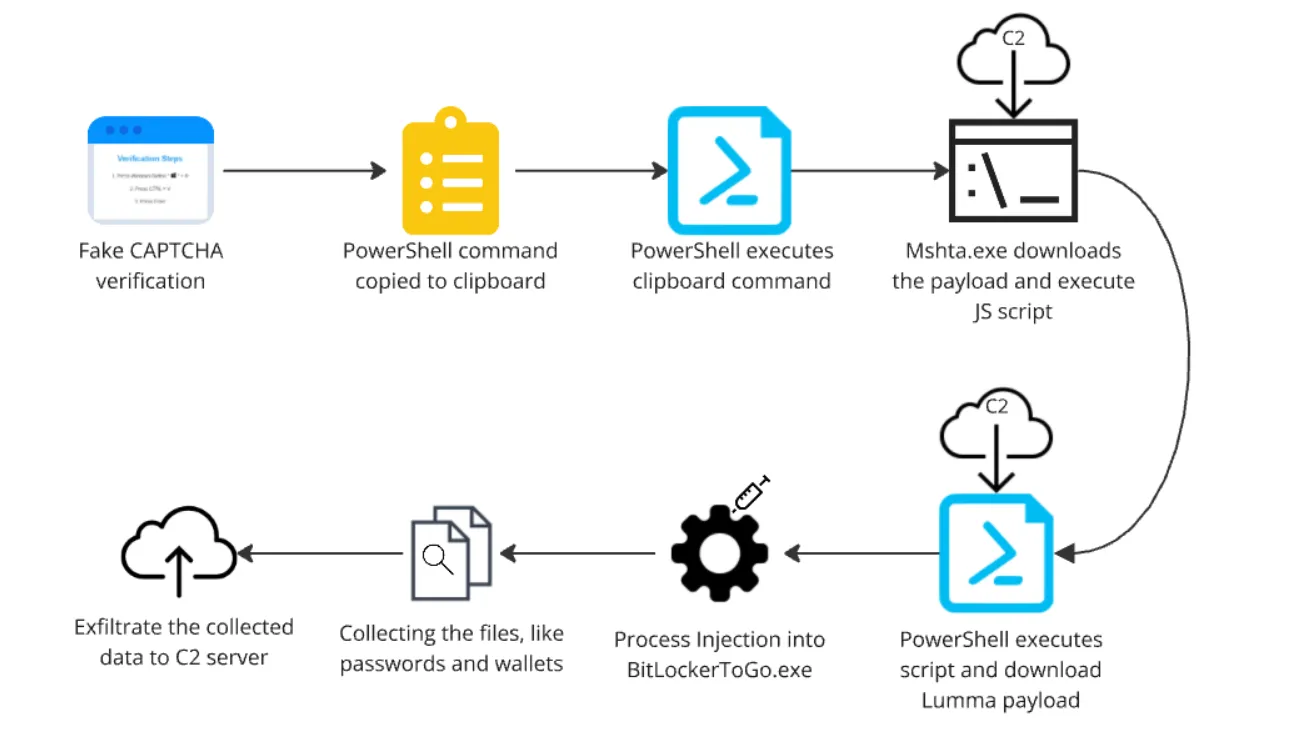
Lumma Stealer Execution Chain | Image: Qualys
Malware-as-a-service (MaaS) offerings have become an increasingly dangerous tool for cybercriminals. Among these threats is Lumma Stealer, a sophisticated information-stealing malware that Vishwajeet Kumar, Threat Research Engineer at Qualys, has recently analyzed. This analysis sheds light on how Lumma Stealer targets sensitive data such as passwords, browser information, and cryptocurrency wallets while employing advanced delivery techniques that make it a persistent and deceptive threat.
One of the most concerning aspects of the Lumma Stealer campaign is the shift from traditional phishing to more insidious tactics, such as using fake CAPTCHA verification to deceive users. According to the report, “threat actors frequently create phishing sites hosted on various providers, often leveraging Content Delivery Networks (CDNs)” to lure users into executing the malicious payload. Users interacting with these fake CAPTCHA pages are tricked into downloading malware through a multi-stage fileless technique.
