magicRecon
MagicRecon is a powerful shell script to maximize the recon and data collection process of an objective and finding common vulnerabilities, all this saving the results obtained in an organized way in directories and with various formats.
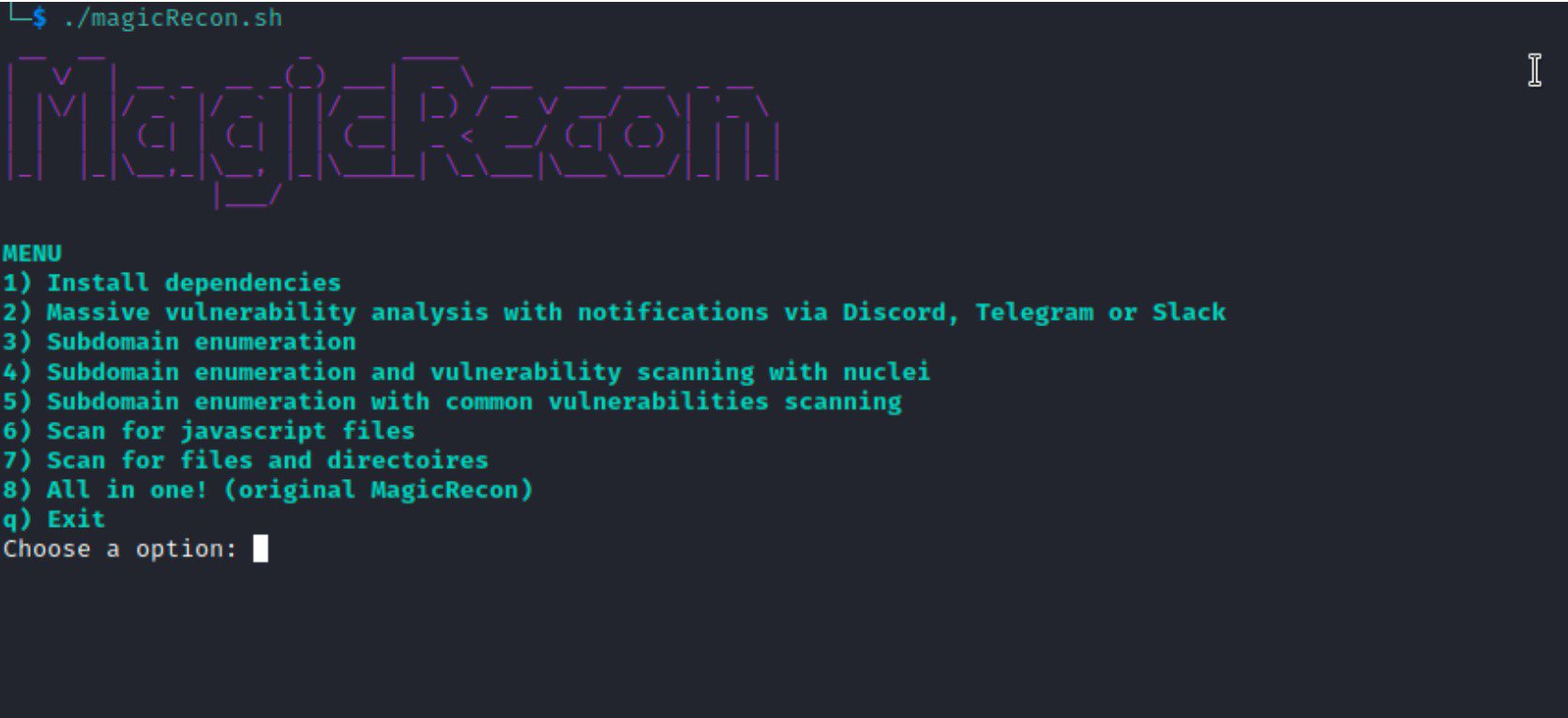
The new version of MagicRecon has a large number of new tools to automate as much as possible the process of collecting data from a target and searching for vulnerabilities. It also has a menu where the user can select which option he wants to execute.
This new version also has the option of “Install dependencies” with which the user can easily install all the tools and dependencies that are needed to run MagicRecon. The script code has been made in a modular way so that any user can modify it to their liking. With MagicRecon you can easily find:
- Sensitive information disclosure.
- Missing HTTP headers.
- Open S3 buckets.
- Subdomain takeovers.
- SSL/TLS bugs.
- Open ports and services.
- Email spoofing.
- Endpoints.
- Directories.
- Juicy files.
- Javascript files with sensitive info.
- CORS misconfiguration.
- Cross-site scripting (XSS).
- Open Redirect.
- SQL Injection.
- Server-side request forgery (SSRF).
- CRLF Injection.
- Remote Code Execution (RCE).
- Other bugs.
Install
Requirements
To run the project, you will need to install the following tools:
- Subfinder
- Httpx
- Notify
- Nuclei
- Nuclei-templates
- SecLists
- Corsy
- Securityheaders
- Ssl-checker
- Secretfinder
- Wfuzz
- Aquatone
- Html-tool
- Waybackurls
- Kxss
- Anew
- Qsreplace
- Urlprobe
- Anew
- Gf
- Gobuster
- Findomain
- spoofcheck
- linkfiner
- Nmap
Download
git clone https://github.com/robotshell/magicRecon.git
IMPORTANT: Remember to configure the Notify and Subfinder tools to work properly.
Use
Source: https://github.com/robotshell/