Malware infection routine | Image Credit: Trendmicro
In a fresh revelation, cybersecurity mavens from Trend Micro have shed light on a novel malware attributed to the notorious APT34 group. This malware, baptized “Menorah,” was spotted playing a crucial role in a recent targeted phishing attack, demonstrating the group’s undiminished proclivity for cyber subterfuge.
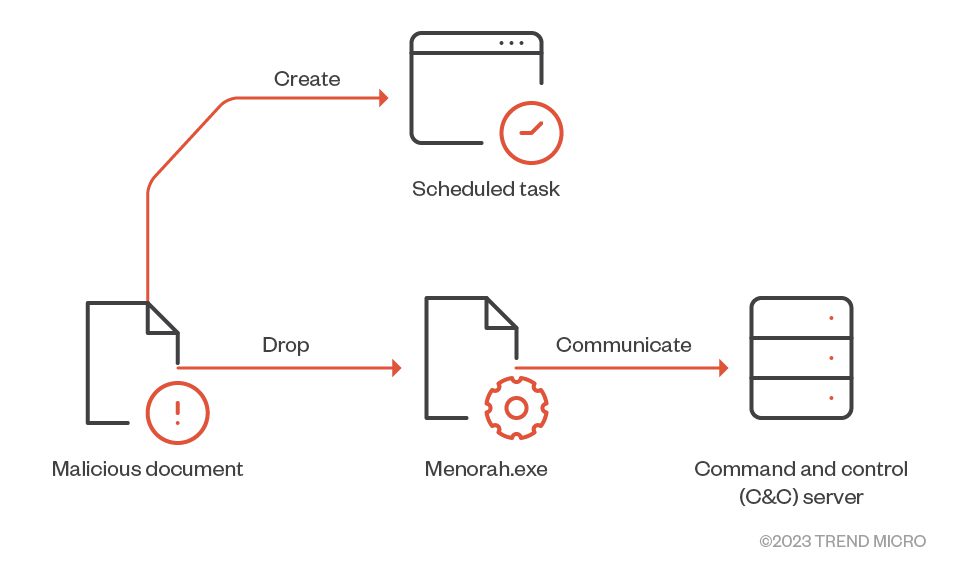
When opened, a document named “MyCv.doc” was discerned to be the vector. Surprisingly, the document hinted at connections to the Seychelles Licensing Authority. Yet, it intriguingly contained pricing in Saudi Riyal, suggesting potential victims within Saudi Arabia’s boundaries. Once the document is accessed, Menorah malware gets to work. This malicious software is not just any run-of-the-mill malware; it’s purpose-built for cyberespionage. It assiduously identifies its host machine, peruses files, and even paves the way for additional malicious software, thereby ensuring its unrelenting presence.

For the uninitiated, APT34 is no ordinary cyber threat. It’s a group that’s garnered notoriety for its covert operations, primarily targeting the Middle East’s nerve centers. Their extensive resume boasts cyberattacks against high-profile targets, including government institutions and critical infrastructure. Their modus operandi isn’t stagnant either; they consistently refine their techniques, always staying a step ahead. Notably, their recent exploits have witnessed an innovative shift in data exfiltration methods, with even a fresh variant of their famed SideTwist malware catching the attention of researchers from NSFOCUS.
APT34’s strategy is quite the masterstroke. By simply opening a document, victims unknowingly trigger a cascade of malicious activities. Menorah’s inner workings can be likened to a Swiss army knife of cyberespionage tools. It can deduce the machine’s identity, trawl through directories, ferry files to and from the compromised system, and even respond to direct commands.
To ensure its clandestine activities remain undetected, this new variant of SideTwist has honed its capabilities. It constantly checks its environment, ready to pull the plug should it sense a threat, ensuring the malware’s continued, stealthy operation.
While comparisons with a previous variant of SideTwist unveiled in 2021 by Checkpoint revealed significant commonalities, it’s clear that APT34’s evolution is ongoing. The digital fingerprints, communication protocols, and even the malicious modus operandi echo previous versions, yet the group’s increasing sophistication and versatility render them a persistent cyber adversary.
As the digital landscape grows more perilous with actors like APT34 lurking in the shadows, it becomes paramount for organizations and individuals to bolster their cyber defenses and remain ever-vigilant.