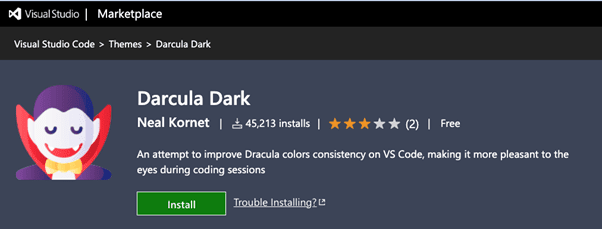
The extension description from the VSCode marketplace
Visual Studio Code (VSCode), a free source code editor developed by Microsoft, is celebrated for its efficiency and customizability, supporting a wide array of programming languages, frameworks, and tools. A leading attraction is the VSCode Extensions Marketplace, a treasure trove of official Microsoft and community-developed extensions that add new features, support new languages, and integrate with external tools and services. However, the Marketplace, boasting approximately 50,000 extensions, is not immune to potential security risks posed by malicious extensions.
These malignant add-ons may install malware, steal user data, or undertake other harmful actions. Microsoft combats this potential security risk with automatic extension scanning tools and user review systems, maintaining the integrity of the marketplace and the safety of its users. While these efforts have effectively curtailed the proliferation of malicious extensions, threat actors persist in their attempts to infiltrate and infect users through open-source code components.
In light of these potential risks, researchers from Check Point embarked on a mission to uncover potentially malicious VSCode extensions. Their findings revealed several suspicious extensions with over 45,000 installs, which were promptly reported to the VSCode team and subsequently removed.
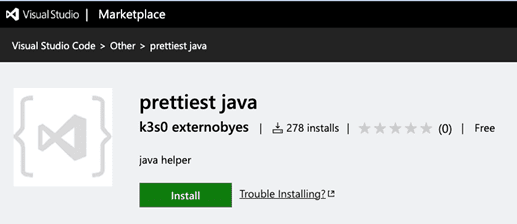
Among the detected malignant extensions was ‘prettiest java’, masquerading as a benign ‘java helper’, which exhibited classic PII stealer code, a type commonly found in the PyPI distribution. Another extension, ‘Theme Darcula dark’, was supposed to improve color consistency but instead contained PII stealer code. Lastly, ‘python-vscode’ used obfuscated statements to inject harmful code into the installer’s machine, deceitfully attracting users with its misleading name suggesting Python development enablement in VSCode.

However, the investigation didn’t end with clearly malicious extensions. There were numerous cases where extensions exhibited suspicious code patterns, yet weren’t definitively harmful. Noteworthy instances included those using private registries to silently install potentially malicious packages and those downloading resources from general IP addresses.
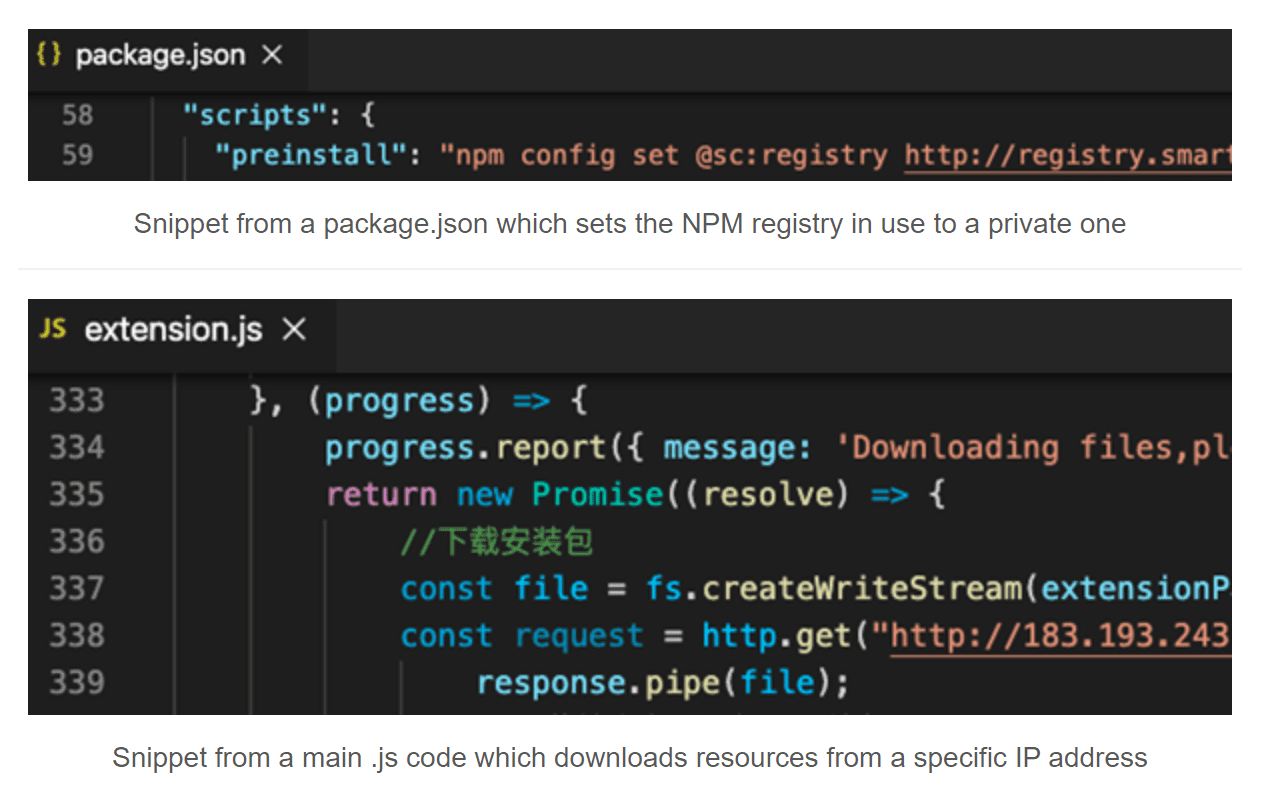
These findings underline the imperative for developers to verify every open-source component, rather than assuming safety, as malicious actors continue to find ways to infiltrate even the most reputable platforms. As the VSCode Extension Marketplace continues to expand, users must remain vigilant, and developers should work towards further strengthening security measures.