mushikago
Mushikago is an automatic penetration testing tool using game AI, which focuses on the verification of post-exploit among penetration testing tools.
Features
- Full Automatic penetration testing tool
- Device detection
- IT penetration testing
- ICS penetration testing
Abstract
Mushikago uses game AI technology to select and execute the most appropriate test content based on the environment in the spot. The application of game AI technology to security products is new, and our work has shown that game AI is most suitable for penetration testing, where the content needs to change depending on the environment. In addition, Mushikago can automatically perform penetration testing in mixed environments of IT and OT(ICS), and can visualize and report the acquired device, account, and network information. The test contents are also displayed in a format consistent with MITRE ATT&CK. This allows the user to perform penetration testing at a certain level without manual intervention.
Contents of Penetration testing
- Collecting device information
- OS
- NIC vendor
- Open TCP/IP port
- Collecting User account detection
- Local user account
- Local user account password & hash
- Domain user account
- Domain user account password & hash
- Collecting Network information
- IP address information assigned to the NIC
- Established network
- Collecting Network drive
- Capturing Network
- Save as pcap file
- Collecting Secret file
- Pre-designated file (mushikago.txt)
- Collecting Process list
- Collecting Security product process
- AntiVurus Software
- Panda
- Kaspersky
- Tanium
- AVG/AVAST
- SEP (Symantec Endpoint Protection)
- Windows Defender
- McAfee
- Sophos
- Malwarebytes
- EDR (Endpoint Detection & Response)
- Carbon Black
- CrowdStrike
- FireEye
- ESET
- F-Secure
- AntiVurus Software
