Covenant v0.6 releases: a .NET command and control framework
Covenant
Covenant is a .NET command and control framework that aims to highlight the attack surface of .NET, make the use of offensive .NET tradecraft easier, and serve as a collaborative command and control platform for red teamers.

Covenant is an ASP.NET Core, cross-platform application that includes a robust API to enable a client-server architecture that allows for multi-user collaboration. There are three main components of Covenant’s architecture:
- Covenant – Covenant is the server-side component of the client-server architecture. Covenant runs the command and control server hosted on infrastructure shared between operators. I will also frequently use the term “Covenant” to refer to the entire overarching project that includes all components of the architecture.
- Elite – Elite is the client-side component of the client-server architecture. Elite is a command-line interface that operators use to interact with the Covenant server to conduct operations.
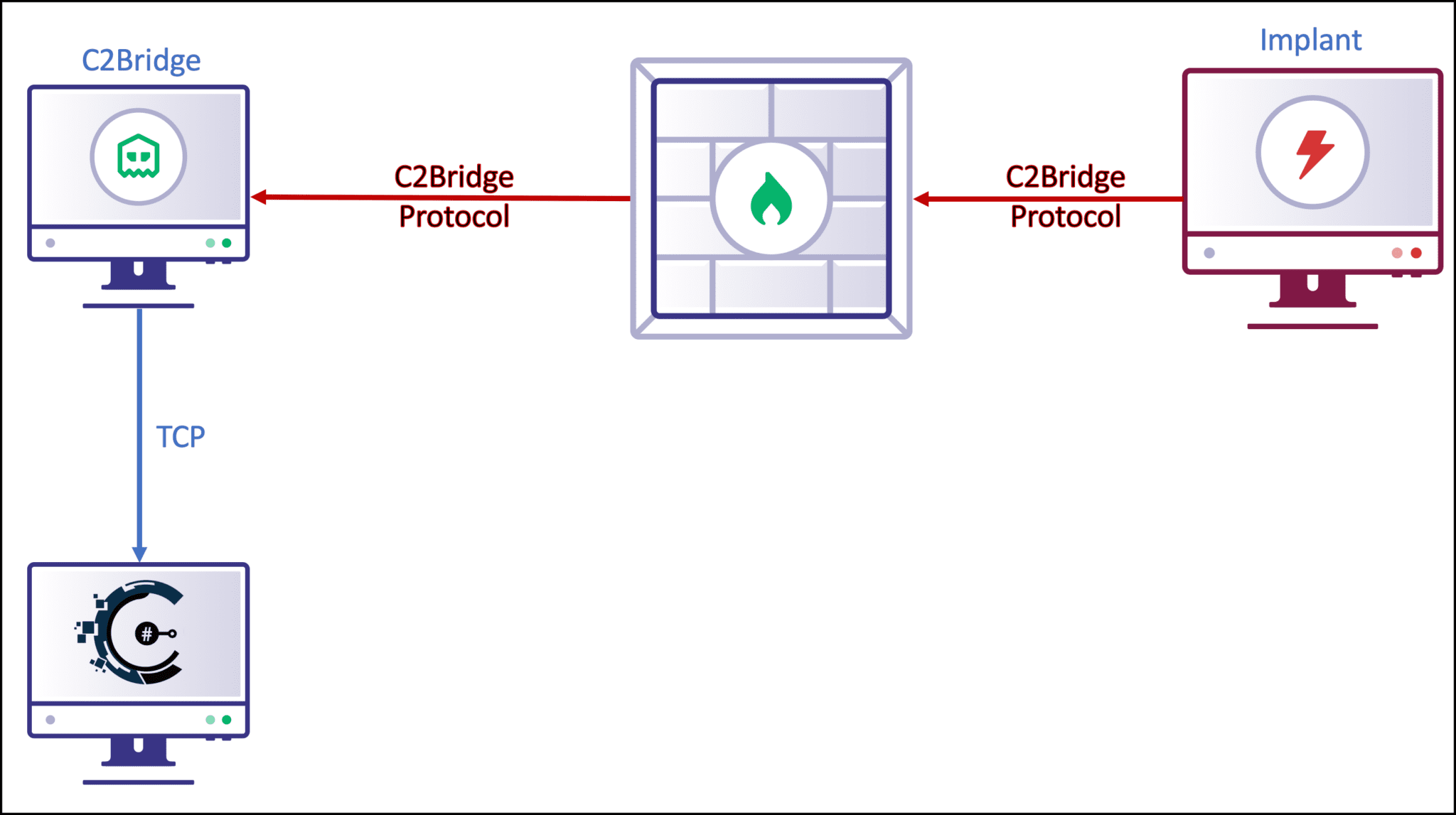
- Grunt – A “Grunt” is the name of Covenant’s implant that is deployed to targets.
