General depiction of the four stages | Image: Microsoft
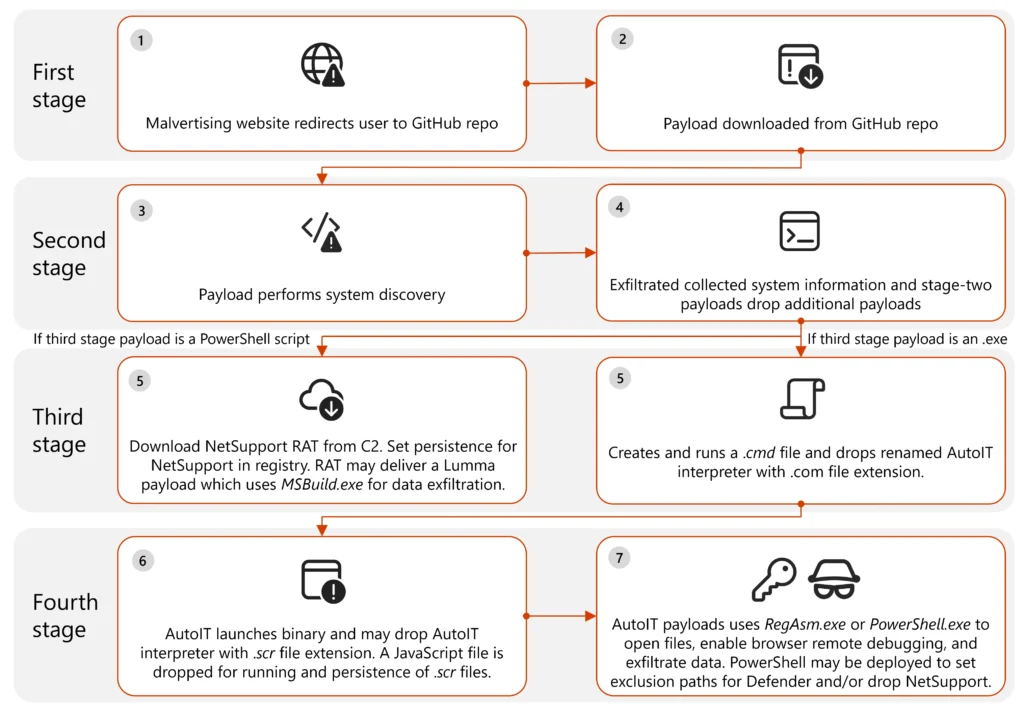
In early December 2024, Microsoft Threat Intelligence uncovered a large-scale malvertising campaign that infected nearly one million devices globally. This attack, originating from illegal streaming websites, leveraged malicious advertisements to redirect unsuspecting users through multiple domains before ultimately delivering information-stealing malware hosted on GitHub.
According to Microsoft’s analysis: “The attack originated from illegal streaming websites embedded with malvertising redirectors, leading to an intermediary website where the user was then redirected to GitHub and two other platforms.”
The threat actors utilized a multi-stage attack to gain an initial foothold, deploy secondary payloads, and establish persistence. GitHub was the primary platform used for hosting first-stage malware, though additional payloads were also observed on Discord and Dropbox.
Multiple stages of malware were deployed in this campaign:
- First-Stage Payload: Served as a dropper for subsequent malware, establishing an initial foothold.
- Second-Stage Payload: Conducted system discovery and exfiltrated data such as OS version, memory details, and user paths.
- Third-Stage Payload: Delivered information stealers (including Lumma Stealer and Doenerium) and deployed remote monitoring tools (NetSupport RMM).
- Fourth-Stage Payload: Used PowerShell scripts and LOLBAS techniques (e.g., MSBuild.exe, RegAsm.exe) to ensure persistence and conduct data exfiltration.
“Once the initial malware from GitHub gained a foothold on the device, the additional files deployed had a modular and multi-stage approach to payload delivery, execution, and persistence,” the report explains.
Microsoft researchers found that the malware employed several techniques to evade detection and maintain access:
- Registry Modification: Altered Windows Run keys to ensure malware execution on startup.
- Scheduled Tasks: Created hidden tasks for automated execution.
- Data Protection API (DPAPI) Exploitation: Used to decrypt stored browser credentials.
- Remote Monitoring & Keylogging: Deployed NetSupport RAT for ongoing surveillance.
Threat actors also monitored browser sessions and exfiltrated user credentials, targeting popular browsers like Chrome, Edge, and Firefox.
Microsoft collaborated with GitHub’s security team to take down the malicious repositories. However, they emphasized that similar campaigns may continue using alternative distribution platforms.
For a full list of Indicators of Compromise (IOCs) and detailed hunting guidance, refer to Microsoft’s official report.
Related Posts:
- Google Products Exploited in Sophisticated Malvertising Scheme
- Massive Illegal Streaming Network Dismantled in Europe-Wide Operation
- Google Ads Abused in Graphic Design Malvertising Attack
- Report: 120,000 computers were infected with information-stealing malware
- Beware of Fake AI Photo Editors on Social Media: Malvertising Campaign Targets Credentials