- Post-exploitation
- Lateral Movement
- Exploiting vulnerability
- SMB
- wmic
- Lateral Movement
- ICS detection
- ICS Protocol identify
- ICS vendor identify
Download
git clone https://github.com/PowderKegTech/mushikago.git
Use
step 1. Launch Metasploit API
# ./msfrpc.sh
step 2-(a). Mushikago execution (Target system is IT)
# python3 main goap/actions-it.json
step 2-(b). Mushikago execution (Target system is OT)
# python3 main goap/actions-ics.json
step 3. Lanch the dashboard
# npm run dev
step 4. Check of nodes.json
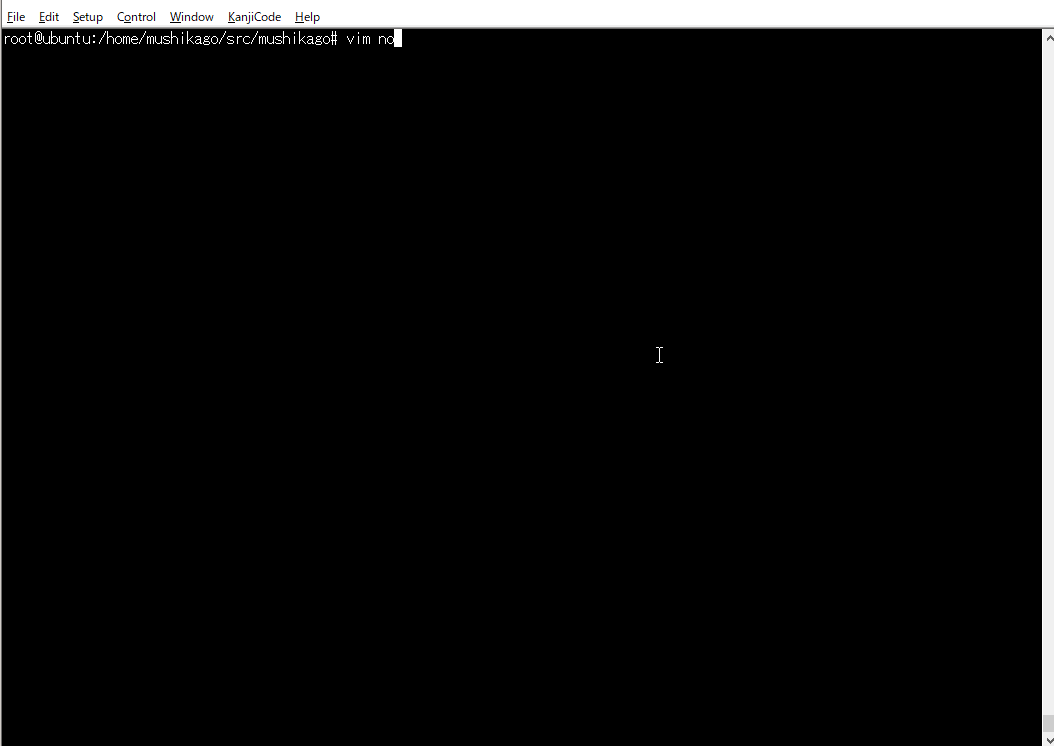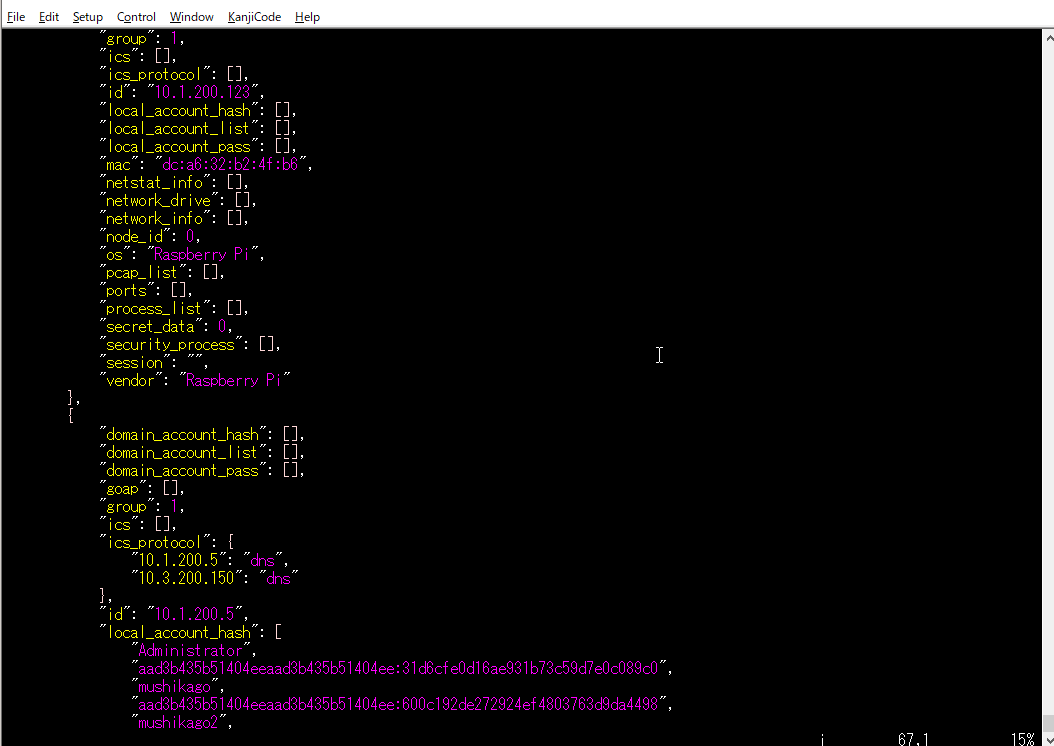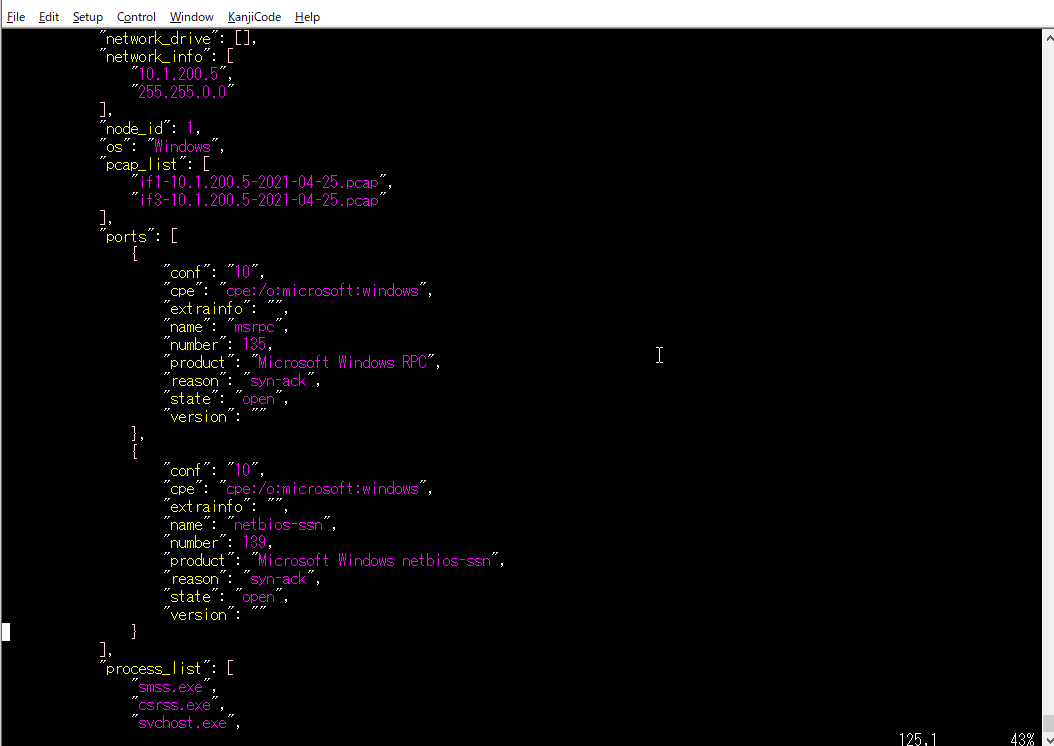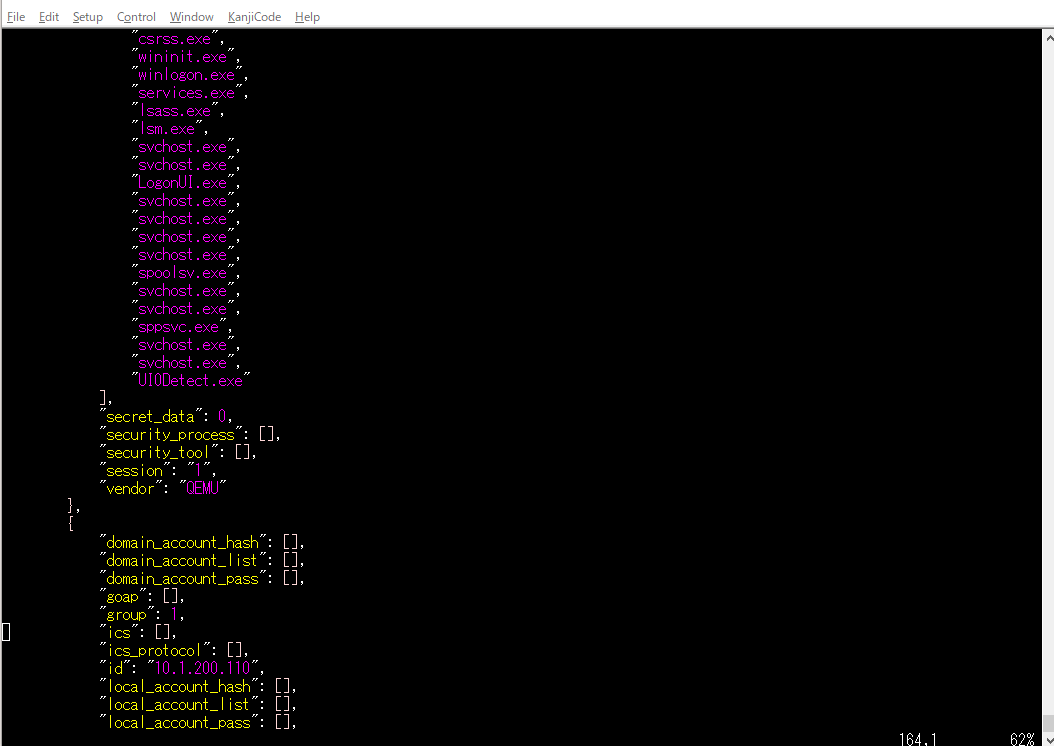
ex) # vim nodes.json
The information collected by the penetration testing is stored in nodes.json.
step 5. Check dashboard
access to the next url.
http://localhost:9529/
We can check the penetration test information from the dashboard.