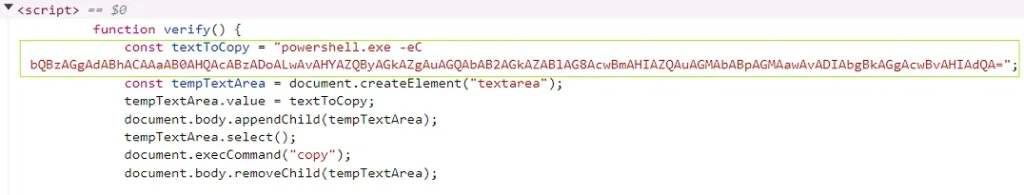
As described by the Qualys team, “the webpage code reveals an embedded payload, where a function called ‘verify’ contains a Base64-encoded PowerShell script that is copied to the clipboard when the verification button is pressed“. This script initiates the download of a stager, which eventually delivers the Lumma Stealer malware.
Lumma Stealer uses mshta.exe, a trusted Windows tool, to execute its malicious payload. By embedding obfuscated JavaScript code inside legitimate software, the malware can avoid detection. “The payload is using an interesting technique called- polyglot, where valid HTA content is embedded inside other files that are directly executable by mshta.”
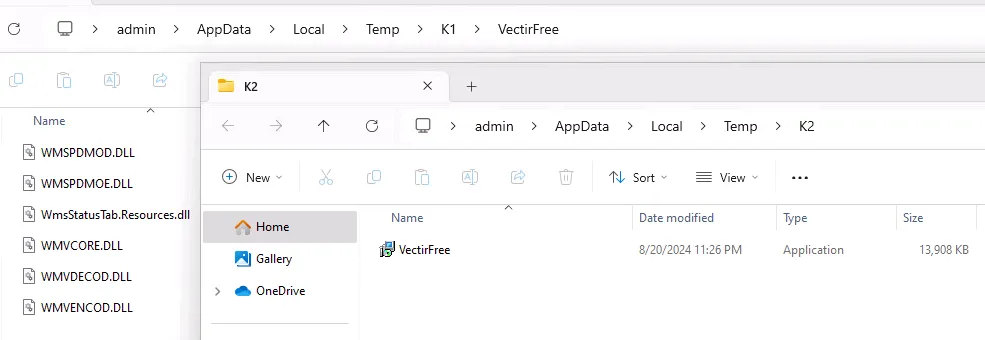
This approach allows the malware to operate under the radar, delivering an AES-encrypted PowerShell script that downloads the final malicious payload: Lumma Stealer, disguised as “Victirfree.exe.”
Lumma Stealer’s sophisticated evasion techniques further complicate detection efforts. It employs process hollowing, injecting its payload into a legitimate program—BitLockerToGo.exe—which then executes malicious tasks. As part of its obfuscation strategy, Lumma Stealer copies ‘Killing.bat’ and ‘Voyuer.pif’ into the temp directory. The bat script checks for antivirus processes, terminating those it identifies, including components from Webroot, Quick Heal, and Bitdefender, making the system even more vulnerable to attack.
Once Lumma Stealer gains a foothold, it aggressively searches the infected system for files containing sensitive information. The malware specifically looks for files related to cryptocurrency and passwords, using keywords like seed.txt, pass.txt, and .ledger.txt.
After collecting this data, Lumma Stealer attempts to exfiltrate it to command and control (C2) servers. The malware primarily communicates with domains using the .shop top-level domain (TLD), although the Qualys team notes that “currently, these C2 servers are unreachable.”
The full report and key Indicators of Compromise (IoC) can be accessed on the Qualys website to better protect against the evolving Lumma Stealer threat.
Related Posts:
- LUMMA Malware: Cybercriminals Elevate Tactics with Fake Invoice Campaign
- Cybercriminals Turn Discord into Malware Playground with Lumma Stealer
- Information Stealer Alert: Lumma Strikes Again with Go-Based Injector
- Cyber Alert: FortiGuard Labs Spot Lumma Stealer on YouTube