naabu v2.1.9 releases: fast port scanner written in go
naabu
naabu is a fast port scanner tool written in Go that allows you to enumerate valid ports for hosts in a fast and reliable manner. It is a really simple tool that does fast SYN scans on the host/list of hosts and lists all ports that return a reply.
Features
- Simple and modular codebase making it easy to contribute.
- Fast And Simple SYN probe-based scanning.
- Multiple Output formats supported (Json, File, Stdout)
- Optimized for ease of use and lightweight on resources
- Stdin and stdout support for integrating into workflows
- Flexible definitions for ports to scan
Changelog v2.1.9
🐞 Bugs Fixes
- Added support for hostnames with
-ehoption by @Mzack9999 in #823
Other Changes
Use
To run the tool on a target, just use the following command.
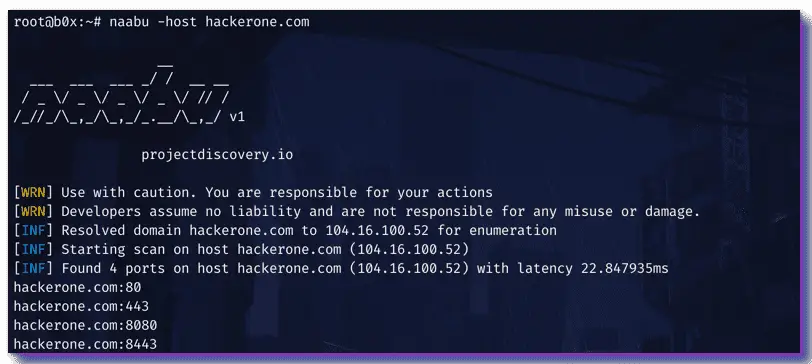
> naabu -host hackerone.com
This will run the tool against hackerone.com. There are a number of configuration options that you can pass along with this command. The verbose switch (-v) can be used to display verbose information.
[INF] Starting scan on host hackerone.com (104.16.100.52)
[INF] Found 4 ports on host hackerone.com (104.16.100.52) with latency 25.46362ms
hackerone.com:443
hackerone.com:8443
hackerone.com:80
hackerone.com:8080
The ports to scan for on the host can be specified via -ports parameter. It takes nmap format ports and runs enumeration on them.
> naabu -ports 80,443,21-23 -host hackerone.com
By default, the tool checks for nmap’sTop 100 ports. It supports following in-built port lists –
- top-100 – Checks for nmap top 100 ports.
- top-1000 – Checks for nmap top 1000 ports.
- full – Checks for 1-65535 ports.
You can also specify a file which contains the ports to scan for using the pL format. You can also specify specific ports which you would like to exclude from the scan.
> naabu -ports full -exclude-ports 80,443
The -o command can be used to specify an output file.
> naabu -host hackerone.com -o output.txt
To run the tool on a list of hosts, -hL option can be used. This requires a directory to write the output files. Ports for each host from the list are written in a text file in the directory specified by the -oD flag with their name being the hostname.
> cat hosts.txt
hackerone.com
google.com
> naabu -hL hosts.txt -oD ~/path/to/output
> ls ~/path/to/output
hackerone.com.txt
google.com.txt
If you want to save results to a single file while using a domain list, specify the -o flag with the name of the output file.
> cat hosts.txt
hackerone.com
google.com
> naabu -hL hosts.txt -o ~/path/to/output.txt
> ls ~/path/to/
output.txt
You can also get output in json format using -oJ switch. This switch saves the output in the JSON lines format.
> naabu -host hackerone.com -oJ -o output.json
> cat output.json
{“host”:”hackerone.com”,”port”:8443}
{“host”:”hackerone.com”,”port”:443}
{“host”:”hackerone.com”,”port”:8080}
{“host”:”hackerone.com”,”port”:80}
The -silent switch can be used to show only ports found without any other info.
Hosts can also be piped to naabu and port enumeration can be run on them. For example –
> echo “hackerone.com” | naabu
> cat targets.txt | naabu
The ports discovered can be piped to other tools too. For example, you can pipe the ports discovered by naabu to the awesome httprobe tool by @tomnomnom which will then find running http servers on the host.
> echo “hackerone.com” | naabu -silent | httprobe
http://hackerone.com:8443
http://hackerone.com:443
http://hackerone.com:8080
http://hackerone.com:80
If you want a second layer validation of the ports found, you can instruct the tool to make a TCP connection for every port and verify if the connection succeeded. This method is very slow but is really reliable. This is similar to using nmap as a second layer validation
> naabu -host hackerone.com -verify
The most optimal setting for threads is 10. Increasing it while processing hosts may lead to increased false positive rates. So it is recommended to keep it low.
Install
Copyright (C) 2020 Ice3man543





