Image: zerodayinitiative
Threat actors constantly evolve their tactics and techniques to exploit new vulnerabilities. The Mirai botnet, a notorious malware strain responsible for numerous devastating DDoS attacks, has once again updated its arsenal, this time exploiting a recently patched vulnerability in TP-Link Archer AX21 Wi-Fi routers. The vulnerability, CVE-2023-1389 (CVSS score of 8.8), was discovered and disclosed by multiple teams during the Pwn2Own Toronto event.
The TP-Link Vulnerability: A Brief Overview
CVE-2023-1389 is an unauthenticated command injection vulnerability in the locale API available via the web management interface of TP-Link Archer AX21 Wi-Fi routers. The bug, which was disclosed by Team Viettel, Qrious Security, and Tenable during the Pwn2Own Toronto event, allows attackers to exploit a race condition issue related to iptable handling, enabling them to gain code execution. TP-Link released a firmware update addressing this and other vulnerabilities in March, shortly before exploit attempts were detected in the wild.
The Mirai Botnet Strikes Again
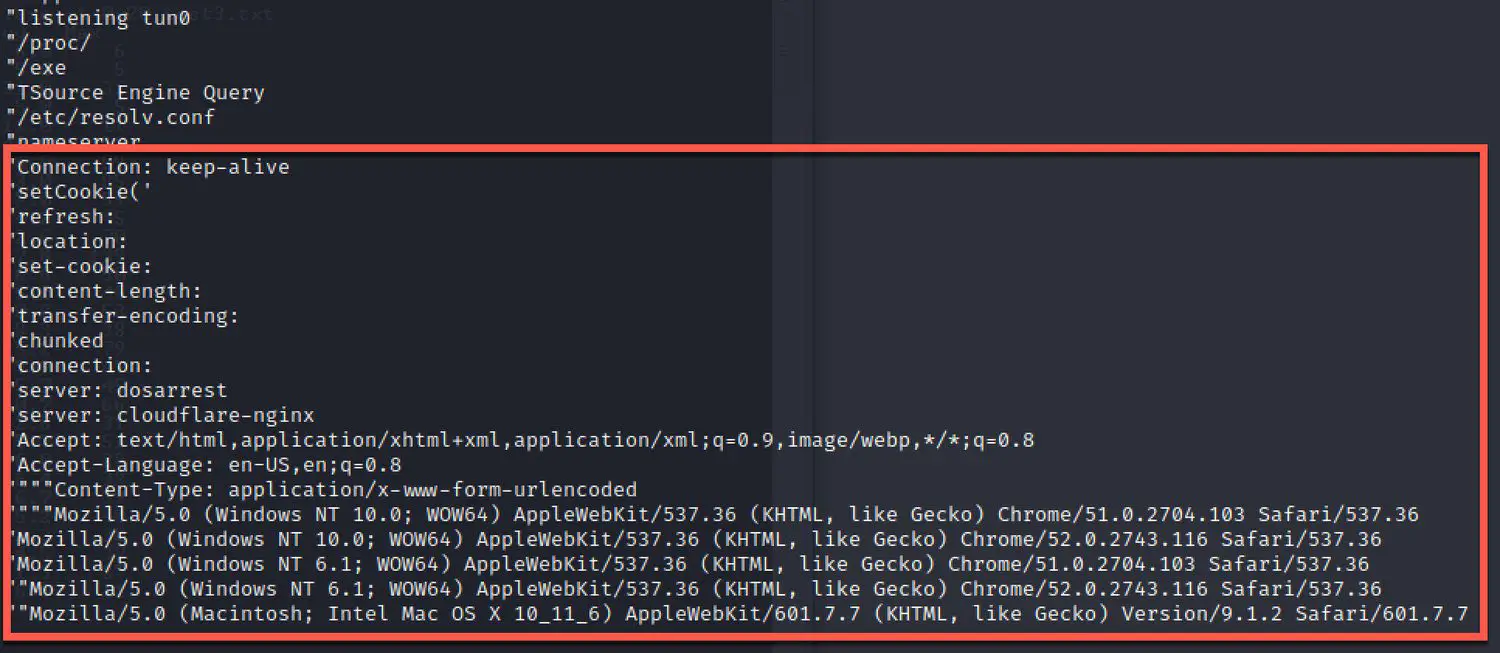
The Zero Day Initiative (ZDI) threat-hunting team revealed that starting April 11th, threat actors began publicly exploiting CVE-2023-1389. The initial activity targeted devices in Eastern Europe, but the attacks have since spread globally. The Mirai botnet exploits the vulnerability by making HTTP requests to its command and control (C2) servers, downloading and executing a series of binary payloads designed for various system architectures.

These payloads are then brute-forced to find the appropriate one for the target system architecture. Once installed, the host becomes fully infected and establishes a connection with the Mirai C2. Analysis of the payloads revealed that the attackers encrypt strings using 0x00 and 0x22 as XOR keys, with decrypted strings exposing Mirai bot attack functions and configuration details. Notably, the bot can launch Valve Source Engine (VSE) distributed denial-of-service (DDoS) attacks against game servers.
The Importance of Timely Patching
The swift exploitation of CVE-2023-1389 by the Mirai botnet underscores the decreasing “time-to-exploit” speed observed in the cybersecurity industry. Threat actors are quick to leverage newly discovered vulnerabilities, especially in IoT devices, to maintain their foothold in enterprise networks. This rapid response emphasizes the critical importance of timely patching to protect against such threats.