules in MAAD-AF
Limitations
- MAAD-AF is currently only fully supported on Windows OS
Install
- Clone or download the MAAD-AF github repo to your Windows host: git clone https://github.com/vectra-ai-research/MAAD-AF
- Open PowerShell as Administrator
- Navigate to the local MAAD-AF directory (cd /MAAD-Attack-Framework)
- Run MAAD_Attack.ps1 (./MAAD_Attack.ps1)
Copyright (C) 2023 vectra-ai-research