AMIRA: Automated Malware Incident Response & Analysis
AMIRA is a service for automatically running the analysis on the OSXCollector output files. The automated analysis is performed via OSXCollector Output Filters, in particular, The One Filter to Rule Them All: the Analyze Filter. AMIRA takes care of retrieving the output files from an S3 bucket, running the Analyze Filter, and then uploading the results of the analysis back to S3 (although one could envision as well attaching them to the related JIRA ticket).
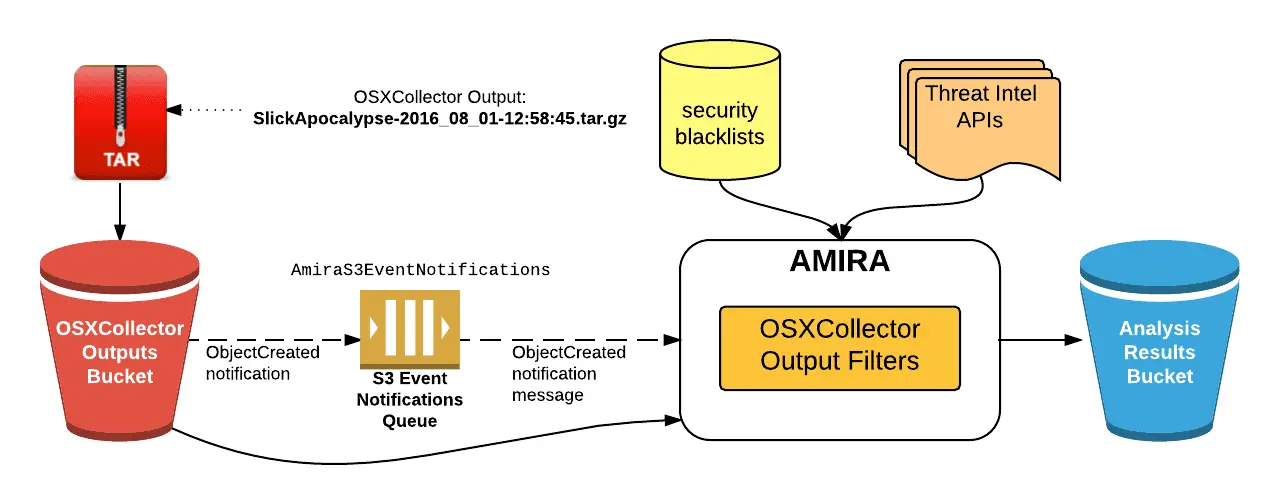
AMIRA Architecture
The service uses the S3 bucket event notifications to trigger the analysis. You will need to configure an S3 bucket for the OSXCollector output files so that when a file is added there the notification will be sent to an SQS queue (AmiraS3EventNotifications in the picture below). AMIRA periodically checks the queue for any new messages and upon receiving one it will fetch the OSXCollector output file from the S3 bucket. It will then run the Analyze Filter on the retrieved file.
The Analyze Filter runs all the filters contained in the OSXCollector Output Filters package sequentially. Some of them communicate with the external resources, like domain and hashes blacklists (or whitelists) and threat intel APIs, e.g. VirusTotal, OpenDNS Investigate or ShadowServer. The original OSXCollector output is extended with all of this information and the very last filter run by the Analyze Filter summarizes all of the findings into a human-readable form. After the filter finishes running, the results of the analysis will be uploaded to the Analysis Results S3 bucket.
The overview of the whole process and the system components involved in it are depicted below:

Install && Use
Copyright (c) 2016 Yelp Inc.