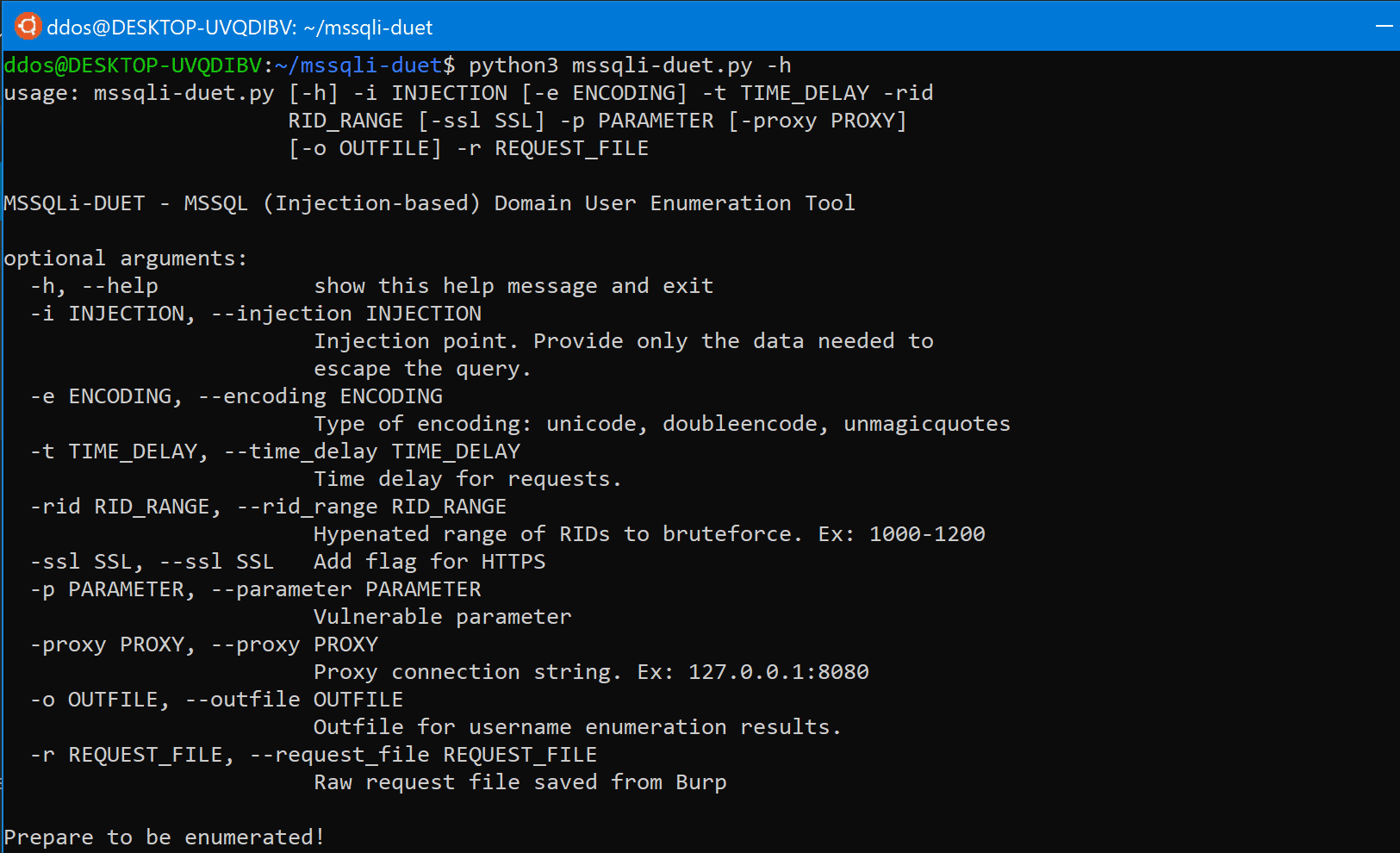
MSSQLi-DUET – MSSQL Injection-based Domain User Enumeration Tool
SQL injection script for MSSQL that extracts domain users from an Active Directory environment based on RID bruteforcing. Supports various forms of WAF bypass techniques through the implementation of SQLmap tamper functions. Additional tamper functions can be incorporated by the user depending on the situation and environment.
Currently only supports union-based injection. Planning to add other techniques later. More samples and test cases are required to fully test tool’s functionality, feedback and comments are greatly welcomed and appreciated!
Download
git clone https://github.com/Keramas/mssqli-duet.git
Use
After identifying a union-based SQL injection in an application, copy the raw request from Burp Suite using the ‘copy to file’ feature.
Pass the saved request to DUET with the -r flag. Specify the vulnerable parameter and well as the point of injection. As an example, if the parameter “element” is susceptible to SQL injection, -p will be “element”. DUET will build out all the SQL injection queries automatically, but specification for the initial injection needs to be provided. Meaning, if the injection occurs because of a single apostrophe after the parameter data, this is what would be specified for the -i argument.
Example
Source: https://github.com/Keramas/