Miteru v2.0.1 releases: An experimental phishing kit detection tool
Miteru
Miteru is an experimental phishing kit detection tool.
How it works
- It collects phishing suspicious URLs from the following feeds:
- It checks a suspicious URL whether it enables directory listing and contains a phishing kit (compressed file) or not.
- Note: compressed file = *.zip, *.rar, *.7z, *.tar and *.gz.
Features
- Phishing kit detection & collection.
- Slack integration. (Posting a message to Slack if the tool detects a phishing kit.)
- Threading.
Installation
$ gem install miteru
Using Docker (alternative if you don’t install Ruby)
$ git clone https://github.com/ninoseki/miteru.git $ cd miteru/docker $ docker build -t miteru . $ docker run miteru # ex. auto-download detected phishing kit(s) into host machines's /tmp directory $ docker run -v /tmp:/tmp miteru execute --auto-download
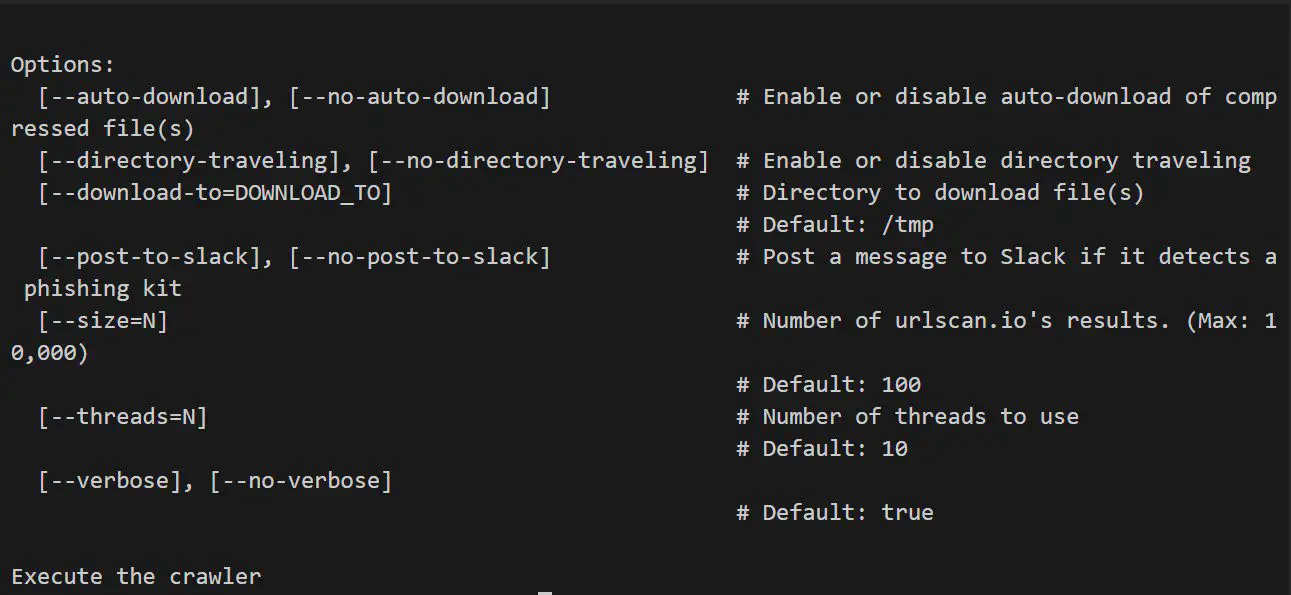
Usage

Note: Stoped the process during the execution because it takes minutes to finish.
Note
For using –post-to-slack feature, you should set the following environment variables:
- SLACK_WEBHOOK_URL: Your Slack Webhook URL.
- SLACK_CHANNEL: Slack channel to post a message (default: “#general”).
Copyright (c) 2018 Manabu Niseki
Source: https://github.com/ninoseki/