Features
Covenant has several key features:
- Multi-Platform – Covenant and Elite both target .NET Core, which makes them multi-platform. This allows these programs to run natively on Linux, MacOS, and Windows platforms. Additionally, both Covenant and Elite have docker support, allowing these programs to run within a container on any system that has docker installed.
- Multi-User – Covenant supports multi-user collaboration. The ability to collaborate has become crucial for effective red team operations. Many users can start Elite clients that connect to the same Covenant server and operate independently or collaboratively.
- API Driven – Covenant is driven by a server-side API that enables multi-user collaboration and is easily extendible. Additionally, Covenant includes a Swagger UI that makes development and debugging easier and more convenient.
- Listener Profiles – Covenant supports listener “profiles” that control how the network communication between Grunt implants and Covenant listeners look on the wire.
- Encrypted Key Exchange – Covenant implements an encrypted key exchange between Grunt implants and Covenant listeners that is largely based on a similar exchange in the Empire project, in addition to optional SSL encryption. This achieves the cryptographic property of forwarding secrecy between Grunt implants.
- Dynamic Compilation – Covenant uses the Roslyn API for dynamic C# compilation. Every time a new Grunt is generated or a new task is assigned, the relevant code is recompiled and obfuscated with ConfuserEx, avoiding totally static payloads. Covenant reuses much of the compilation code from the SharpGen project, which I described in much more detail in a previous post.
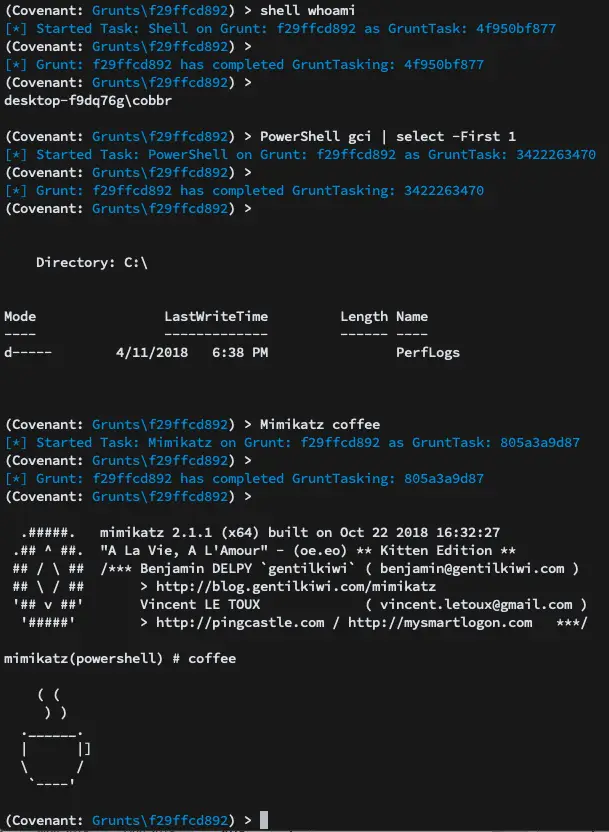
- Inline C# Execution – Covenant borrows code and ideas from both the SharpGen and SharpShell projects to allow operators to execute C# one-liners on Grunt implants. This allows for similar functionality to that described in the SharpShell post but allows the one-liners to be executed on remote implants.
