Image: Check Point
Magnet Goblin is a financially motivated threat actor demonstrating proficiency in swiftly exploiting 1-day software vulnerabilities to gain a foothold in target environments. Their opportunistic approach targets a range of edge devices and enterprise software, with primary tools including custom Linux malware and repurposed commercial software.
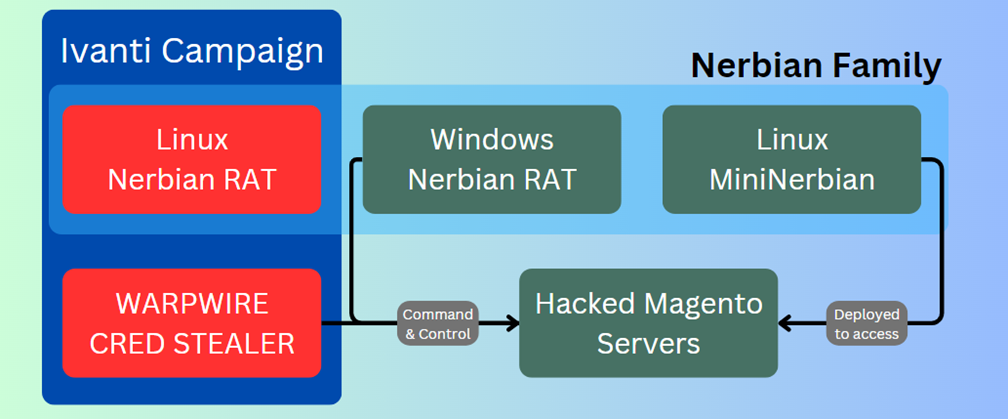
Critical vulnerabilities (CVE-2023-46805 and CVE-2023-21887) in Ivanti Connect Secure VPN, disclosed on January 10, 2024, spurred swift exploitation by numerous threat actors. Check Point Research isolated a unique campaign linked to a threat actor designated Magnet Goblin.

Magnet Goblin’s repertoire includes the Nerbian family of malware, with NerbianRAT, a cross-platform Remote Access Trojan (RAT), and MiniNerbian, a diminutive yet potent Linux backdoor. These tools are part of a broader strategy that exploits vulnerabilities in not just Ivanti’s offerings but also other high-profile platforms such as Magento (CVE-2022-24086), Qlik Sense (CVE-2023-41265, CVE-2023-41266, and CVE-2023-48365), and potentially Apache ActiveMQ.
The recent Ivanti exploitation shed light on Magnet Goblin’s methodology, characterized by the deployment of an ELF file housing the Linux variant of NerbianRAT. This variant, alongside tools like the WARPWIRE JavaScript credential stealer and Ligolo, an open-source tunneling tool, exemplifies the threat actor’s diverse toolkit aimed at infiltrating systems and exfiltrating sensitive information.
Magnet Goblin’s activities are not restricted to a single vector. Throughout 2022, Magento servers fell victim to their schemes, serving both as entry points and command-and-control (C2) servers. The exploitation of Qlik Sense vulnerabilities further underscores their opportunistic nature, leveraging every possible breach to further their malicious objectives.
The Linux variant of NerbianRAT reveals a stark lack of protective measures, indicating a preference for swift deployment over stealth. Its primary function includes collecting basic system information and establishing communication with its C2 server. The malware exhibits a certain level of sophistication, with encrypted network communication and configurable parameters that dictate its operational parameters.
MiniNerbian, on the other hand, simplifies command execution, utilizing HTTP for communication. This backdoor, despite its reduced footprint, aligns with the broader objectives of Magnet Goblin, facilitating system infiltration and control while remaining under the radar.
The financial motivation behind Magnet Goblin’s activities is evident through their target selection and rapid exploitation of emerging vulnerabilities. Their focus on edge devices and the deployment of custom Linux malware underscores a strategic approach to cybercrime, exploiting less guarded entry points for monetary gain.
While Magnet Goblin has been linked to numerous exploit campaigns, the group’s true identity remains unknown. Similarities in TTPs (Tactics, Techniques, and Procedures) have raised the possibility of connections to established ransomware operators, however, this remains speculative.