Image: Zimperium
A new report from Zimperium zLabs reveals a sprawling and sophisticated Android malware campaign that has infected over 107,000 devices across 113 countries since February 2022. The malware, a silent SMS stealer, targets one-time passwords (OTPs) from over 600 top-tier brands, potentially compromising millions of users’ accounts.
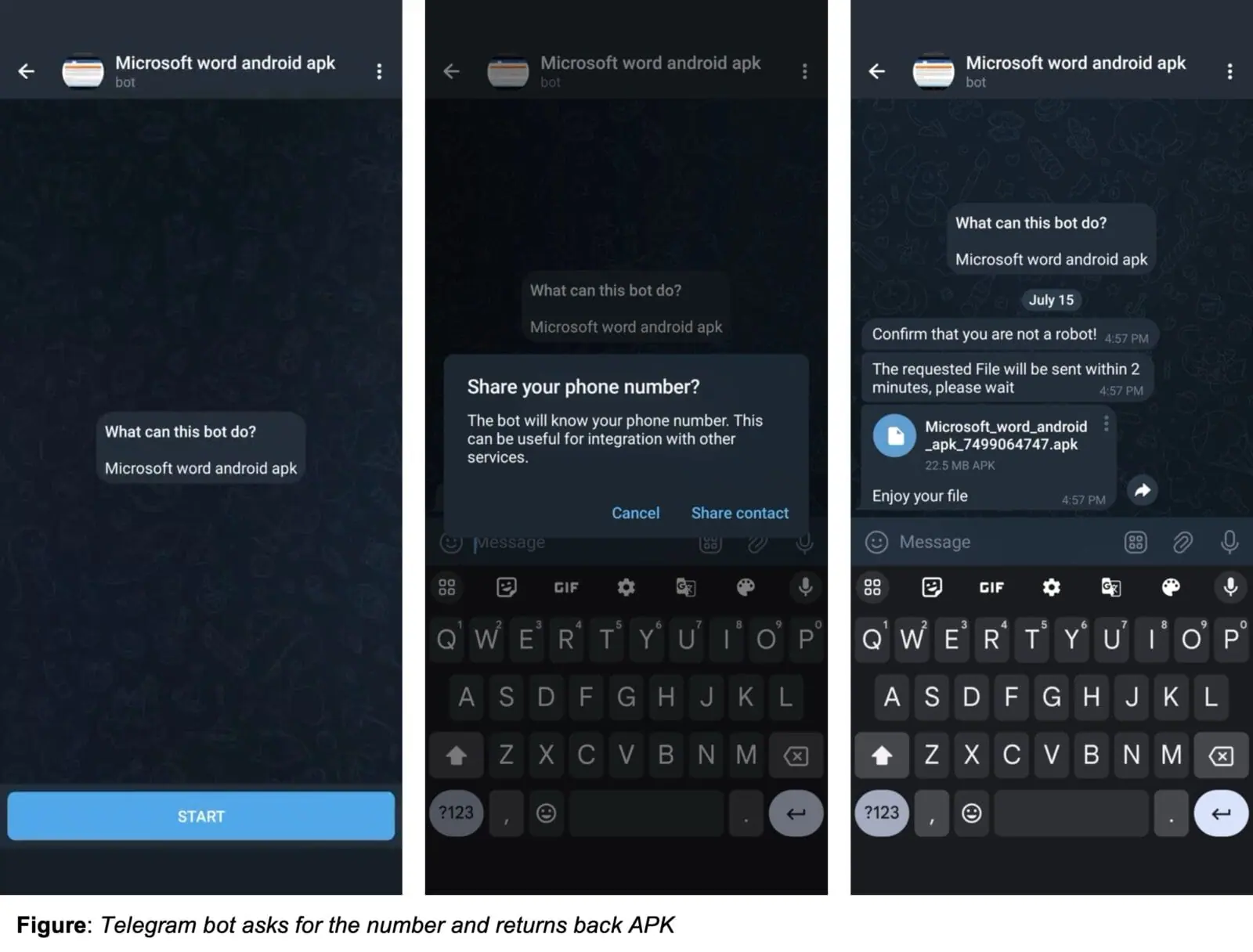
The campaign utilizes a multi-pronged approach to infect victims, including deceptive advertisements and Telegram bots. Once installed, the malware requests SMS read permissions, allowing it to intercept and transmit OTPs to its command-and-control (C&C) server. The stolen OTPs are then sold on a cybercrime marketplace, enabling attackers to bypass two-factor authentication and gain unauthorized access to victims’ accounts.
