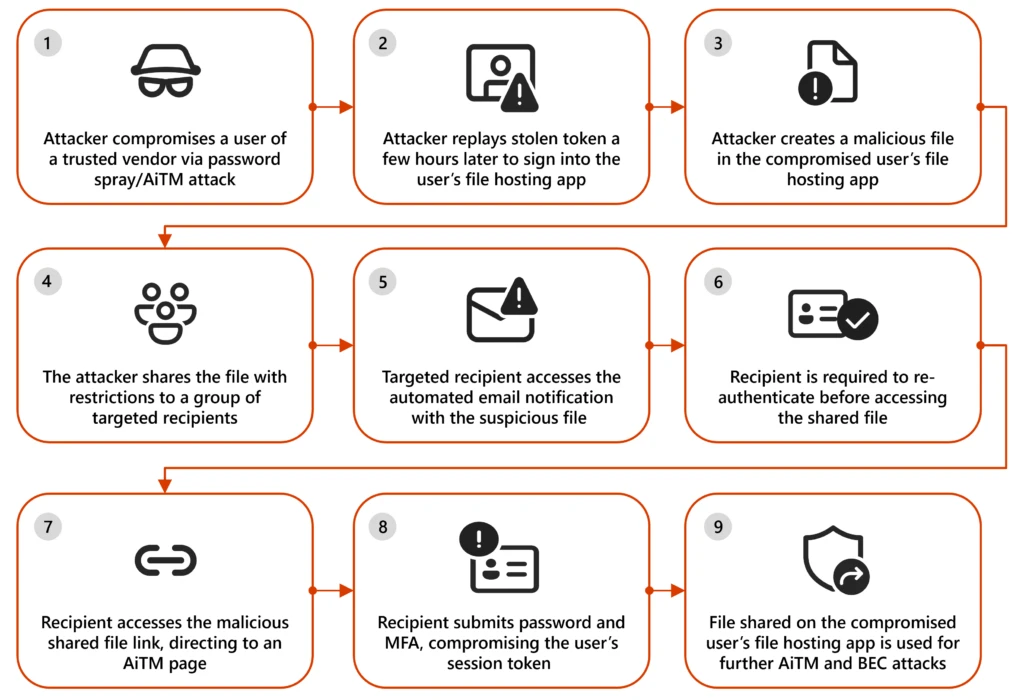
Example attack chain | Image: Microsoft
Microsoft Threat Intelligence has identified a rising trend of phishing campaigns exploiting legitimate file hosting services like SharePoint, OneDrive, and Dropbox to launch business email compromise (BEC) attacks. These campaigns, which began in mid-April 2024, use sophisticated defense evasion techniques to bypass security measures, resulting in the compromise of identities, devices, and often leading to financial fraud, data exfiltration, and lateral movement within organizations.
While file hosting services provide essential tools for businesses to store and share data, their widespread use also makes them attractive targets for threat actors. As Microsoft notes:
“Legitimate hosting services, such as SharePoint, OneDrive, and Dropbox, are widely used by organizations for storing, sharing, and collaborating on files. However, the widespread use of such services also makes them attractive targets for threat actors, who exploit the trust and familiarity associated with these services.”
In these campaigns, attackers often use social engineering to gain access to trusted accounts and then misuse these platforms to deliver malicious files or links to target organizations. This approach allows attackers to avoid traditional detection mechanisms, as the files appear to come from trusted sources, giving phishing emails an added layer of credibility.
Microsoft has observed the increasing use of restricted access and view-only files to evade detection by email security systems and malware analysis tools. These files are configured to ensure that only the intended recipient can access them, requiring re-authentication via email and a one-time password (OTP). Furthermore, the files are set to “view-only”, preventing downloads and hindering analysis:
“The files shared in these phishing attacks are set to ‘view-only’ mode, disabling the ability to download and consequently, the detection of embedded URLs within the file.”
These tactics make it difficult for security systems to scan the contents of the files or analyze the embedded malicious links, increasing the likelihood of a successful attack.
The attack typically begins with the compromise of a user account within a trusted vendor. The attacker then uploads a malicious file to the vendor’s file hosting service, sharing it with the target organization. Because the file is sent from a trusted source, the email is often allowed through security filters, making it more likely that the recipient will engage with the content. The report explains:
“Recipients are more likely to trust emails from known vendors, allowing threat actors to bypass security measures and compromise identities.”
In some cases, attackers impersonate trusted individuals, such as IT support or administrators, to further increase the credibility of the email. File names often create a sense of urgency or familiarity, with titles like “Urgent: Attention Required” or “Audit Report 2024”, designed to prompt users to open the files without hesitation.

Once the recipient opens the file and verifies their identity via the OTP, they are redirected to a malicious adversary-in-the-middle (AiTM) phishing page. Here, the user is asked to provide their password and complete multifactor authentication (MFA). The attacker then captures the session token, enabling further exploitation, including BEC attacks and lateral movement within the organization.