Image: Socket
Researchers from Socket have uncovered a malicious typosquatting campaign infiltrating the Go ecosystem, using fraudulent packages that install hidden malware loaders. These rogue packages, designed to target Linux and macOS systems, pose a significant supply chain risk, particularly for developers working in financial and enterprise environments.
The attackers employed typosquatting, a tactic where malicious packages mimic legitimate ones, tricking developers into installing them.
One such example is github.com/shallowmulti/hypert, which impersonates the legitimate github.com/areknoster/hypert—a widely used Go library for testing HTTP APIs.
“In February 2025, the threat actor released four malicious packages on the Go Module Mirror that impersonate the legitimate github.com/areknoster/hypert library,” warn Socket researchers.
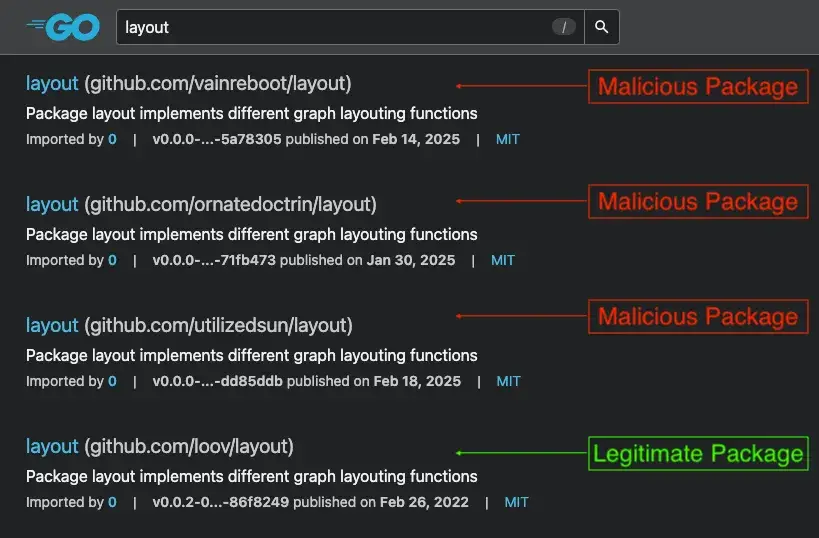
Similarly, three additional malicious packages—github.com/vainreboot/layout, github.com/ornatedoctrin/layout, and github.com/utilizedsun/layout—were found impersonating github.com/loov/layout, another trusted Go library.
These fake packages were uploaded between January and February 2025, indicating a coordinated effort to exploit the Go Module ecosystem.
Once installed, these rogue packages silently execute malicious code upon import, leveraging an array-based obfuscation technique to evade detection.
For instance, in github.com/shallowmulti/hypert, the function qcJjJne() is automatically triggered upon import:
This function executes a shell command that downloads and runs a remote script from alturastreet[.]icu, an attacker-controlled domain:
According to Socket researchers, this method ensures automatic malware execution the moment a developer includes the package in their project, making detection more challenging.
Once the malicious script is executed, it downloads and installs a stealthy ELF file (f0eee999), designed to run in the background on Linux and macOS systems.
The script follows a delayed execution method, likely to evade sandbox analysis:
By delaying execution for an hour, the malware avoids immediate detection and only runs after a set period, making it harder for security tools to trace.
Interestingly, the malicious domain alturastreet[.]icu appears to mimic Altura Credit Union’s legitimate website (alturacu.com), suggesting a potential financial-sector targeting strategy.
This raises concerns that threat actors are not only targeting Go developers but may also be attempting to infiltrate financial institutions through software supply chain compromises.
Developers using Go modules from unverified sources are at risk, particularly those working with:
- Open-source Go packages
- Enterprise applications and APIs
- Continuous Integration/Continuous Deployment (CI/CD) pipelines
- Financial software development
Since these malicious packages remain accessible on the Go Module Mirror, developers must manually verify their package sources before installation.
Related Posts:
- C&C in the Clouds: OilRig Group Hijacks Microsoft Services for Espionage
- Silver Fox APT Targets Organizations with PNGPlug and ValleyRAT Malware
- Python Developers Targeted in Massive Supply Chain Attack; Over 170,000 Users Affected