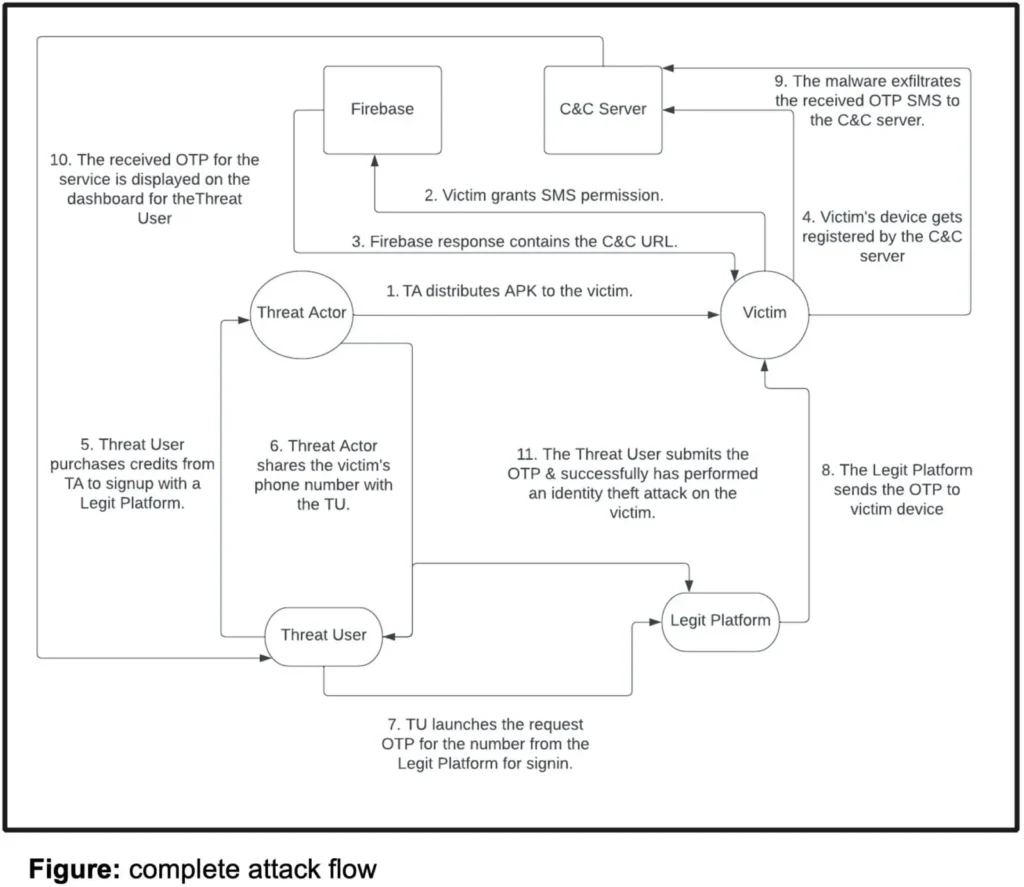
The threat actors have transitioned from using Firebase for C&C communication to utilizing GitHub repositories and even embedding C&C addresses directly within the apps. Furthermore, Zimperium researchers discovered a clear financial motive behind the campaign, linking one of the malware samples to a website offering stolen phone numbers and OTPs for various services.
The scale of this campaign is staggering:
- Over 107,000 Unique Malware Applications: Indicating a prolific campaign targeting numerous global victims.
- Over 95% of Malware Samples are Unknown or Unavailable: Over 99,000 samples were not found in common repositories.
- 60+ Top-tier Global Brand Services Targeted: Monitoring OTP messages across over 600 global brands.
- 113 Countries Affected: With Russia and India being primary targets.
- 13 Command and Control (C&C) Servers Identified: Used to steal and leak SMS messages.
- Extensive Telegram Bot Network: Approximately 2,600 bots linked to the campaign.
The scale of this campaign is alarming, with the majority of malware samples being unknown to antivirus software. The researchers identified 13 C&C servers and a vast network of Telegram bots involved in the distribution. While Russia and India were the primary targets, victims were found in 113 countries, underscoring the global reach of this threat.
To protect against this and similar threats, users are strongly advised to avoid sideloading apps from untrusted sources, exercise caution when clicking on links or interacting with Telegram bots, and keep their devices updated with the latest security patches. Enterprises should also implement robust mobile security solutions to detect and prevent such threats.
Related Posts:
- Facebook have been collecting call logs and SMS metadata for several years
- Microsoft365_devicePhish: Abusing Microsoft 365 OAuth Authorization Flow