
Malicious Apple ID login page (Source: urlscan)
A new campaign by the Roaming Mantis-affiliated MoqHao malware family, also known as Wroba and XLoader, has been uncovered by Threat Hunting Platform – Hunt.io. The campaign exploits trusted platforms such as Apple iCloud and Russian social media service VK to target both Android and iOS users, utilizing sophisticated phishing and malware delivery tactics.
The operation begins with a seemingly innocuous SMS, written in Japanese, claiming a failed delivery attempt and directing recipients to a shortened URL hosted on X/Twitter. Upon closer examination, the message shows signs of linguistic inconsistencies, hinting at its fraudulent nature. Clicking the link redirects users to phishing pages tailored to their device type, either mimicking the Apple ID login portal for iOS users or delivering malicious APK files for Android devices.
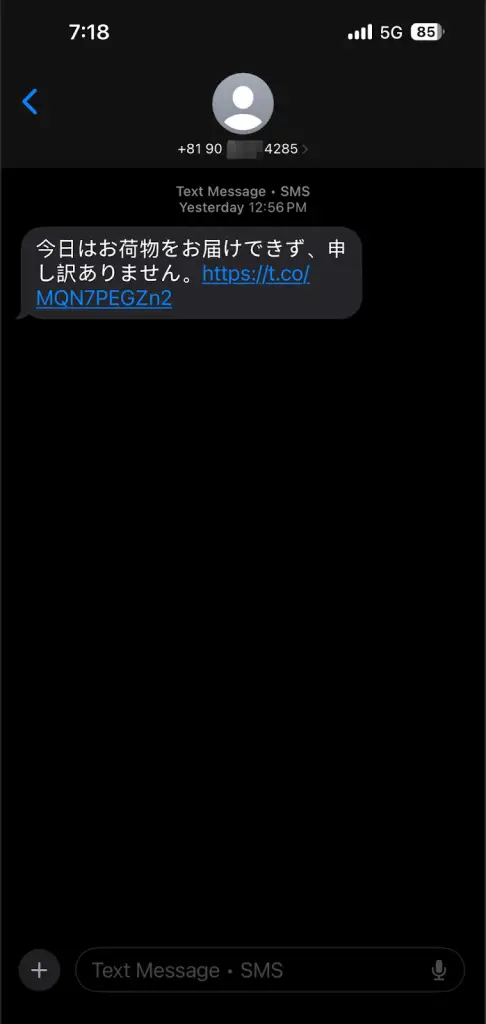
The attackers demonstrate a high level of sophistication in their infrastructure. When an iOS user accesses the link, they are directed to a localized phishing page with region-specific URLs. These fake Apple ID login pages are designed to harvest credentials by first rejecting the user’s initial password attempt, creating an illusion of legitimacy. For Android users, the campaign delivers a file named Chrome_up1732156036129.apk, masquerading as a Google Chrome update. This APK, flagged by multiple vendors on VirusTotal, downloads directly from Apple’s legitimate iCloud infrastructure, which the attackers have abused for hosting malware.
To further obfuscate their operations, the operators rely on dynamic DNS services like DuckDNS and intermediary platforms like VK. The command-and-control (C2) address is encoded within a VK user profile, serving as an intermediary to conceal the true location of the C2 server. This multilayered approach, using both trusted platforms and disposable domains, makes detection and attribution significantly more challenging.
MoqHao’s operators have adapted their techniques to evade security measures. From using Apple’s iCloud for malware distribution to leveraging VK for C2 communication, they exemplify the increasing sophistication of cybercriminal campaigns. By employing multiple hosting providers and dynamic DNS subdomains, they ensure the resilience of their infrastructure even if specific domains are flagged or taken down.
By combining traditional smishing tactics with advanced malware delivery mechanisms and leveraging trusted platforms, these attacks underline the importance of proactive security measures. As Hunt.io states, “Their ability to target Android and iOS users with tailored methods underscores the importance of vigilance when handling unsolicited messages.”
Related Posts:
- Google Advanced Protection Program now supports iOS applications
- Apple Confirmed that All Mac and iOS Devices Are Affected by Chip Vulnerability
- Hackers attack MetaMask users via phishing and steal $655,000