mole: identifying and exploiting out-of-band (OOB) vulnerabilities
Mole
A framework for identifying and exploiting out-of-band application vulnerabilities.
Installation & Setup
Mole Install
Python >= 3.6
git clone https://github.com/ztgrace/mole.git
virtualenv -p /usr/bin/python3 venv
source venv/bin/activate
./venv/bin/pip3 install -r requirements.txt
git submodule update –init –recursive
Set an API key in config.yml (must be the same for the client and server)
DNS Configuration
You’ll need to configure the DNS records in your registrar to point to your mole server. Minimally, you’ll need an A record for the name server and an NS record configured.
Mole can be configured to host other configuration options.
Mailgun (Optional)
Mailgun requires DNS entries to enable the service.
TLS
Currently, Mole does not support TLS natively. To implement TLS, use a reverse proxy such as nginx to terminate the TLS connection and forward traffic to the Mole server.
Burp Suite Extension
The Burp Suite Extension requires a separate Python 2.7 virtual environment due to the latest version of Jython only supporting 2.7. Below are the instructions for setting up the virtual environment and configuring the Extension.
- Create a new python2.7 virtualenv for burp/jython, virtualenv -p /usr/bin/python2.7 burp_venv
- Load the venv, source ./burp_venv/bin/activate
- Install the required packages, ./burp_venv/bin/pip -r requirements
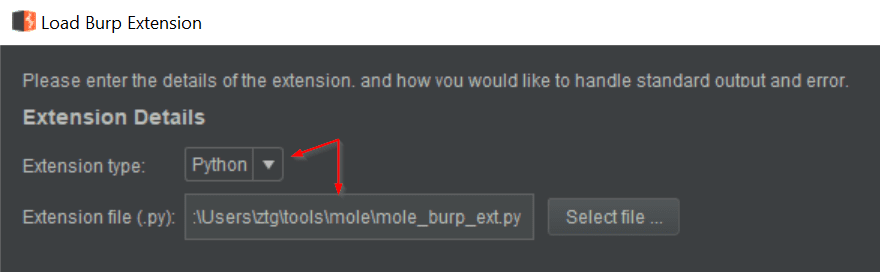
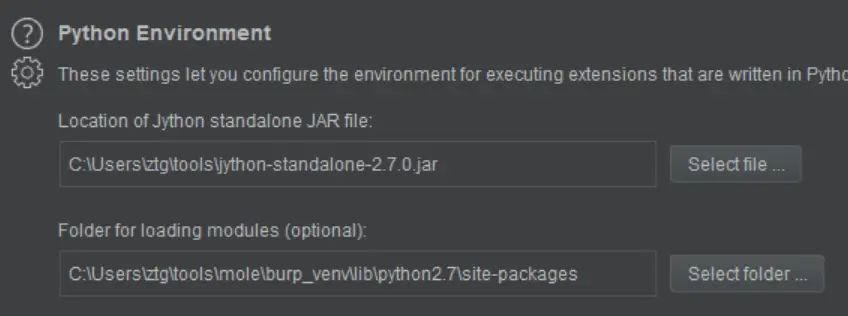
- Configure the Python Environment by downloading and selecting the jython-standalone jar.
- Set the “Folder for loading modules” to the full path to burp_venv/lib/python2.7/site-packages that was created in steps 1-3.

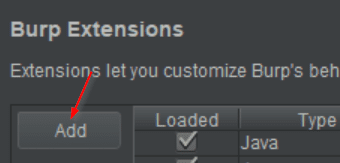
- Set the Extension type to Python and select the mole_burp_extension.py file from the mole project directory.

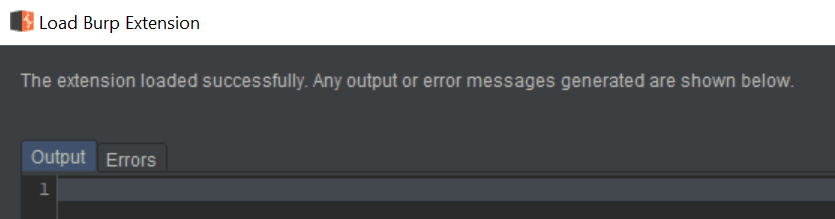
- Click Next and if all goes well, there will be no errors on the load screen.