- Network Overview
- Device list
- acquired data list
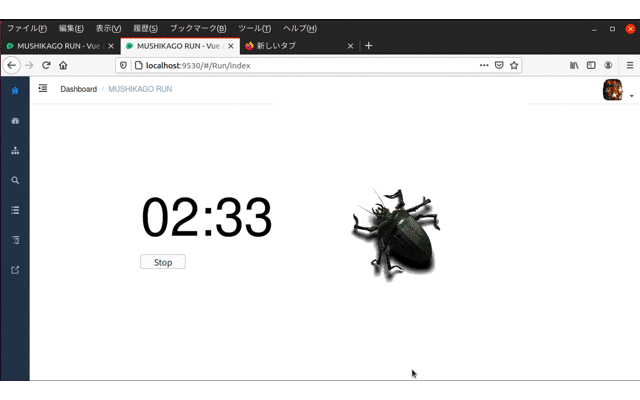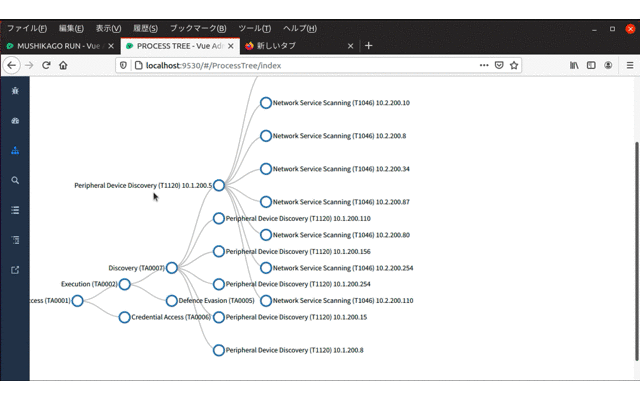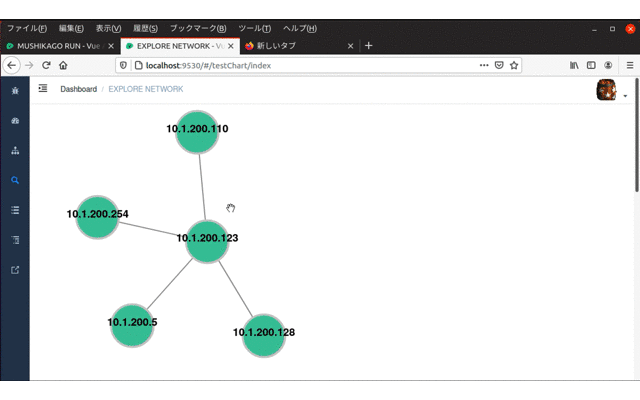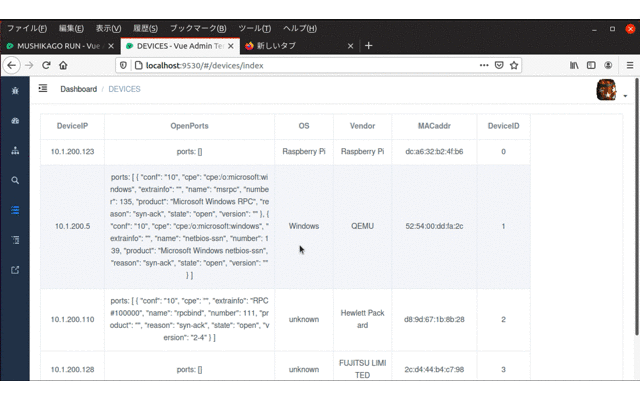
- Penetration testing process tree (Display along MITRE ATT&CK)
Acknowledgment: This code was created for personal use with hosts you able to hack/explore by any of the known bug bounty programs. Use it at your own risk.
Copyright 2021 Powder Keg Technologies
Source: https://github.com/PowderKegTech/