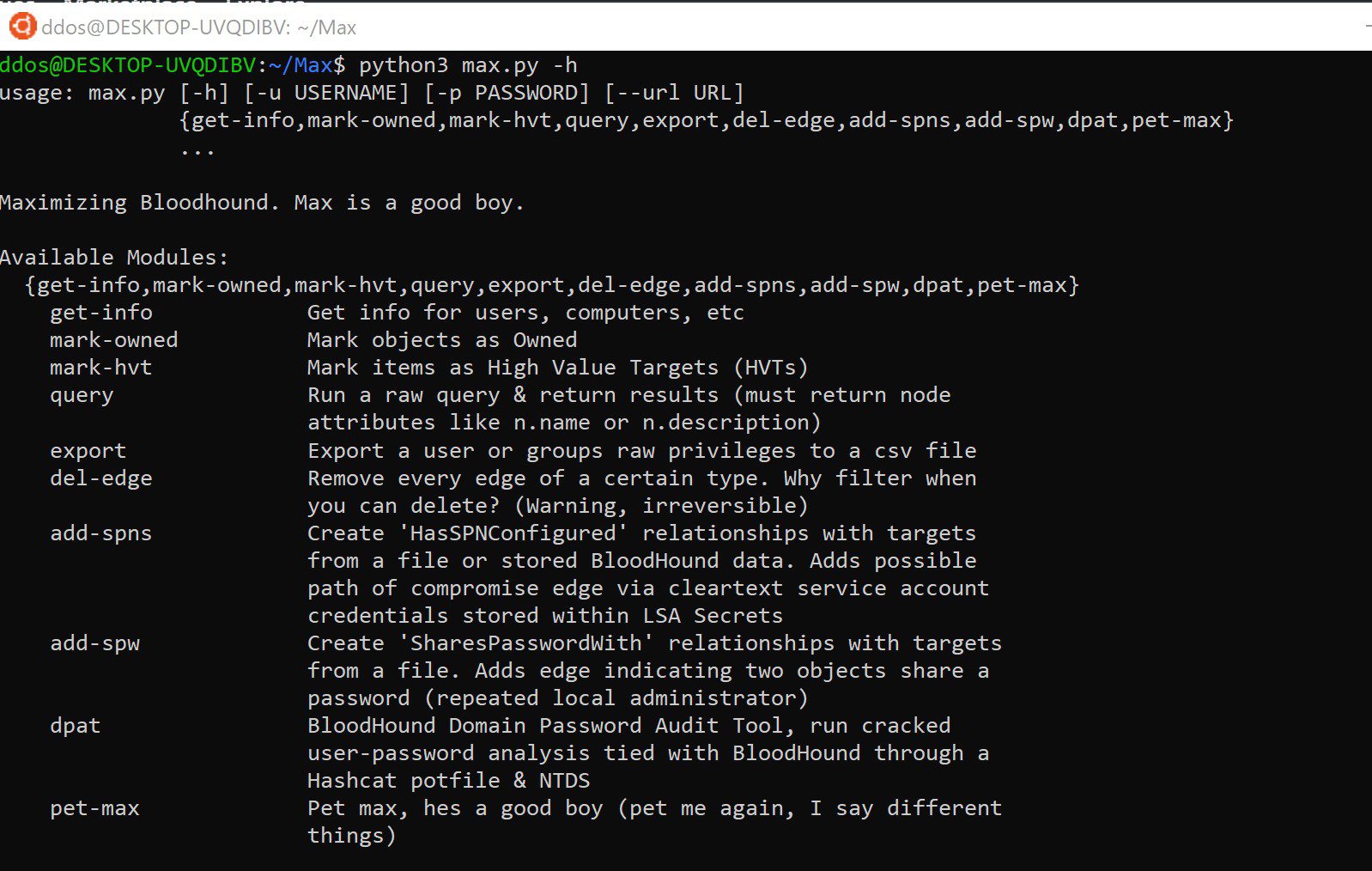
Maximizing BloodHound with a simple suite of tools
Description
New Release:
- dpat – The BloodHound Domain Password Audit Tool (DPAT)
A simple suite of tools:
- get-info – Pull lists of information from the Neo4j database
- mark-owned – Mark a list of objects as Owned
- mark-hvt – Mark a list of objects as High-Value Targets
- query – Run a raw Cypher query and return output
- export – Export all outbound controlling privileges of a domain object to a CSV file
- del-edge – Delete an edge from the database
- add-spns – Create HasSPNConfigured relationships, new attack primitive
- add-spw – Create SharesPasswordWith relationships
- dpat – The BloodHound Domain Password Audit Tool (DPAT)
- pet-max – Dogsay, happiness for stressful engagements
This was released with screenshots & use-cases on the following blogs: Max Release, Updates & Primitives & DPAT
A new potential attack primitive was added to this tool during my research, see the add-spns section for full details.
Install
git clone https://github.com/knavesec/Max.git
cd Max
pip3 install -r requirements.txt
Neo4j Creds
Neo4j credentials can be hardcoded at the beginning of the script OR they can be provided as CLI. If both areas are left blank, you will be prompted for the uname/password.
python3 max.py -u neo4j -p neo4j {module} {args}python3 max.py {module} {args} Neo4j Username: neo4j Neo4j Password:
Use
Importing owned objects into BH
python3 max.py mark-owned -f owned.txt python3 max.py mark-owned -f owned.txt --add-note "Owned by repeated local admin"
Get the list of users
python3 max.py get-info –users
python3 max.py get-info –users –enabledUSER01@DOMAIN.LOCAL
USER02@DOMAIN.LOCAL
…
Get the list of objects in a target group
python3 max.py get-info --group-members "domain controllers@domain.local"
Get a list of computers that a user has administrative rights to
python3 max.py get-info --adminto USER01@DOMAIN.LOCAL
Get a list of owned objects with the notes for each
python3 max.py get-info --owned --get-note
Running a query – return a list of all users with a path to DA
python3 max.py query “MATCH (n:User),(m:Group {name:’DOMAIN ADMINS@DOMAIN.LOCAL’}) MATCH (n)-[*1..]->(m) RETURN DISTINCT(n.name)”
Delete an edge from the database
python3 max.py del-edge CanRDP
Add HasSPNConfigured relationship using the information stored within BloodHound, or with a GetUserSPNs impacket file
python3 max.py add-spns -b python3 max.py add-spns -i getuserspns-raw-output.txt
DPAT
python3 max.py dpat -n ~/client/ntds.dit -p ~/.hashcat/hashcat.potfile -o ouputdir –html –sanitize
Pet max
python3 max.py pet-max
Object Files & Specification
Objects in file must contain FQDN within, capitalization does not matter. This also applies to whenever a CLI username/computer name is supplied.