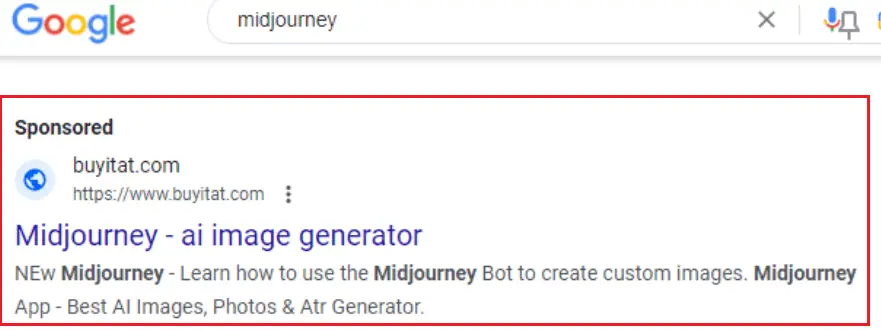
Malicious ads that appear on the search results page when using the keyword “midjourney” | Image: Trend Micro
In a swiftly evolving digital landscape, threat actors are capitalizing on the popularity of Artificial Intelligence (AI) tools, leveraging them as conduits for elaborate social engineering stratagems. According to recent findings from Trend Micro, these cybercriminals aim to dupe unsuspecting victims into downloading malicious software, leading to the deployment of stealers like Vidar and Redline.
The researchers noted a marked increase in malicious advertisement campaigns circulating within Google’s search engine, all bearing themes related to AI tools. A case in point was when users searched for the keyword “midjourney” (an AI tool that generates images from natural language descriptions), they were served with deceptive sponsored ads.

Upon clicking these ads, the user’s IP address is forwarded to a backend server, triggering the delivery of a malicious webpage. Some of these deceptive advertisements are designed to evade detection by filtering bots visiting the malevolent domain. If the visitor’s IP address is blocked or entered directly, a benign version of the domain is displayed.
To ensure undetected communication with its command-and-control (C&C) server, the campaign cunningly exploits Telegram’s API. This innovative tactic ensures network communication seamlessly blends with regular traffic, thereby circumventing network detection.
On downloading and executing the misleading installer, a spurious installation window is displayed while a malevolent PowerShell download process runs unnoticed in the background. This should serve as a warning for users since a desktop version of Midjourney does not exist.
The infection chain of the campaign leads to the PowerShell script execution, which can be proactively blocked by Trend Micro’s Behavior Monitoring Solution. As the campaign unfolds, victims are led to a Redline stealer after downloading and executing the counterfeit Midjourney installer.
The installer attempts to execute an obfuscated PowerShell script which subsequently downloads and executes the Redline payload from a remote server. Following the execution, the Redline stealer proceeds with the exfiltration of sensitive information, including browser cookies, passwords, cryptocurrency wallet data, and file information.
The findings underscore the importance of constant vigilance and cautious online behavior. Organizations and individuals should avoid engaging with suspicious ads and unverified applications to thwart potential malware infections. Furthermore, it’s essential to be aware that many AI tools, such as ChatGPT and Midjourney, don’t offer desktop versions, and any such offers should be regarded as potential threats.