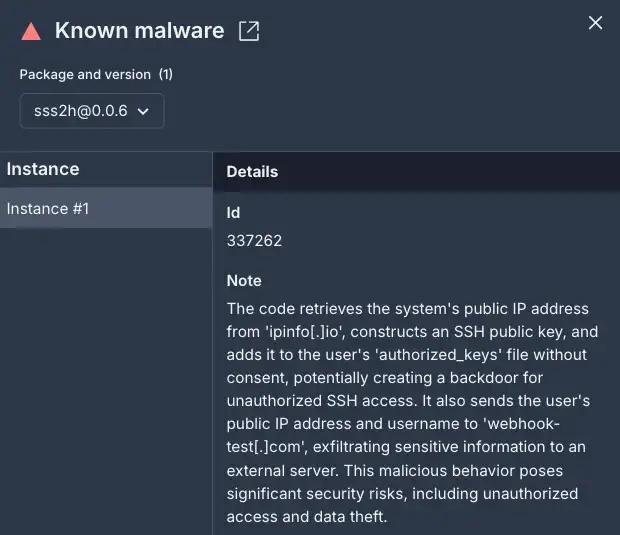
Socket AI Scanner’s description with additional context for the malicious “sss2h” package | Image: Socket
The developer community should be vigilant by the discovery of six malicious npm packages masquerading as popular libraries. According to a recent report by Socket’s threat research team, these packages exploit typographical errors to infiltrate developers’ systems and inject SSH backdoors.
The malicious packages—babelcl, chokader, streamserch, sss2h, npmrunnall, and node-pyt—were crafted by the threat actor “sanchezjosephine180” to resemble well-known npm libraries such as babel-cli, chokidar, and ssh2. With over 700 downloads before being flagged, these packages silently compromised developer environments. Socket described the campaign, stating: “The threat actor exploits common typing errors and abuses the postinstall script to distribute malicious code aimed to compromise developers and organizations.”
The attack relies on npm’s postinstall script, which executes immediately after a package is installed. Once triggered, the script installs a legitimate library alongside a malicious backdoor, masking its intent. The malicious payload adds the attacker’s SSH public key to the user’s authorized_keys file, granting unauthorized access. As Socket highlighted: “An unauthorized SSH key does not just open a door — it creates a hidden pathway for attackers to infiltrate and threaten the very foundation of the organization’s digital fortress.”
The stolen credentials and system information are sent to a remote server via a seemingly benign domain, webhook-test.com, enabling attackers to establish SSH connections without raising alarms. This clever use of a legitimate service obfuscates the attacker’s trail, complicating detection and attribution.
Among the findings was a seventh package, parimiko, designed to resemble the Python SSH library paramiko. Though currently benign, this package raises alarms. Socket warns: “By publishing a benign package, the threat actor may try to build a facade of legitimacy, making it easier to distribute malicious code in the future.”
Developers incorporating parimiko without strict version control could unknowingly install malicious updates later, exposing their projects to future compromises.
The discovery underscores the urgent need for enhanced security measures across the open-source ecosystem. As Socket aptly concludes: “The developer community must adopt proactive security measures, stay informed about emerging threats, and cultivate a culture of vigilance in managing software supply chains.”
Related Posts:
- npm’s Hidden Threat: The Covert Trojan Lurking in Your Windows System
- North Korean Cyberattacks Persist: Developers Targeted via npm
- Major npm flaw crashes Linux Systems, force users to reinstall
- SentinelOne Unveils: The Hidden Dangers of npm in Business Security
