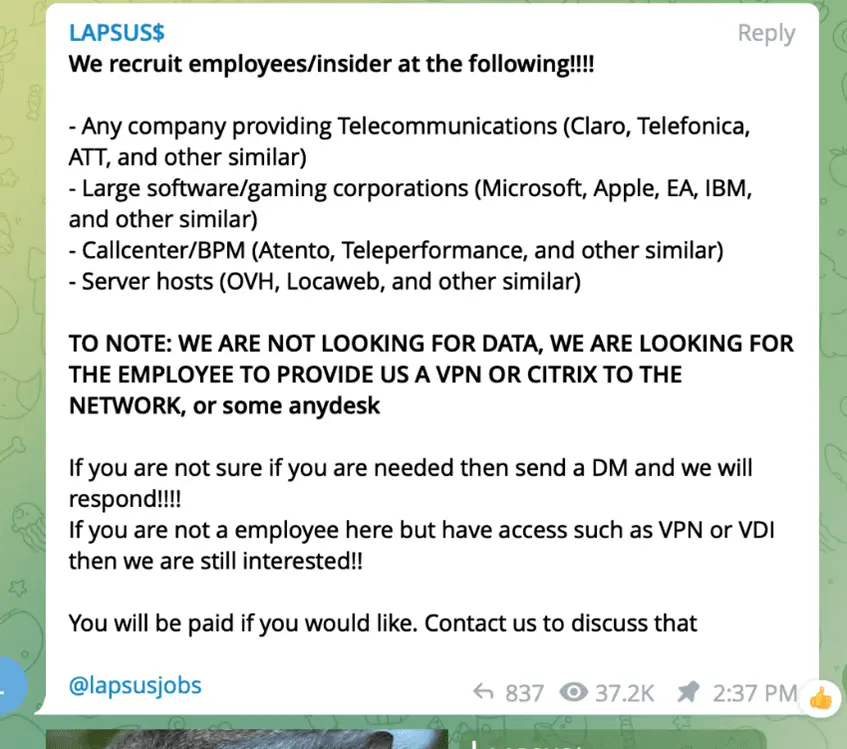

In some cases, DEV-0537 first targeted and compromised an individual’s personal or private (non-work-related) accounts giving them access to then look for additional credentials that could be used to gain access to corporate systems. Given that employees typically use these personal accounts or numbers as their second-factor authentication or password recovery, the group would often use this access to reset passwords and complete account recovery actions.
Microsoft makes the following recommendations for businesses:
DEV-0537 leverages legitimate credentials to perform malicious actions against customers. Since these credentials are legitimate, some activity performed might seem consistent with standard user behavior. Use the following recommendations to improve your cloud security posture:
- Review your Conditional Access user and session risk configurations:
- Block or force password reset for high/medium user risk for all users
- Block high sign-in risk logins for all users
- Block medium sign-in risk logins for privileged users
- Require MFA for medium sign-in risk logins for all other users
- Alerts should be configured to prompt a review on high-risk modification of tenant configuration, including but not limited to:
- Modification of Azure AD roles and privileged users associated with those roles
- Creation or modification of Exchange Online transport rules
- Modification of tenant-wide security configurations
- Review risk detections in Azure AD Identity Protection
- Risk detections highlight risky users and risky sign-ins
- Administrators can review and confirm individual sign-ins listed here as compromised or safe
- More information is available here on how to Investigate risk Azure AD Identity Protection