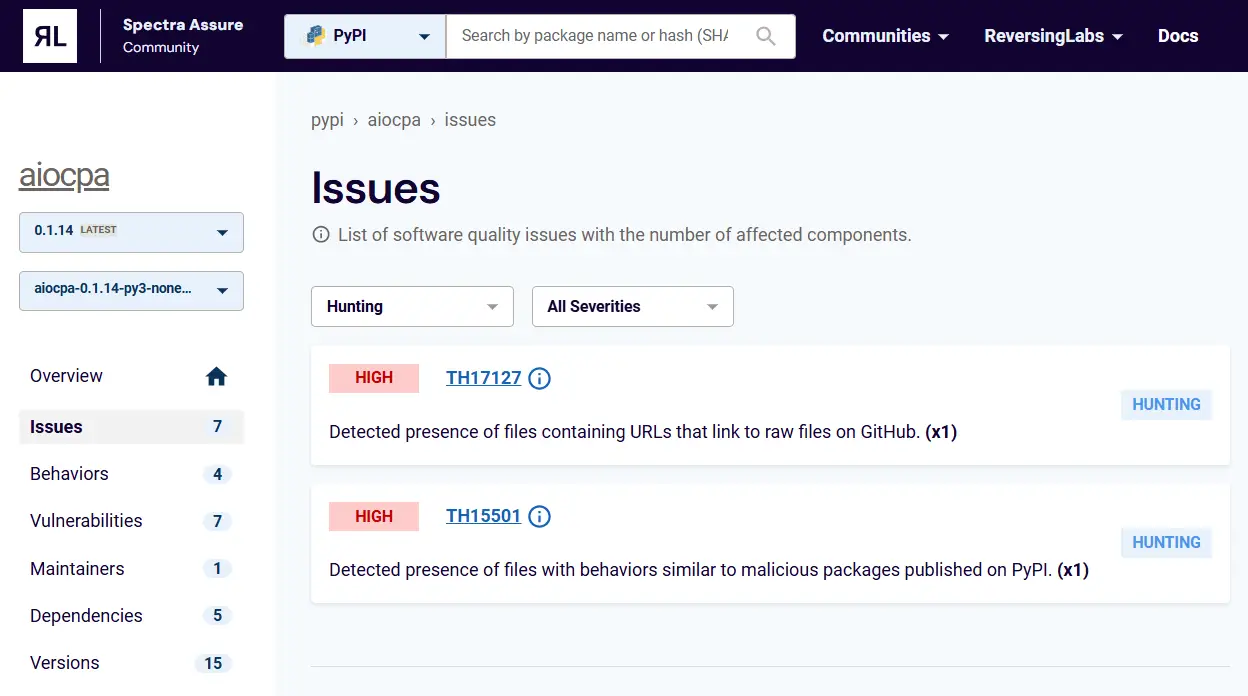
ML Threat Hunting policy violation | Image: ReversingLabs
Cybersecurity researchers at ReversingLabs have uncovered a stealthy supply chain attack targeting cryptocurrency wallets via the PyPI repository. The malicious package, named aiocpa, posed as a legitimate crypto client tool, exposing sensitive user information to attackers. ReversingLabs immediately reported the threat to PyPI, leading to its removal.
ReversingLabs’ advanced machine-learning threat detection platform identified the malicious package on November 21. Unlike typical attacks involving typosquatting or impersonation, the threat actors behind aiocpa adopted a subtler approach. They published their own crypto client package to build user trust before compromising them with malicious updates.
“A regular developer trying to make a security assessment… would not be able to judge this package as suspicious,” stated the ReversingLabs report.
The malicious code was hidden within the utils/sync.py file of aiocpa, employing multiple layers of obfuscation such as Base64 encoding and zlib compression. Upon deobfuscation, researchers uncovered a wrapper around the CryptoPay initialization function, exfiltrating sensitive data such as cryptocurrency trading tokens to a remote Telegram bot.
This strategic exploitation was further evident in the versions 0.1.13 and 0.1.14 of aiocpa, where malicious functionality was surreptitiously added. Notably, this code was absent from the package’s GitHub repository, evading traditional source code audits.
The attackers also attempted to take over the existing PyPI package pay, highlighting a growing threat vector in software supply chain attacks. As ReversingLabs noted, “Would you be able to detect such a change? Would it get automatically propagated to your software solution?”
ReversingLabs emphasized that even well-maintained projects with legitimate contributors are not immune to compromise. This case reinforces the importance of advanced security assessments, as traditional methods are no longer sufficient.
“Dedicated tools need to be incorporated into your development process to help prevent these threats and mitigate related risks,” the report concluded.
Related Posts:
- Malicious Update in Python Crypto Library Targets Private Keys via Telegram
- Developers Beware: Supply Chain Attacks Target Visual Studio Code Extensions
- PyPI Poisoned: 116 Malicious Packages Target Windows and Linux
- PyPI’s New Rule: 2FA Verification for All Project Maintainers
- Malicious NuGet Campaign Exploits Homoglyphs and Code Injection to Fool Developers