More Flaws, Fewer Frightmares: 2023 Cybersecurity – A Tale of Exploitable Echoes
As we approach the end of 2023, it’s crucial to reflect on the cyber threats that have shaped our digital world. This year has been a rollercoaster in the realm of cybersecurity, with significant developments that have both challenged and advanced our understanding of digital threats. The Qualys Threat Research Unit‘s comprehensive analysis provides us with key insights into this year’s cyber threat landscape.
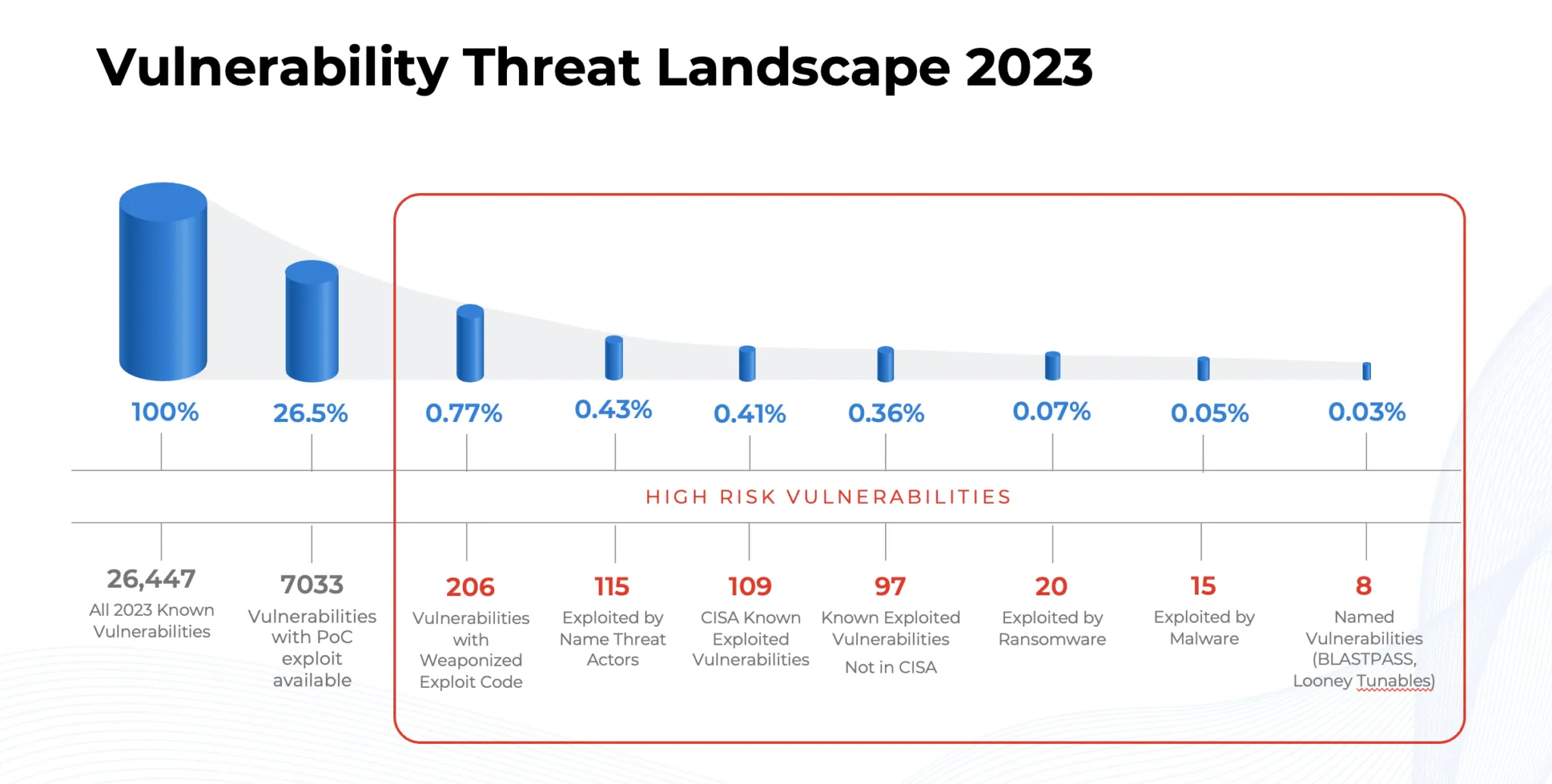
A staggering 26,447 vulnerabilities were disclosed in 2023, surpassing 2022’s total by over 1,500 CVEs. This increase continues a years-long trend of escalating vulnerability disclosures. However, it’s not the quantity but the quality of these vulnerabilities that poses the greatest risk. A mere 1% of these vulnerabilities contributed the highest risk and were actively exploited in the wild.
One of the most alarming revelations of 2023 was the discovery that 97 high-risk vulnerabilities, ripe for exploitation, were not included in the CISA Known Exploited Vulnerabilities catalog. This oversight highlights the ever-evolving nature of cyber threats and the need for constant vigilance.

Image Credit: Qualys
In 2023, the cyber battlefield witnessed a drastic reduction in response times. Attackers increasingly capitalized on vulnerabilities immediately, with some exploits being published the same day the vulnerabilities were disclosed. This trend emphasizes the need for organizations to adopt a proactive stance toward patch management and threat intelligence.
Ransomware continued to be a dominant force in 2023, with groups like LockBit and Cerber exploiting 20 vulnerabilities. Additionally, 15 vulnerabilities were targeted by malware and botnet groups. This underscores the urgent need for robust cybersecurity measures in the face of these sophisticated threats.
The 2023 threat landscape highlighted the necessity of a comprehensive vulnerability management strategy. Over a third of the high-risk vulnerabilities identified could be exploited remotely, making it critical for organizations to employ a variety of vulnerability management methods, including agent-based, agent-less, and network-based techniques.
A significant 32.5% of high-risk vulnerabilities were found in networking infrastructure and web applications, challenging traditional security measures. This calls for a diversified approach to cybersecurity, encompassing various detection and remediation techniques.
The most exploited vulnerabilities of 2023 include CVE-2023-0669 and CVE-2023-20887, among others. These vulnerabilities span a wide array of systems and applications, demonstrating that no platform is immune to cyberattacks.
Attackers in 2023 employed a range of sophisticated techniques, including exploitation of remote services, public-facing applications, and privilege escalation. This variety in attack methods paints a picture of a sophisticated and multifaceted threat landscape.
The 2023 threat landscape has been a stark reminder of the dynamic nature of cyber threats. The rapid evolution from vulnerability disclosure to exploitation underscores the critical need for organizations to closely monitor disclosures and implement rapid response mechanisms. As we move forward, we must learn from the lessons of 2023 to bolster our defenses against the ever-changing cyber threats that lie ahead.





