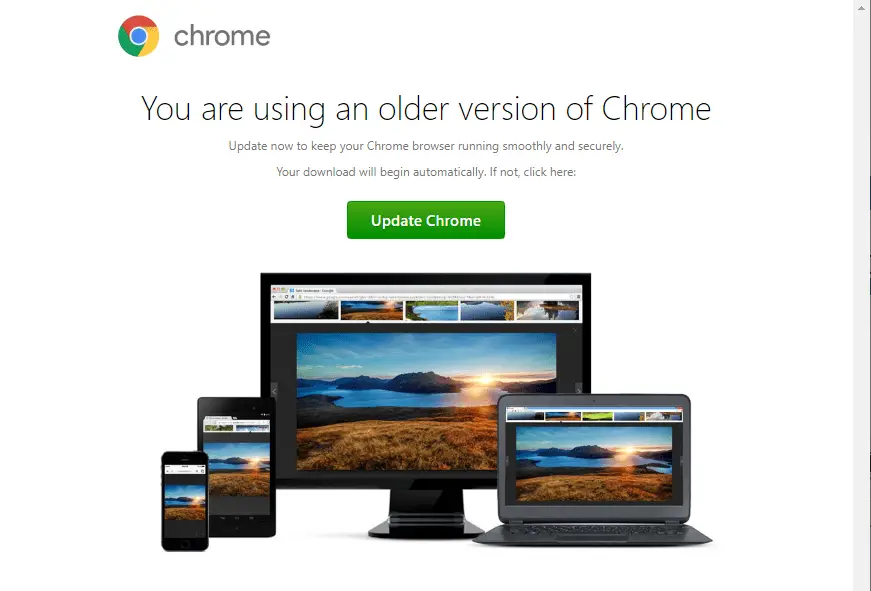
Fake chrome browser update presented to victim
Experts from VMware Carbon Black are sounding the alarm: there has been a recent uptick in cyber attacks targeting the educational sector, government institutions, and service industry enterprises. The primary weapon of these malefactors has become the NetSupport RAT, a Trojan for remote access.
According to researchers, hackers are employing a multitude of methods to disseminate this malicious software: from fake updates and automatic downloads while browsing websites to malicious loaders like GHOSTPULSE and phishing campaigns. In the past few weeks alone, there have been no fewer than 15 instances of NetSupport RAT infections detected.

It’s noteworthy that NetSupport Manager was once a legitimate tool for remote administration. However, fraudsters have adapted it for nefarious purposes.
NetSupport RAT most commonly infiltrates a victim’s system through deceptive websites and bogus browser updates. In August 2022, Sucuri unveiled details of a campaign in which hackers exploited compromised WordPress sites. The program was disguised as Cloudflare DDoS protection pages.
For the fake updates, a specialized JavaScript software known as SocGholish (or FakeUpdates) is used. This program acts as a loader — installing additional malicious modules on the infected device.
The malicious JavaScript code is activated immediately after the “update” is installed. It, in turn, triggers the system utility PowerShell, which downloads the main virus. NetSupport RAT then covertly connects with a command server to receive instructions.