macOS Root Access Exploit: PoC Code for CVE-2024-27822 Released
A security researcher has published details and proof-of-concept (PoC) code for a macOS CVE-2024-27822 vulnerability that could be exploited to gain root privileges.
The security defect was identified and reported in March, with a patch available since the release of macOS Sonoma 14.5 in May. In its advisory, Apple notes that “a logic issue was addressed with improved restrictions.”

Image: Mykola Grymalyuk
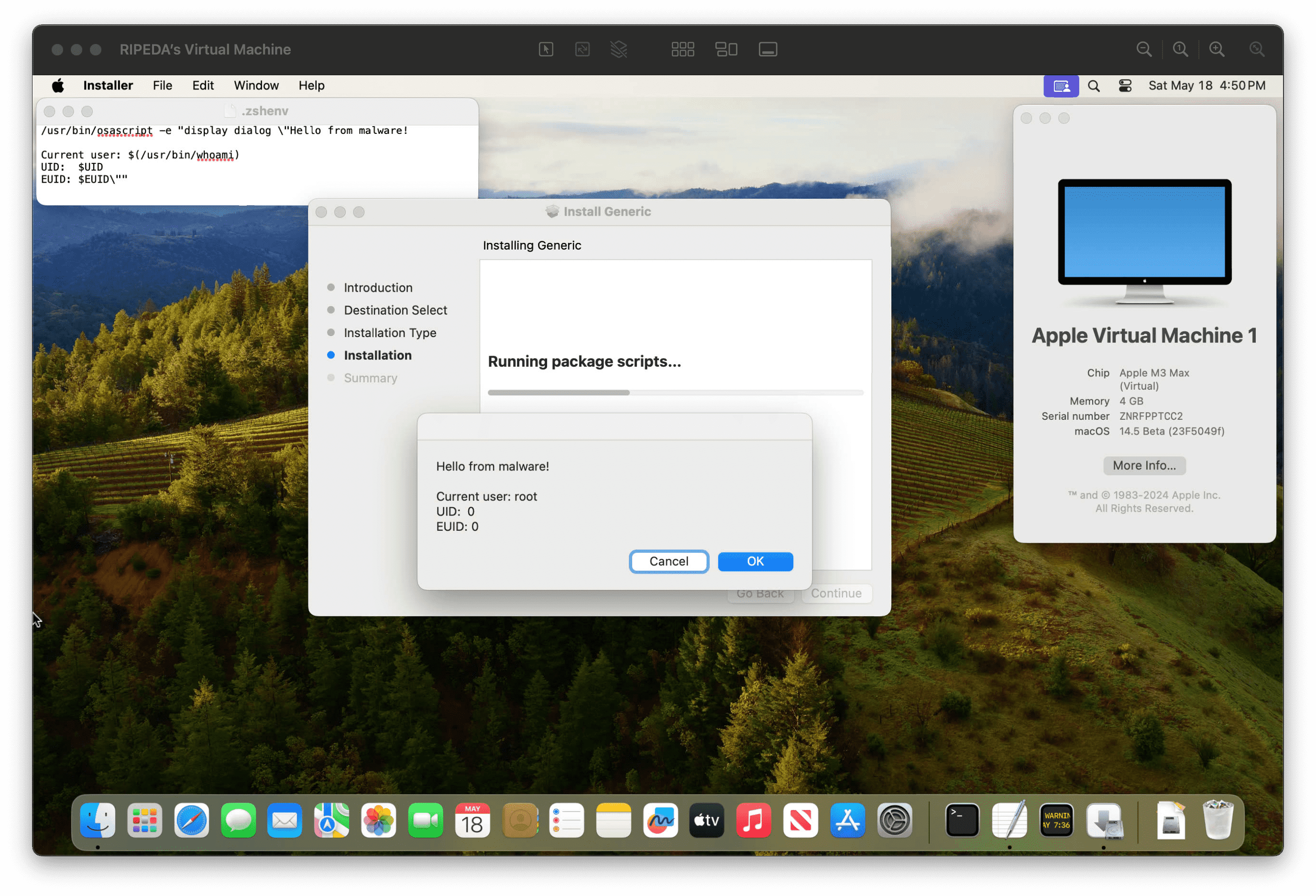
The recent analysis by security researcher Mykola Grymalyuk, CVE-2024-27822 centers around Apple’s Installer.app and the PackageKit.framework, which spawns installation scripts embedded in PKGs (package files) as root within the current user’s environment. The issue arises from the way these scripts, particularly those with the #!/bin/zsh shebang, load the user’s .zshenv file while running with root permissions.
The crux of this vulnerability is the ability to insert a malicious payload into the .zshenv file. When a user installs a ZSH-based PKG, the installation script executes with root privileges and loads the .zshenv file, thereby executing the embedded malicious code as root. This presents a significant security risk, especially in scenarios where users manually install PKGs.
The primary attack vector for this vulnerability involves a logic bomb-based payload, which can lie dormant within the .zshenv file. The payload waits for the user to install a ZSH-based PKG and then executes, granting the attacker root access. This could be particularly devastating in environments where users frequently install PKGs from various sources.
Mykola Grymalyuk has provided a proof of concept (PoC) to demonstrate the exploitation of CVE-2024-27822. The process is straightforward and highlights the severity of the vulnerability:
- Inject a malicious payload into the .zshenv file.
- Install a PKG with the #!/bin/zsh shebang (e.g., Generic-ZSH.pkg).
- Observe the execution of the payload with root privileges upon PKG installation.
An automated PoC, available in pkg_exploit.py, simplifies this process by creating a dummy PKG and injecting a payload into the .zshenv file.
To protect against this vulnerability, users and administrators should ensure their systems are updated to the latest macOS versions that address this issue:
- Update to macOS 14.5 Beta 2 (23F5059e) or newer
- Update to macOS 13.6.7 (22G720) or newer
- Update to macOS 12.7.5 (21H1222) or newer
Additionally, users should exercise caution when installing PKGs from untrusted sources and regularly review and secure their .zshenv files.