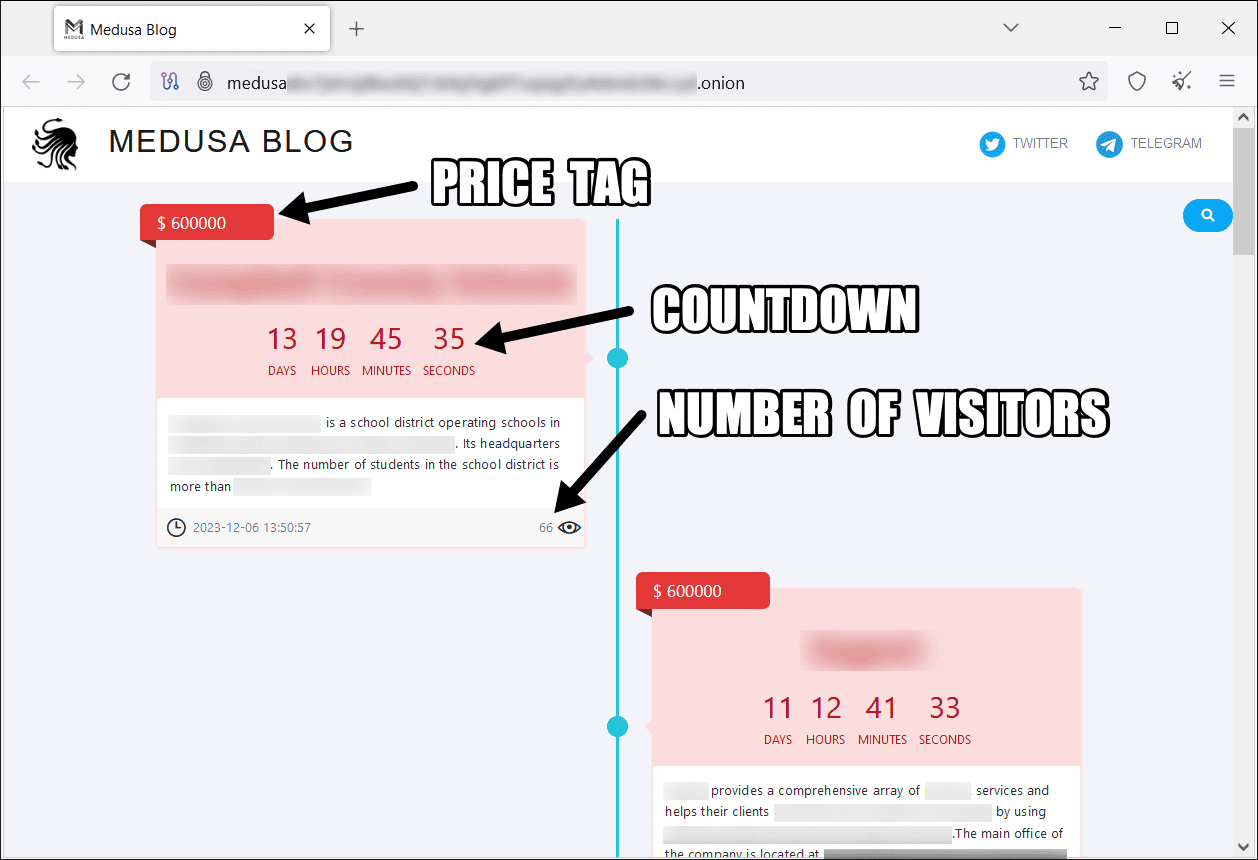
Medusa Blog dedicated leak site
The Medusa ransomware has emerged as a formidable adversary. Originating as a Ransomware-as-a-Service (RaaS) in late 2022, Medusa has rapidly evolved, primarily targeting Windows environments. This malicious software represents a significant escalation in ransomware activities, marked by a disturbing shift towards multifaceted extortion tactics.
Early 2023 saw the launch of the Medusa Blog, a dedicated leak site on the dark web. This platform serves as a chilling showcase for sensitive data from non-compliant victims. The Medusa ransomware group leverages this site to exert pressure, offering victims various costly options for data extension, deletion, or download.

Beyond the anonymity of the dark web, Medusa extends its reach through a public Telegram channel, aptly named “information support.” This channel serves as a more accessible medium for sharing files from compromised organizations, intensifying the threat’s visibility and reach.
Medusa’s modus operandi involves exploiting vulnerable services and hijacking legitimate accounts, often utilizing initial access brokers for infiltration. The group employs living-off-the-land techniques, using legitimate software for malicious purposes. This method blends in with regular traffic, making detection challenging.
Medusa’s indiscriminate approach has impacted a diverse range of sectors worldwide, with a substantial number of incidents occurring in the United States and Europe. Its global footprint underscores the universal threat posed by such ransomware actors.
Unit 42 Incident Response Team’s investigation into a Medusa ransomware incident has unveiled intricate tactics, tools, and procedures. These include webshell placement, encrypted kernel drivers, and novel applications of netscan tools. Medusa’s gaze leads to file encryption, leaving the ominous .medusa file extension in its wake.
The emergence of Medusa ransomware marks a significant evolution in the cyber threat landscape. Its complex propagation methods, coupled with transparent pressure tactics, demand a more proactive and robust defensive strategy from organizations worldwide.