Image: Morphisec
In the ever-shifting landscape of cyber threats, a new player has emerged: Chae$ 4.1. This updated version of the Chaes malware infostealer series, analyzed by Morphisec Advanced Research Center, demonstrates a significant leap in cybercriminal ingenuity.
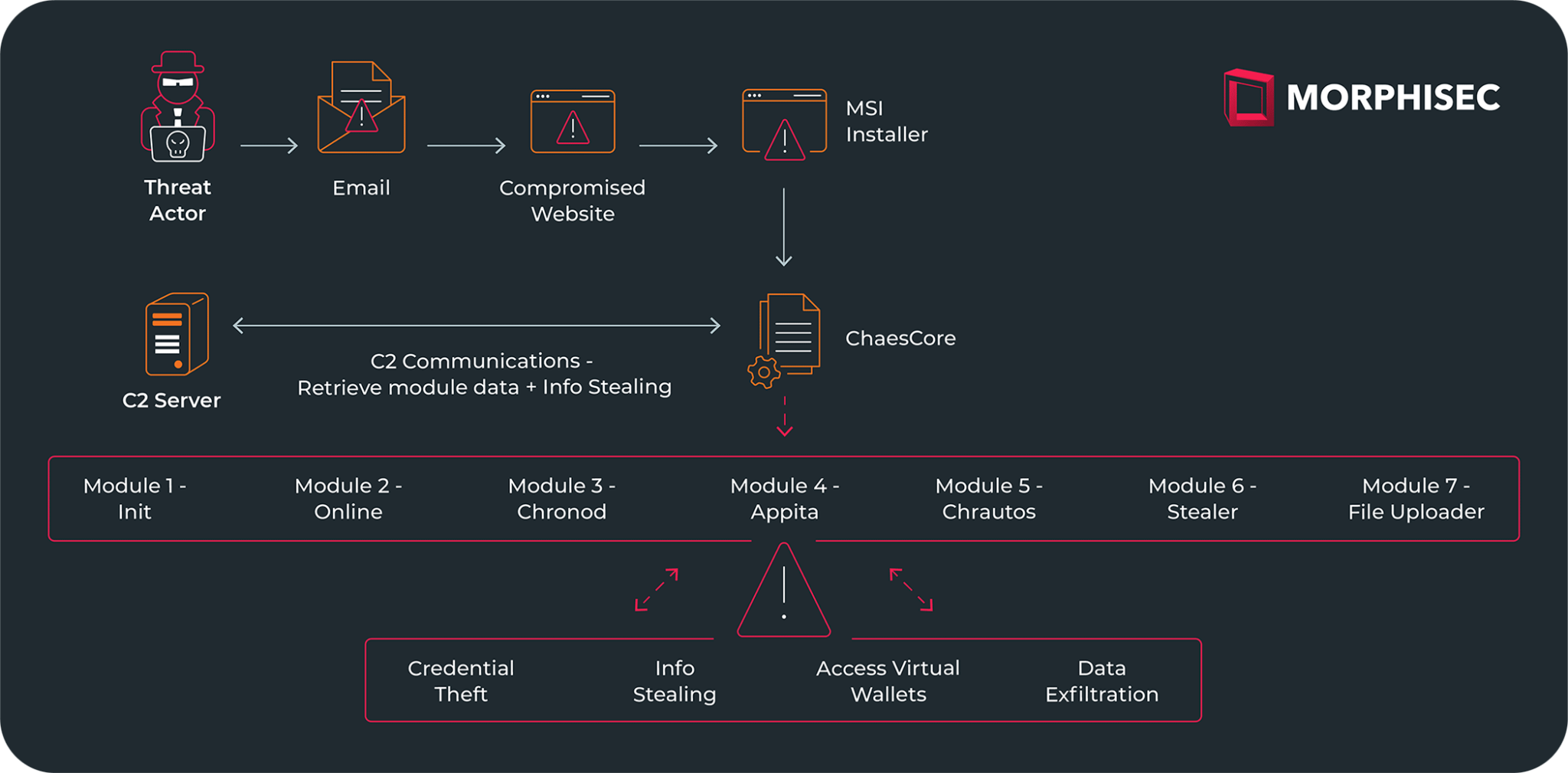
Chae$ 4.1 employs a complex infection chain, starting with an email that lures victims to download a ZIP file containing a malicious MSI installer. This campaign is multilingual, with emails written in languages like Portuguese, indicating a broad target base.
“Within the ZIP archive, there is an LNK file. Clicking this file initiates the execution of msiexec.exe, facilitating the remote download and execution of the next stage payload in silent mode with no user interface,” reads the report.

The core of Chae$ 4.1’s sophistication lies in its Chronod module. This module has been overhauled to become more modular and generic, capable of intercepting browser activity to steal critical information such as login credentials and banking details from a variety of services.
“The Chronod module is responsible for intercepting browser activity to steal information from the victim such as credentials sent on a login process, banking information when communicating with the bank’s website, and has a clipping functionality,” the report continues.
Chae$ 4.1 malware exhibits advanced capabilities in stealth and data exfiltration. It uses deceptive websites and compromised WordPress sites to distribute its payload, showcasing the attackers’ adaptability and persistence.
Interestingly, Chae$ 4.1’s source code contains a direct message to the Morphisec team, a rare instance of cybercriminals acknowledging their adversaries.
The emergence of Chae$ 4.1 malware marks a significant development in the world of cyber threats. With its advanced techniques and multifaceted attack strategies, it represents a new level of challenge for cybersecurity professionals and emphasizes the need for continuous vigilance and innovation in cybersecurity defenses.