pown-recon v2.176 releases: A powerful target reconnaissance framework
Pown Recon
Pown Recon is a target reconnaissance framework powered by graph theory. The benefit of using graph theory instead of flat table representation is that it is easier to find the relationships between different types of information which comes quite handy in many situations. Graph theory algorithms also help with diffing, searching, like finding the shortest path, and many more interesting tasks.
Quickstart
If installed globally as part of Pown.js invoke like this:
$ pown recon
Otherwise, install this module from the root of your project:
$ git clone https://github.com/pownjs/pown-recon.git
$ npm install @pown/recon --save
Once done, invoke pown recon like this:
$ ./node_modules/.bin/pown-cli recon
Usage
pown-cli recon [options] <command>
Target recon
Commands:
pown-cli recon transform <transform> Perform inline transformation
[aliases: t]
pown-cli recon select <expression> Perform a selection [aliases: s]
pown-cli recon diff <fileA> <fileB> Perform a diff between two recon files
[aliases: d]Options:
–version Show version number [boolean]
–modules, -m Load modules [string]
–help Show help [boolean]
Transforms
- GitHub Search of Repos, Gists and Members
- Bitbucket Search of Repos, Snippets and Members
- CloudFlare 1.1.1.1 DNS API
- CRTSH (CN & SAN)
- DockerHub Repo Search
- Gravatar URLs
- Hacker Target Reverse IP Lookup
- Have I Been Pwned Lookup
- PKS Lookup
- Bufferover.run
- Urlscan Live Shot
- Threatcrowd Lookup
- Wappalyzer
- AWS IAM Pages
- Builtwith
- Riddler
- CommonCraw
- Archive.org
- Shodan
- WhatsMyName
- Utility Transforms
- Security Trails
- Auto Recon
Tutorial
To demonstrate the power of Pown Recon and graph-based OSINT (Open Source Intelligence), let’s have a look at the following trivial example.
Let’s start by querying everyone who is a member of Google’s engineering team and contributes to their GitHub account.
pown recon t -w google.network ghlm google
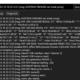
This command will generate a table similar to this:
You just created your first network!
The representation is tabular for convenience but underneath we’ve got a model which consists of nodes connected by edges.
If you are wondering what that looks like you can use SecApps Recon. The command line does not have the necessary level of interactivity to present the complexity of graphs.
The -w google.network command-line option exported the network to a file. You can load the file directly into SecApps Recon with the file open feature. The result will look like this:
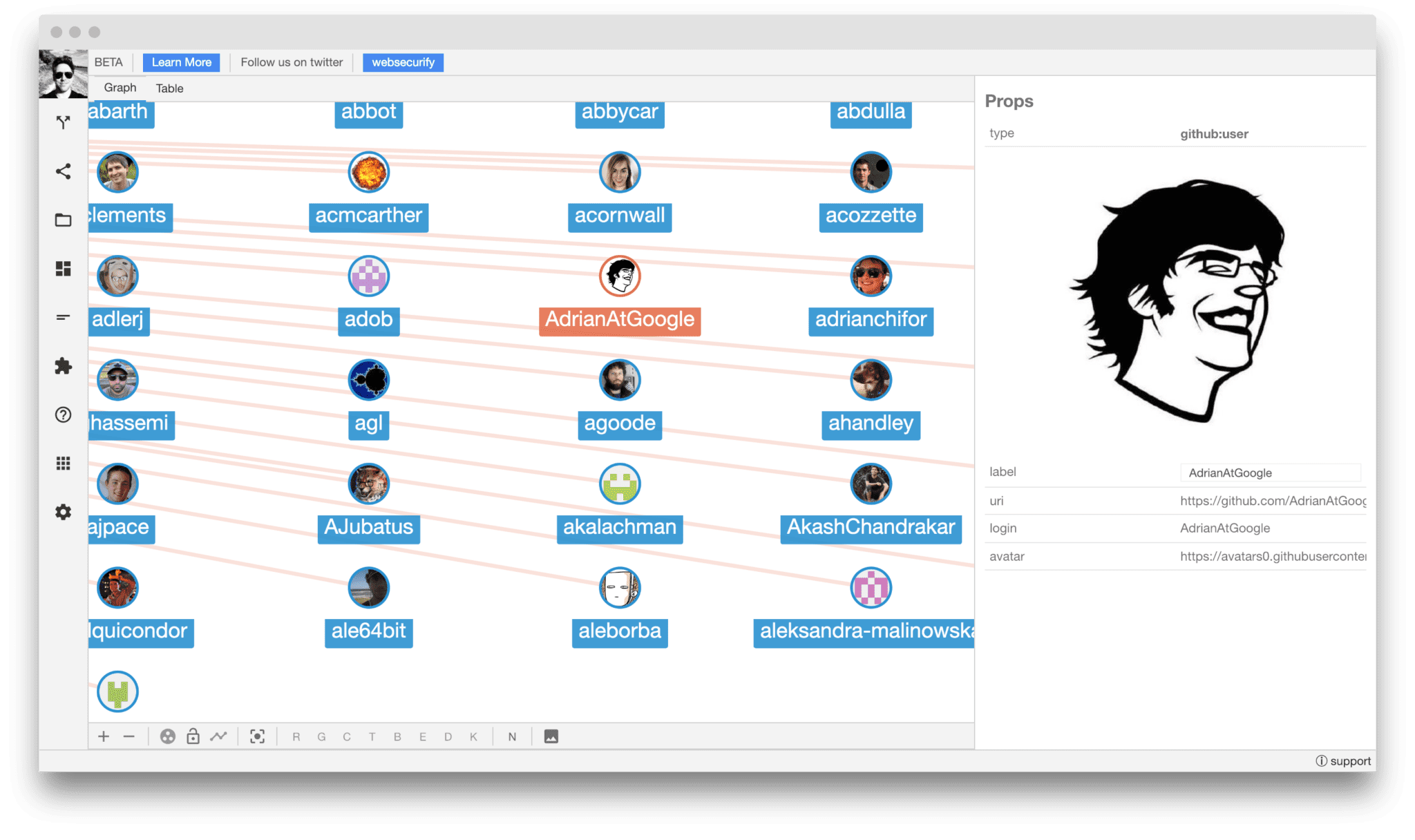
More…
Copyright (c) 2018 pownjs