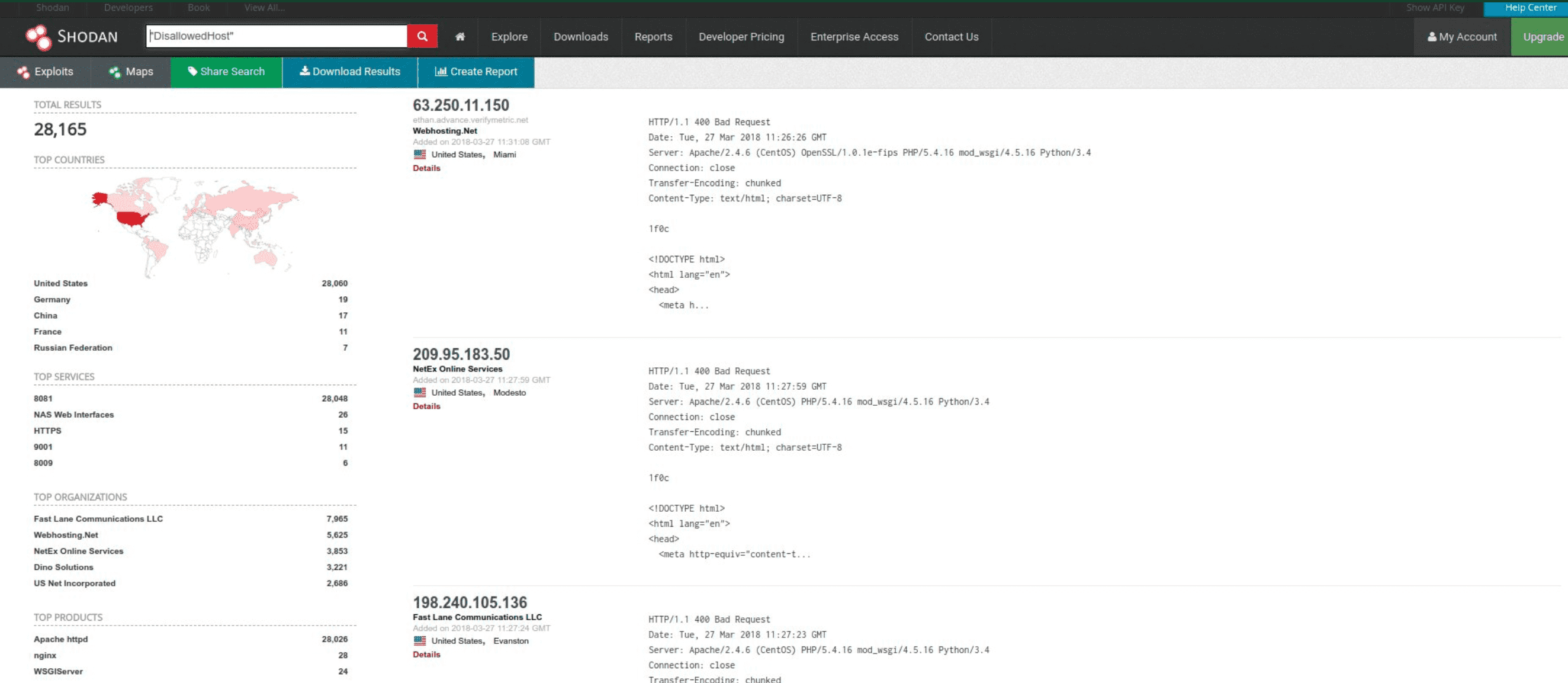
Recently, security researcher Fábio Castro discovered 28,165 misconfigured Django applications that exposed sensitive information, including passwords, API keys, and AWS access tokens. Fábio Castro stated that this was caused by Django developers forgetting to disable the debug mode. Hackers can use this leaked data to gain full control of the system.
Django is a very popular advanced Python web framework that can quickly develop Python-based web applications. However, when Castro used the Django framework on a small project, he found that its configuration was wrong. For security reasons, he suggested disabling debug mode when deploying the application to production.
After a cursory review of these servers, Castro discovered that such an application would expose some extremely sensitive information and could even allow potential attackers to access all the data stored on the server.
Castro points out that the deeper Django is being used on the server, the more exposed sensitive information may be. In some cases, the exposed data comes not only from the application itself, but also API keys, database passwords, and AWS access keys. It may even allow potential attackers to access information on other IT infrastructures through Django applications.
https://twitter.com/6IX7ine/status/978598496658960384
“I found this as I was working with the Django framework on a small project,” Castro told Bleeping Computer, “I noticed some error exception and then went searching on Shodan.”
Castro added: “The main reason [for all the exposures] is the debug mode enabled,” Castro says. “This is not a failure from Django’s side. My recommendation is to disable debugging mode when deploying the application to production.”