- Tracking Indicators – Covenant tracks “indicators” throughout the operation, and summarizes them in the Indicators menu. This allows an operator to conduct actions that are tracked throughout an operation and easily summarize those actions to the blue team during or at the end of an assessment for deconfliction and educational purposes. This feature is still in its infancy and still has room for improvement.
Changelog
[v0.6] – 2020-08-04
Added
- Added CreateDirectory task
- Add SharpSC submodule, ReferenceSourceLibrary, and GruntTask
- Added CreateProcessWithToken task
- Added aliases for Shell tasks
- Added ShellCodeLauncher using Donut
- Added Copy command
- Added missing Keylogger task
- Added streaming task output
- Added Download/Upload .NET Core Tasks
- Added ReadTextFile,CreateDirectory,Delete .NET Core Tasks
- Added UI Themes, new Heathen Mode theme
- Added a TabbedTerminal view to GruntIndex component
- Added message that Covenant has started
Changed
- Add SharpSploit.LateralMovement namespace to SharpShell command
- Updated PowerShellRemoting tasks to show output
- Update implants to use WellKnownSidType enum rather than string for non-english systems
- Update all launchers to support non-http profiles
- Changed Shell tasks to use CreateProcess to get output
- Updated SharpSploit, Rubeus, Seatbelt ReferenceSourceLibaries to latest versions
- Simplified compilation optimization to use HashSet
- Limited compilation optimization for SharpSC
- Updated Seatbelt to latest version
- Updated SharpSploit to latest version, PowerShell task should include verbose/error output
- Changed GruntTask export to exclude GruntTaskOption value property
- Updated codemirror, added night theme for codemirror
- Removed Covenant certificate hash message
Fixed
- Fixed order of Upload parameters
- Fixed Brute compilation path for case-sensitive file systems
- Fixed HttpPost issue on Linux servers
- Fixed Listeners stop issue
- Fixed Seatbelt command group suggestions
- Fixed EditGruntTask for task with aliases, validationmessage issue
- Fixed Task aliases to be able to be edited
- Fixed InstallUtil launcher
- Fixed PowerShellLauncher maxlength too short
- Fixed BridgeListener null exception on creation
- Fixed Dockerfile to use sdk for runtime
- Fixed ordering of deserialized GruntTask Options
- Fixed Assembly tasks to do command-line style parsing
- Updated YAML task file code options to use literal strings, may have been causing some problems
- Fixed parameter parsing bug when multiple trailing double-quotes
- Fixed command parameter parsing bug when multiple trailing double-quotes
- Fixed command parameter parsing bug when labeled parameter
- Fixed CovenantUser default properties set to null, not following OpenApi spec
- Fixed task aliases use incorrect case comparisons
- Fixed LauncherForm exception when no active listeners
- Fixed missing ReferenceAssemblies for SharpSploit
- Fixed WMICommand/WMIGrunt output format
- Fixed ConnectAttempts bug
- Fixed BridgeListener ArgumentOutOfRangeException
- Fix/tweak Connect/Disconnect tasks
- Fixed JwtKey issue
- Fixed ImplantTemplateForm options resetting issue
- Fixed terminal typeahead issues
- Fixed HttpProfile editing issue
- Fixed POST /api/users API endpoint authentication issue
- Fixed profiles using Cookie header
- Fixed profile using curly brace character
- Fix create/edit for ReferenceSourceLibraries,ReferenceAssemblies,EmbeddedResources
- Fix launcher commands (i.e. BypassUacGrunt, WMIGrunt, PowerShellRemotingGrunt)
- Fix Launcher properties not being applied during generation
- Fixed Graph with BridgeListener issue
Download && Use
Copyright (C) 2019 cobbr