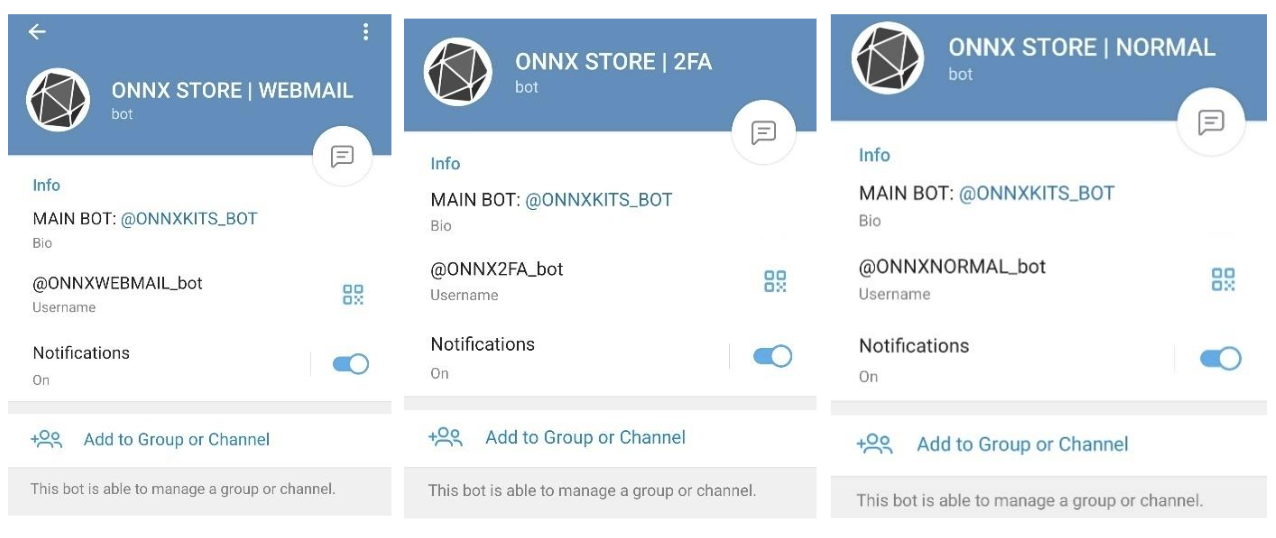
Fraudulent ONNX Store Telegram Channels | Image: Microsoft
Microsoft’s Digital Crimes Unit (DCU) has struck a significant blow against the cybercrime supply chain, seizing 240 fraudulent websites and disrupting a major player in the “Phishing-as-a-Service” (PhaaS) industry. This operation, fraudulently using the “ONNX” brand name, was responsible for a massive volume of phishing attacks, particularly targeting the financial services industry.
“While all sectors are at risk, the financial services industry has been heavily targeted given the sensitive data and transactions they handle,” said Steven Masada, Assistant General Counsel of Microsoft’s DCU, in a recent report. “In these instances, a successful phish can have devastating real-world consequences for the victims.”
The Egypt-based operation, led by Abanoub Nady (known online as “MRxC0DER”), developed and sold “do it yourself” phish kits, enabling even novice cybercriminals to launch sophisticated attacks. These kits were marketed through online storefronts and social media channels, complete with “how-to” videos and tiered subscription models.
One of the most concerning aspects of this operation was its focus on enabling “adversary-in-the-middle” (AiTM) phishing techniques, which bypass multifactor authentication (MFA) defenses. As Masada explained, “AiTM phishing attacks – where attackers secretly inject themselves in network communications to steal credentials and cookies used to authenticate users’ identity – have become highly favored, if not the ‘go-to’ method used by malicious actors to bypass the additional protections of Multifactor Authentication (MFA) defenses.”
The DCU’s action, in partnership with LF Projects, LLC (the legitimate owner of the ONNX trademark), redirects the malicious infrastructure to Microsoft, effectively severing access for the operators and their customers. This disruption is a crucial step in protecting users from financial fraud, data theft, and ransomware.
“This action builds on the DCU’s strategy of disrupting the broader cybercriminal ecosystem and targeting the tools cybercriminals use to launch their attacks,” Masada stated. “Our goal in all cases is to protect customers by severing bad actors from the infrastructure required to operate and to deter future cybercriminal behavior by significantly raising the barriers of entry and the cost of doing business.”
Related Posts:
- 2FA Bypass and More: Inside ONNX Store, the Phishing Threat to Your Finances
- Tycoon 2FA: The Evolving Threat Bypassing Multi-Factor Authentication
- Beware the Bite of Mamba 2FA: This Phishing Kit Bypasses 2FA
- Greatness: A Sophisticated New Phishing-as-a-Service Revealed
- Tycoon Group Exposes Risks of Phishing-as-a-Service Model