MalwLess v2.3 releases: Test Blue Team detections without running any attack

MalwLess Simulation Tool (MST)
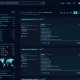
MalwLess is an open source tool that allows you to simulate system compromise or attack behaviors without running processes or PoCs. The tool is designed to test Blue Team detections and SIEM correlation rules. It provides a framework based on rules that anyone can write, so when a new technique or attack comes out you can write your own rules and share it a with the community.
These rules can simulate Sysmon or PowerShell events. MalwLess can parse the rules and write them directly to the Windows EventLog, then you can forward it to your event collector.
Changelog v2.3
- Merge pull request #9 from n0dec/fix01
- fixing contents field
Requirements
It is necessary to have sysmon installed in your system.
Use
Commands
To test the default rule set which is on rule_test.json just download it and run:
> malwless.exe
If you want to test a different rule set file, use the -r parameter:
> malwless.exe -r your_pack.json
To write a custom rule set check the writing sets section.
Creating rules
Anyone can create a rule. These are written in json with an easy format.
| key | values |
|---|---|
| enabled | If the value is set to true the event will be written. If it’s set to false just ignore the rule. |
| source | The source of the events. (Working on more supported sources…) Sysmon PowerShell |
| category | For each source, there is a list of different categories that can be specified. |
| description | A simple rule description. |
| payload | These are the values that will be added to the event. If you don’t indicate a specific payload the event will contain the values of the default configuration files located on conf. |
Rule example
Download
Copyright (C) 2018 n0dec
Source: https://github.com/n0dec/