MITMsmtp v0.0.2 released: an Evil SMTP Server for pentesting SMTP clients
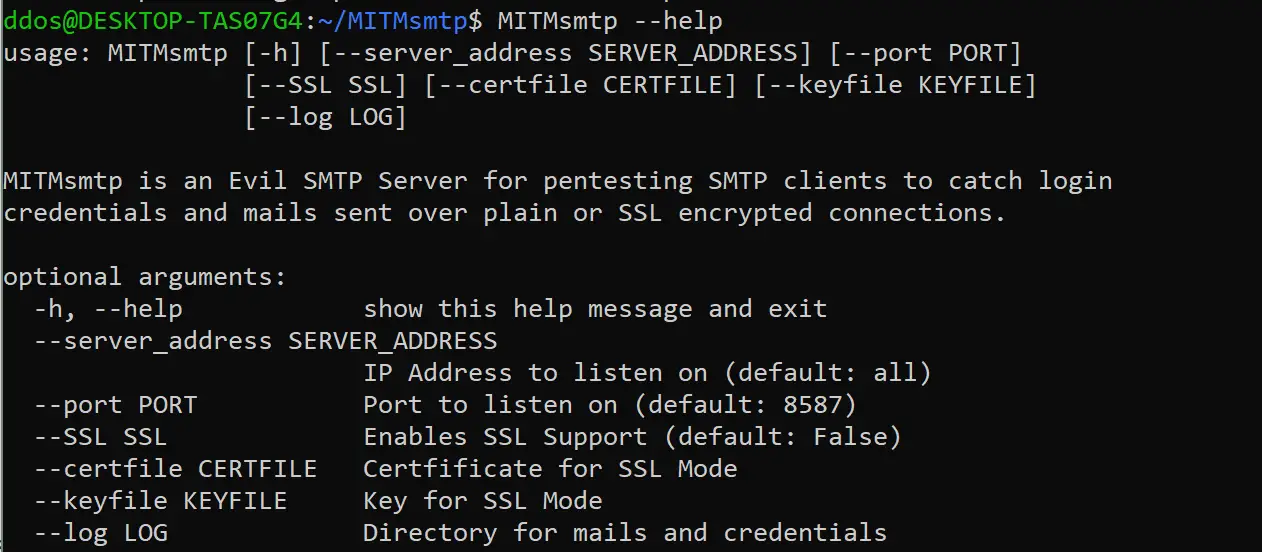
MITMsmtp
MITMsmtp is an Evil SMTP Server for pentesting SMTP clients to catch login credentials and mails sent over plain or SSL/TLS encrypted connections. The idea is to catch sensitive emails sent by clients which are not correctly verifying the SMTP servers identity in SSL/TLS mode. It will catch username and password as well as the message itself. This way you might gain access to a companies mail server or catch information like password reset tokens or verification links sent by applications. Using that information you might gain more and more access to a system. MITMsmtp has been built to work together with MITM Attacks like ARP Spoofing to terminate encrypted connections.

MITMsmtp offers a command line tool as well as an open Python3 API which can be used to build own tools for automated pentesting of applications.
Compatibility
MITMsmtp has been tested against the SMTP client of Thunderbird 60.5.3 and some other SMTP clients.
Connection Security
MITMsmtp supports the following connection security modes:
- Plaintext
- SSL/TLS
- STARTTLS (under development, not yet working)
Login Methods
MITMsmtp supports the following login methods:
- PLAIN
- LOGIN (under development, not yet working)
Other methods are not supported as we want to extract the cleartext password. As this might be a problem for restrictive clients, it is planned to add support for MD5 later. However, NTLM or Kerberos can’t be supported as these methods require the server to know the cleartext password.
Changelog v0.0.2
This release introduces STARTTLS support and flexible authentication plugins which can be easily loaded to allow custom attacks against clients
Download && Use
Copyright (C) 2019 RobinMeis





